The average tenure of a Chief Information Security Officer said to sit between 18 to 24 months. This is barely enough time to get feet under the table, never mind a meaningful seat at the table. Two questions arise: why is there such volatile churn in this space; and how does it affect enterprise cybersecurity?
Cause #1: the scapegoat effect
The potential for CISOs to be used as scapegoats for security incidents is widely accepted and potentially growing.
It can simply be internal: ‘We got breached under your watch, so we’ll blame you and let you go.’ But it can equally be a complex external issue ultimately caused by a lack of legal clarity in the Computer Fraud and Misuse Act (CFAA), a lack of clarity on bounty hunting and security research, and regulatory pressure for security professionals to protect personal information.
The Joe Sullivan dismissal by Uber and prosecution by government is a case in point. (Many of the following details are abstracted from a DefCon talk he gave in August 2023.)
Sullivan was on vacation at the time he was dismissed as CISO at Uber. He learned about it through third parties. Media coverage, he said, reported “I was fired for covering stuff up and that I had paid money to people to delete data.” That is a wildly simplistic view of what happened.
Sullivan had himself been a prosecutor before entering the private cybersecurity sector. His journey through companies like eBay, PayPal, Facebook, and Uber led him to conclude that researchers are a resource to be harnessed and ideally paid rather than prosecuted, but complicated by the likelihood that at some point they will most likely have breached the CFAA.
At Uber, he received an email saying that researchers/hackers/felons (depending on your point of view) had found a major vulnerability allowing them to dump the Uber database. Sullivan’s team quickly replied to the email, saying ‘we would prefer you use our public bug bounty program, but we can exchange details by email if you prefer.’
At this point, Sullivan was advised by legal that it was not a reportable breach situation if he was confident the ‘hackers’ no longer had the data, that the data had not been disseminated further, and if the hackers would sign an NDA. This is what Sullivan and his team proceeded to do — and it is not so far from modern bug bounty systems. The researchers personally downloading the database is effectively a proof of concept. Metasploit was founded on the need for PoCs because of vendors’ tendency to claim, ‘that’s not a bug, it’s a feature’. Payment to the researchers is little different to paying a bounty.
Sullivan’s team tracked down and located the hackers – primarily “a kid named Brandon”. This precise attribution was necessary for an effective NDA — the same NDA that the prosecution claimed to be proof of a coverup. In reality, Sullivan’s team had located the hackers, verified that the personal data was destroyed and had never been disseminated, paid a bug bounty for disclosure of the vulnerability, and obtained an NDA to confirm the hackers would not disclose details of the vulnerability.
It is worth stressing that this process was successful: the stolen Uber database has never been found on the dark web. So, effectively, Sullivan improved Uber’s security, protected personal information and paid a bounty for disclosure.
For this he was prosecuted and convicted. He was charged on two counts: obstructing an FTC investigation, and misprision of a felony (failure to report knowledge of a felony to the authorities; that is, failure to report the breach that he had been advised by legal wasn’t necessary, and/or failing to report the kid named Brandon to law enforcement for breaking the CFAA). It would be fair to say that many people in the security industry do not consider Sullivan did anything unethical. (Sullivan is appealing his conviction, although the outcome is unknown at the time of writing.)
Anderson Lunsford, an attorney and CEO of incident reporting and response firm BreachRx, wrote in October 2022, “I don’t know Joe, but seeing him prosecuted and found guilty is shocking, though unfortunately not surprising… Joe is suffering from being the ‘Chief Scapegoat Officer’… Joe Sullivan is the first person we’ve seen prosecuted criminally for how his company handled a data breach, but I do not expect this to be a one-off or rare occurrence.”
The scapegoat effect is a real threat to CISOs — they can take the fall for incidents outside of their control, even when they may be trying to do the right thing within a sea of contradictory pressures.
More recently, in June 2023, the SEC sent Tim Brown (CISO at SolarWinds) a Wells Notice over the 2020 Orion incident. A Wells Notice is formal advice that the SEC is considering enforcement action. Sounil Yu, CISO at JupiterOne, comments, “It is clear that we will be held accountable for both how we represent ourselves before a breach (Tim Brown) and how we handle events after a breach (Joe Sullivan). With these concerns, it is common for CISOs to leave their position when they feel like they are being set up to be a scapegoat.”
“There is still a prevalent perception that CISOs are viewed as scapegoats in serious breach events,” adds George Jones, CISO at Critical Start. “This is based on a general lack of understanding, high expectations, and accountability associated with the role. When a breach occurs, it’s easy to point the finger at the person responsible for cybersecurity.” It’s the effect, says Yu, of “accountability without authority”.
