Business Email Compromise (BEC) poses a growing threat to businesses of all sizes. As BEC attacks have almost doubled across the Verizon DBIR entire incident dataset and represent more than 50% of incidents within the social engineering pattern.
Attackers use various tactics to access sensitive information, such as email account compromise and using a legitimate email address to initiate the attack.
BEC attacks can occur in various ways, using a variety of methods. But what makes them different and arguably more dangers is they are driven by intent. BED attacks target specific individuals within organizations and have messages that are often personalized to the intended victim.
These strategies include spoofing an existing email or website, or spearphishing (using emails that come from trusted sources). Read on to learn how these attacks work and how to protect yourself against them.
Recognizing a Business Email Compromise Attack
Running a business is complex, and with so many moving parts, attackers can attempt different angles, targeting C-level executives, shipping departments, billing, or IT.
Both internal and external threats can occur but 83% of breaches involved external actors with Financial motives. With that, it’s best to explore several real-world attacks to learn from.
CEO Fraud
This type of attack involves a threat actor impersonating a C-suite individual, such as the CEO or CFO of a company. The attacker would then email an individual in the finance department requesting a fund transfer.
The transferred funds would be directed to an account controlled by the attacker.
To make the attack more effective, the threat actor may have researched their targets and attempted to match their language, terminology, style, and email address as closely as possible.
If the target does not pay attention, they may fall for the ruse and transfer the funds.
Account Compromise
In a more insidious attack, an attacker may compromise an existing employee’s email account from the inside. With access to this compromised account, the attacker can then request payments to vendors that are accounts controlled by the attacker.
For instance, Joe in the purchasing department could have their account compromised. His email could then send numerous requests to billing that seem like standard payment requests to vendors, usually for smaller amounts.
Since the request comes from a trusted account, billing may not scrutinize it closely and pay the vendor. Additionally, larger companies may need more resources to audit every request, resulting in many missed requests.
False Invoice Scheme
An attacker may email a company requesting payment of an invoice, insisting that it is overdue for services rendered.
An overworked billing department may not think twice about paying it, especially if the email and invoice look legitimate and mimic those of prior vendors.
In addition, an attached PDF may contain malware, allowing for an account compromise attack.
Attorney Impersonation
While most attacks in this area have focused on the vendor supply chain, this attack targets many people’s natural unease when dealing with legal matters.
A supposed attorney contacts the target and requests payment for a settlement or threatens legal action if payment is not received.
Rather than risk being on the wrong side of the law or embroiled in a lawsuit, some employees may pay the requested funds to avoid issues. Cases can be extremely costly, so paying the lower amount may be an attractive option to make the issue disappear without engaging expensive company lawyers.
Data Theft
A typical attack targeting human resource employees involves data theft. The objective is to gather personal and sensitive information about individuals in positions of power for reconnaissance purposes.
With this information, an attacker can launch more sophisticated schemes, such as CEO Fraud, by leveraging the intimate details they have acquired to make their emails seem more believable.
Compromising Business Email
BEC attacks are a type of social engineering attack that takes place over email. The attacker falsifies an email message to trick the victim into performing some action.
In these situations, the goal is not only to have the target perform the requested task but also to compromise their computer for future attacks against the business. A compromised computer can quickly provide private information about the employee and the company.
For instance, with a compromised email account, an attacker could see that a company works with a specific vendor. The attacker could then craft an email from the compromised account and send it to the billing department, requesting payment to the same vendor but to an attacker-controlled account.
So, what can a company do to protect against this type of theft? Along with providing in-depth education on the types of attacks and social engineering required to carry out this theft, a company needs a robust security infrastructure if an account is compromised. This includes implementing strong password policies to prevent the use of compromised credentials in attacks.
Protect User Accounts with Specops Password Policy
Business Email Compromise (BEC) attacks can have a devastating impact on a business and it’s essential to take steps to mitigate the risk.
Passwords continue to be a crucial factor, as 49% of breaches by external actors involved use of stolen credentials, so it’s important to enforce strong password policies.
Specops Password Policy with Breached Password Protection, helps you increase password security in your Microsoft Active Directory environment while blocking over three billtion already known compromised passwords.
