The NoName hacker group enlisted a number of European organizations as victims early this week. Among them was the Czech company TAJMAC-ZP, the German Ministry of Foreign Affairs, and the Port Authority of Bremen, Germany. The Czech Foreign Ministry cyber attack was also claimed by the NoName hacker group.
The Czech Foreign Ministry cyber attack and other targeted
FalconFeedSio tweeted the following government website that was allegedly targeted by NoName:
- The Czech Foreign Ministry
- The SOR company, Czech Republic
- Czech company TAJMAC-ZPS
- The German Ministry of Foreign Affairs
- The Federal Ministry of Transport and Digital Infrastructure, Germany
- The Port Authority of Bremen, Germany
The Cyber Express reached out to the Czech Foreign Ministry regarding the alleged cyber attacks on its website, and we are yet to receive a response from them.
The official website following the Czech Foreign Ministry cyber attack was accessible at the time of writing. However, the website of the SOR company was inaccessible and displayed the following:

Similarly, the website of TAJMAC-ZPS, a machinery manufacturing company was also not accessible at the time of writing.
The following post was shared by the NoName hacker group on their leak site claiming the TAJMAC-ZPS cyberattack.
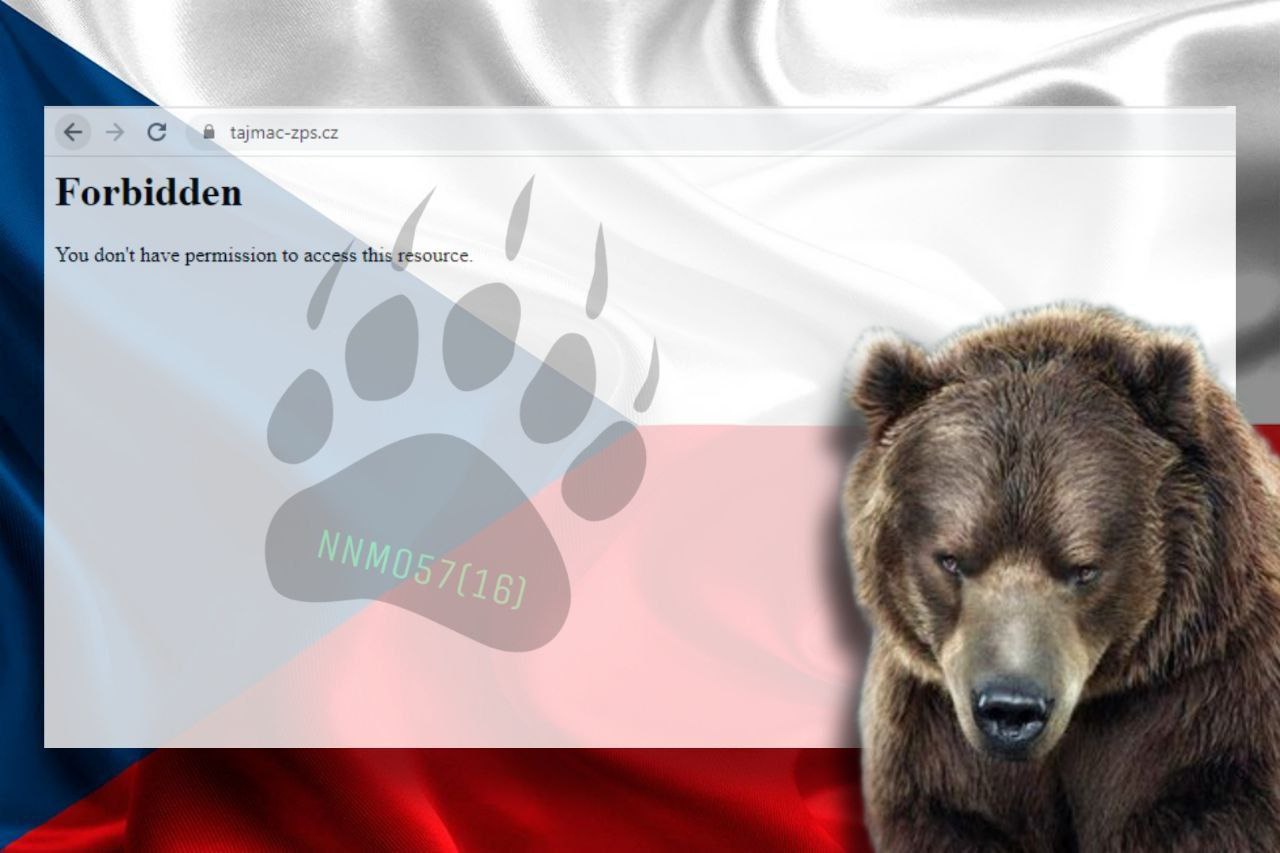
TAJMAC-ZPS is based in Malenovice, Czechia or Czech Republic.
The website of the German Ministry of Foreign Affairs was active as opposed to the claims made by the NoName group as shown below, post the alleged DDoS attack.