Making the CISO a scapegoat is a common but not blanket response to cybersecurity incidents. Agnidipta Sarakar, VP and CISO advisory at ColorTokens, points out, “Organizations who are mature tend not to blame the CISO unless the security program is actually not good enough.” But less mature organizations with weaker programs or negligent security oversight will readily activate the scapegoat effect.
This scapegoat effect is a major cause of CISO churn, whether it is instigated by government, business leaders unwilling to shoulder their own blame, or CISOs knowing they have insufficient resources to prevent a breach and moving on before the inevitable happens.
Cause #2: lack of board support
Board recognition of the importance of the CISO and cybersecurity is slowly growing, but remains far from optimum. An August 2023 survey by BSS of 150 UK security decision makers found that only 28% felt their role was valued; 22% were actively involved in the wider business strategy; and only 9% said cybersecurity was always in the top three priorities on boardroom agendas.
BSS director Chris Wilkinson commented, “CISOs need a seat at the table. Such a poor level of prioritization for information security is unacceptable in a world of evolving threats that can result in significant financial and reputational penalties.”
Globally, there are many companies where cybersecurity is both prioritized and supported, but these tend to be among the larger and more mature organizations. There remains a large underswell of newer and smaller companies where growth is often prioritized over security.
“When CISOs interview for a new role,” comments Yu, “we are often led to believe that the hiring organization cares about security and will champion the CISO’s initiative to bolster their security program. However, once the CISO lands in the role, it becomes clear how much true authority they have to drive change.”
The result is often a lack of support and resources for the CISO to implement the cybersecurity controls necessary to secure the company. So, whether it is to forestall becoming the scapegoat for the inevitable breach, or simple frustration at not being able to do a good job, lack of board support often leads to CISOs seeking a new and more responsive position.
Cause #3: stress and burnout
Stress is another cause of CISO churn. It’s not stress on its own, but the cumulative mental and emotional debilitation caused by multiple, different, and continuous stressors: burnout.
Burnout can strike suddenly. A CISO may think he or she is handling stress effectively, but a single, final straw can suddenly and unexpectedly tip the balance. Burnout can cause physical and/or mental collapse. Sufferers may need to take extended time out, move to a less stressful position, or simply leave the industry altogether. “Some CISOs are moving into consultancy,” comments Sarakar, “especially when they have the experience, but they don’t want the operational fatigue.”
“The CISO job can be a stressful one, especially when you have accountability without authority,” explains Yu. “If CISOs are held responsible for security outcomes but aren’t given the tools or power to influence those outcomes, they will feel helpless and frustrated, leading to decreased morale and motivation.”
A recent survey by Salt Security lists six of the top personal stressors experienced by CISOs globally. Noticeably, the threat of personal litigation is #1 (48%). Only 1% of CISOs don’t feel they face any personal challenges.
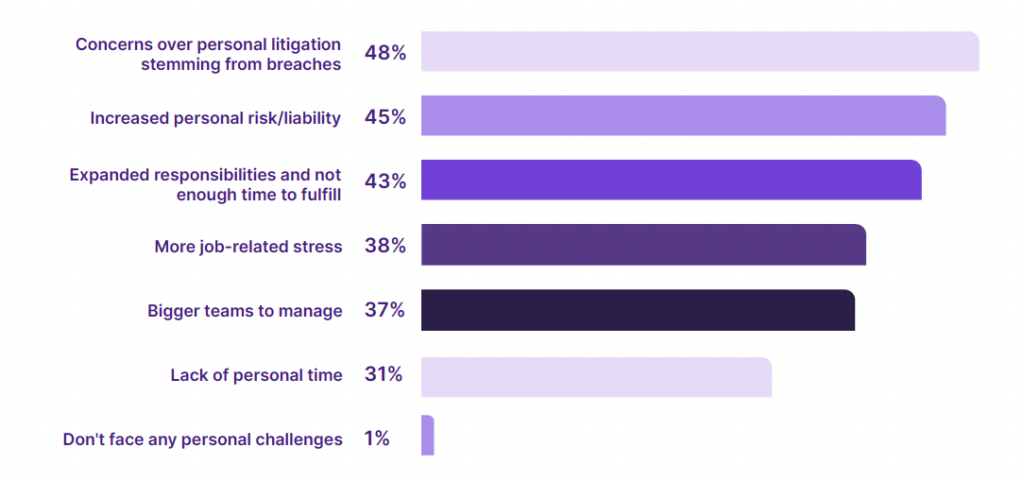
The scapegoat effect and lack of adequate boardroom support are clearly contributing factors to CISO burnout – but so too are overwork and frustration. Success in cybersecurity is when nothing happens: effectively a successful CISO can work his or her butt off, and have nothing to show for the success.