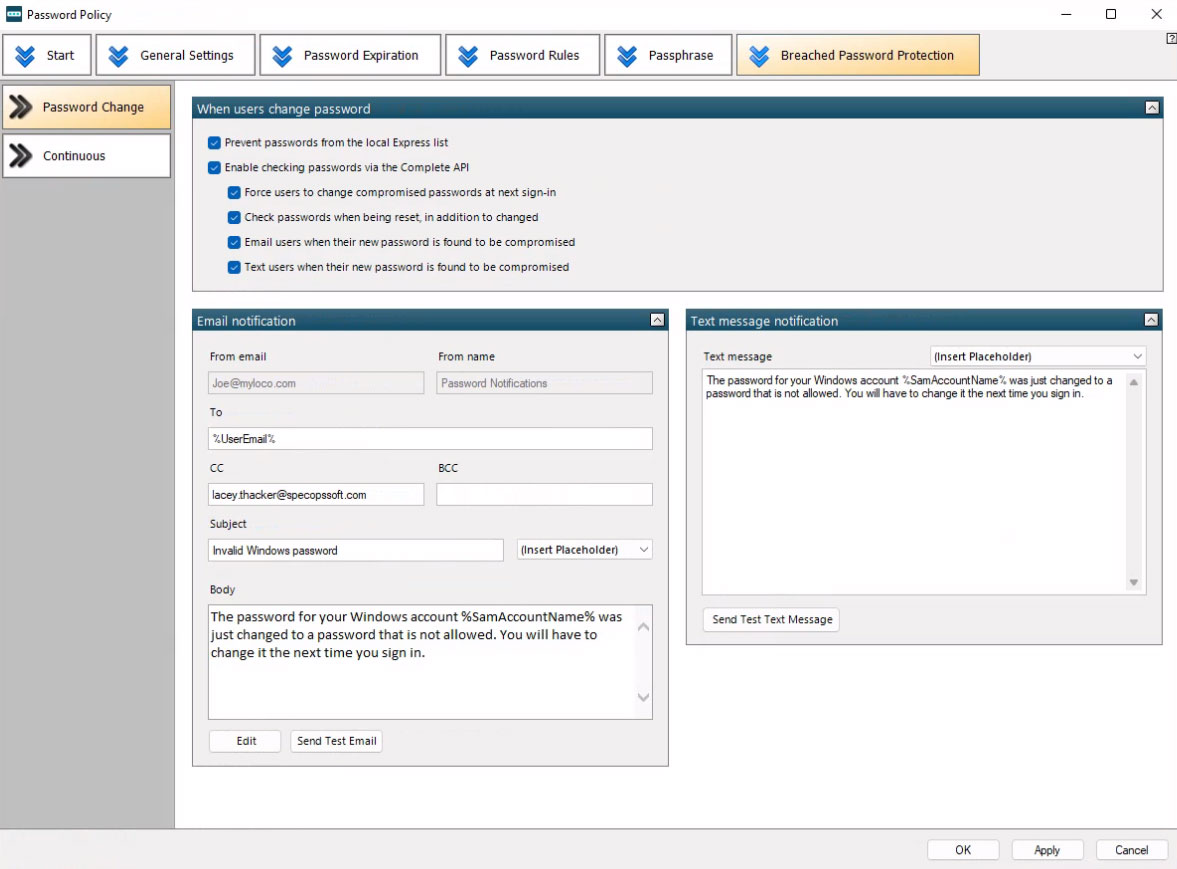
The tool extends the functionality of Group Policy, and simplifies the management of fine-grained password policies while offering realtime dynamic end user feedback at password creation.
The Danger of Business Email Compromise Attacks
As more and more business moves online, Business Email Compromise (BEC) attacks will become increasingly more common and challenging to detect.
But, with proper education and vigilance on the part of employees, paired with a robust password policy such as one offered by Specops Password Policy, these attacks can be mitigated.
Organizations want to avoid being on the receiving end of such an attack, especially one that can result in a huge finanical loss as 95% of all breaches are financially driven.
By learning about the types of attacks and taking preventative measures, you can ensure your business is better protected.
Sponsored and written by Specops Software
