VALIC Retirement Services Company is among the latest victims of the MOVEit File Transfer cyber attack.
The VALIC cyber attack is estimated to impact 798,000 persons, raising the number of MOVEit vulnerability victims from about 30 million as of July 31.
VALIC Retirement Services Company is the subsidiary of Variable Annuity Life Insurance Company, or VALIC, a group company of the American International Group (AIG).
Valic cyber attack through PBI using MOVEit
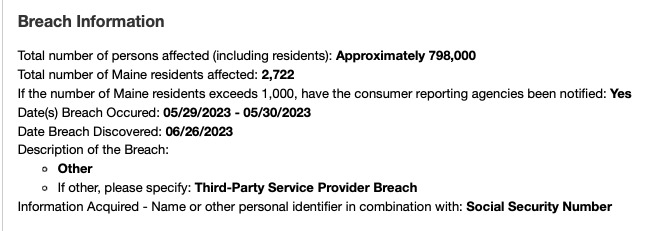
Valic Retirement Services Company (VRSCO) filed a notice about the Valic cyber attack with the attorney General of Maine, according to a JDSupra report. A vendor of Valic suffered a security breach coming from the MOVEit cyber attack.

The compromise led to the exposure of confidential VRSCO client information including names, Social Security Numbers, policy or account numbers, dates of birth, and addresses. The vendor of Valic that was impacted by MOVEit vulnerability exploitation was Pension Benefit Information (PBI) LLC.
The filed notice by VRSCO about the Valic cyber attack had a letter attached from the PBI explaining the compromise of its data impacting Valic.
On May 31, 2023, Progress Software announced that the MOVEit software contained a critical vulnerability. Evidently, hackers were able to exploit this vulnerability and access the MOVEit server used by PBI, The Cyber Express reported.
MOVEit cyber attack victims
An SQL injection vulnerability CVE-2023-34362 was found to be exploited by the Cl0p ransomware group in May 2023. The exploited MOVEit vulnerability was named on June 2, 2023.
Shortly after evidence of the attack surfaced, Progress patched the vulnerability. However, that small time window was enough for Cl0p ransomware group to launch a worldwide cyber attack.
“Even though the MOVEit patch has been issued, some users of the service continue to be attacked because they haven’t installed the patch on their networks. This underlines the importance of threat intelligence and a well-defined patching strategy,” said an IBM report of the situation.
No industry escaped the consequences of the malicious CL0P campaign.
“Dozens of entities from the public and private sectors have been impacted. Victims include payroll services, retailers, major airlines, government offices, two Department of Energy entities and the U.S. states of Missouri and Illinois,” it said.
Those organizations using the services provided by MOVEit were largely impacted by the data breach.
During the second week of July, the impact of this vulnerability extended to 299 organizations, affecting a staggering 18,154,787 individuals. However, by July 18, the number of affected individuals surged to 19,879,769.
As of July 21, the figures continued to rise, reaching 20,421,414 impacted individuals, with only 66 disclosures reported.
Significantly, 384 organizations were still in the process of confirming the number of individuals affected. Among them were 70 schools, 20 public sectors, and 31 international public sectors.
Third party vendors and lawsuits for loss of privacy
Other third-party vendors like PBI, National Student Clearinghouse (NSC) and Teachers Insurance and Annuity Association (TIAA) used by US schools and Universities were also impacted. Nearly 3,600 US educational institutions use NSC and TIAA for research and employee accounts, respectively.
CalPERS is a government agency that manages the largest public pension fund in the US. A CalPERS retiree recently sued PBI because their Social Security Number was compromised due to the MOVEit cyber attack.
CalPERs used MOVEit to exchange retirees or beneficiaries data with clients. The lawsuit stated that the PBI and Berwyn Group were negligent in securing the data violating the right to privacy of retirees and violated the California Customer Records Act.
According to a report from the cybersecurity rating platform SecurityScorecard, a remarkable 78% of the major financial institutions within the European Union encountered a third-party breach in the previous year.
The report focused on analyzing the preparedness of 240 of the EU’s largest financial institutions to comply with the Digital Operational Resilience Act (DORA) by January 2025.
It is not uncommon to see banking and financial service companies making headlines in cybersecurity news as they remain a favored target for cybercriminals.
Furthermore, the report revealed that an alarming 84% of financial institutions have been exposed to a breach through a fourth-party.