Cause #4: the next big challenge

Not all CISO churn is caused by the job’s difficulty. There are many CISOs that are simply very good at their job and can confidently ride all the difficulties. Such people thrive on challenge and career progression. The difficulty is that career progression within the same organization is likely to be difficult. The only option is to take on a new challenge in a different organization with potentially a larger budget, a bigger security team, greater responsibility, more authority, and – probably – higher remuneration and benefits. These CISOs have simply outgrown their existing position and need to move on to the next big challenge.
“CISOs are a special breed,” explains Jennifer Pittman-Leeper, whole of state strategist at Tanium. “They want to help, but if their hands are tied, they aren’t willing to stick around assuming the risk for an organization that isn’t willing to put in the hard work and reduce risk. They also love a good challenge. Once they get an organization on a good path, they are ready to tackle the next cyber mountain. A CISO skill set is quite unique – it’s a mix of introvert and extrovert, technical and strategic, communicator and listener. If you have a good one, it is in your best interest to keep them as long as you can.”
CISO churn is a hidden cybersecurity threat. Major security initiatives or implementations can take longer than the residency of a single CISO, and new CISOs may have different beliefs on how to implement security. Constant churn can leave cracks or gaps in security.
New CISOs will also need to understand the business before being able to secure it –that in itself is a challenge. Sarakar believes that only “about 10-20% [of CISOs] actually understand business context, 10-20% have low experience or are underqualified, and the rest have medium understanding of business context.”
The average tenure for a CISO is often quoted as 18 months. Pittman-Leeper analyzes this: “I think the reason is for the first six months they are trying to figure out their way at the organization. Learn who is who, what the real story is. The next six months are spent trying to effect change and policy. These six months are critical – they will either meet resistance and not be able to improve the security posture or they will be successful in implementing meaningful change. The last six months are spent ensuring compliance and helping the stragglers along the way – or looking for a job where they will be able to help an organization.”
The result of this timeline is just a short period of effective cybersecurity, between settling in and trying to find a way out: there is little time for the CISO to implement seriously effective security controls.
Obviously, the 18-month tenure does not apply to all CISOs and all organizations – more mature and especially larger organizations tend to keep the same CISO for longer periods – but new and smaller organizations are the ones most likely to suffer from rapid churn. This, through supply chains, will have a knock-on effect on the wider cybersecurity ecosystem.
There is only one real solution to the CISO Carousel: better communication. While boards must learn to love their CISOs (which includes respect, responsiveness, resources, and support); CISOs must better understand business imperatives and better communicate cybersecurity imperatives to business leaders.
Respect and support go beyond simply paying inflated salaries (although adequate compensation is essential). You cannot buy enthusiasm – it must be fostered by respect and support. Above all, the fear of scapegoating should be eliminated by genuine support. CISOs rarely criticize each other. When a breach occurs in another company, the general feeling is ‘there but for the grace of God go I’. Breaches cannot be eliminated. CISOs need to be confident that the expectation is to limit and ameliorate breaches, and that one single success by an elite hacker with a zero day exploit won’t lead to dismissal.
Board responsiveness requires listening to the CISO’s concerns and recommendations in a constructive manner. This is a two-way requirement: boards must have a better understanding of cybersecurity, while CISOs must learn to better communicate security requirements into a business-relevant language.
An August 2023 report from the Advanced Cyber Security Center and CyberSaint noted, “Board members lament they continue to get overly technical reports from management teams that fail to put governance in business and financial terms. While cyber risk has by all accounts become a higher priority for Boards, security executives are frustrated that too often cyber risk and cyber management continue to be secondary topics to enterprise strategic plans and success.”
Adequate resources for the cybersecurity function will only result from better responsiveness between the needs of security and business. Boards need to bring security out of its silo and integrate it into the business process. Only when both work in lockstep will the CISO churn be slowed, and the full benefit of stable security leadership be achieved.
Related: CISOs’ New Stressors Brought on by Digitalization: Report
Related: Why CISOs Make Great Board Members
Related: Boardrooms Are Still Not Singing the Security Song
Related: The VC View: Digital Transformation