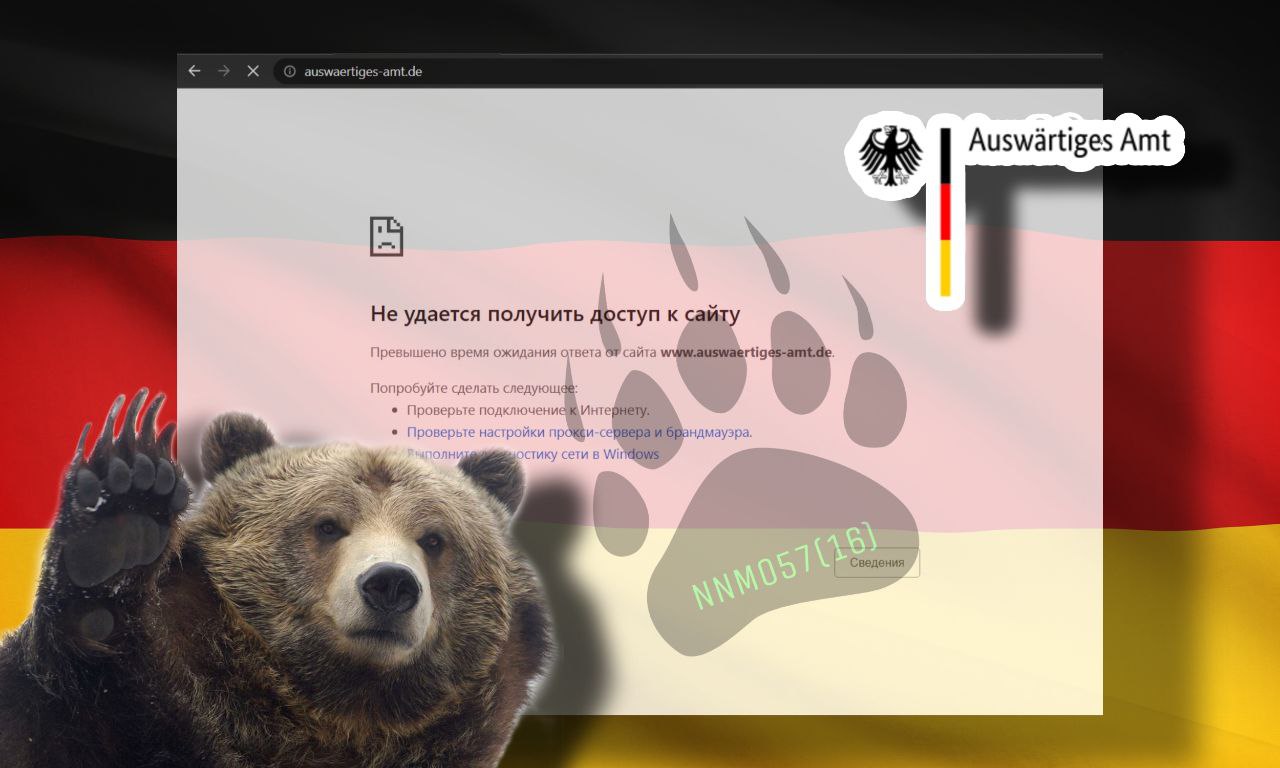
Among the other targets named alongside the Czech Foreign Ministry cyber attack were the website of the Federal Ministry of Transport and Digital Infrastructure, Germany, and the website of the Port Authority of Bremen, Germany. While the former was inaccessible and showed an error message, the latter was functional.
The Cyber Express reached out to the authorities for comments about the alleged cyberattacks. We will update the story with updates as we receive more information.
What the German officials have to say about Gaza and Israel
Several groups including Anonymous Sudan and the NoName hacker group are launching attacks in the name of hacktivism or support for Russia in the Russo-Ukrainian war. All while governments are declaring support to form peace.
“We are deeply alarmed by this new round of violence and the deteriorating security situation in the occupied Palestinian territories and Israel, and ongoing developments in Gaza, which has claimed unacceptable civilian casualties including women and children,” read a press release on the Federal Foreign Office website of Germany.
In another news release posted on the German website, a ceasefire was welcomed by the German authorities saying, “Germany welcomes the ceasefire in Gaza and Israel announced yesterday.”
“We mourn the civilians killed. Our thoughts are with the many wounded,” the news release further added. It is now up to hacktivists and cybercriminals to stop the cyberwar and put the government and not attack the websites.
Czech Foreign Ministry cyber attack and NoName’s long list
The Czech Foreign Ministry cyber attack is the latest in the list of campaigns NoName launched in the region. NoName has been targeting several European nations’ government and defense force websites, in retaliation of supporting Ukraine in the Russo-Ukrainian war.
Dubbed NoName057(16) by researchers, the threat group has been active since the early days of the war in Ukraine, and has since conducted a range of high-profile attacks on various targets.
Most recently, the group disrupted services across the financial sector of Denmark, highlighting the potential risks that cyberattacks pose to critical infrastructure.
Apart from the Ukrainian organizations attacked by NoName, the greatest hits in the threat group’s playlist were businesses and organizations in Poland, Lithuania, and other countries.
A notable attempt started on January 11, when NoName reportedly began targeting the websites of candidates in the upcoming 2023 Czech presidential election, reported cybersecurity firm SentineOne.
Initial attacks focused on Ukrainian news websites, while later shifting to NATO associated targets,” said the SentinelOne report. For example, the first disruption the group claimed responsibility for were the March 2022 DDoS attacks on Ukraine news and media websites Zaxid, Fakty UA, and others.
Overall the motivations center around silencing what the group deems to be anti-Russian.” Despite the group’s efforts to remain anonymous, researchers at SentinelLabs have identified several tools and tactics used by NoName057(16) to carry out their attacks.
These include public Telegram channels used for communication, a volunteer-fueled DDoS payment program, a multi-OS supported toolkit, and GitHub, among other methods.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
