XWorm has emerged as one of the most versatile and actively distributed remote access trojans in the current threat landscape, establishing itself as a formidable tool in cybercriminals’ arsenals.
This sophisticated malware has evolved far beyond traditional RAT capabilities, incorporating advanced features including keylogging, remote desktop access, data exfiltration, and command execution that make it particularly attractive to threat actors seeking comprehensive system control.
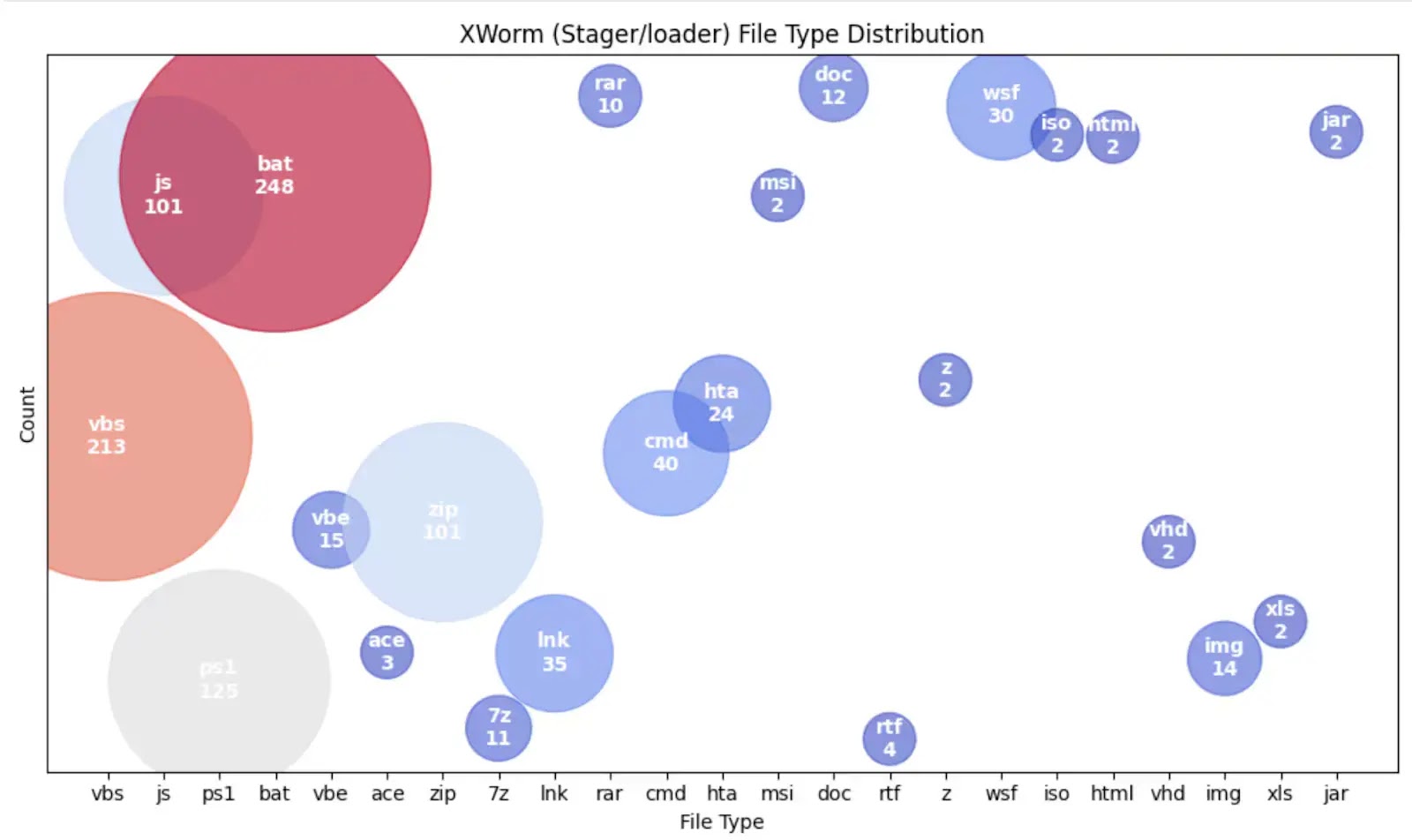
The malware has demonstrated remarkable adaptability in its delivery mechanisms, employing a dynamic approach that cycles through multiple file formats and scripting languages to evade detection.
Unlike conventional malware that relies on fixed infection chains, XWorm leverages PowerShell scripts, VBS files, .NET executables, JavaScript, batch scripts, and even Office macros as initial attack vectors.
This shape-shifting capability significantly complicates detection efforts and suggests a deliberate strategy to circumvent endpoint defenses and sandboxing technologies.
Recent campaigns have shown XWorm targeting organizations within the software supply chain and gaming industry, with attackers deploying both AsyncRAT and XWorm as initial-stage malware to establish persistent footholds.
Splunk analysts identified that these operations often culminate in ransomware deployment using leaked LockBit Black builder tools, linking XWorm activities to broader ransomware ecosystems.
Analysis of over 1,000 XWorm samples from Malware Bazaar revealed recurring phishing themes centered around invoices, receipts, and delivery notifications designed to appear urgent and business-critical.
The threat research community has documented XWorm’s sophisticated evasion techniques, with Splunk researchers noting the malware’s ability to patch critical Windows security features.
.webp)
The malware specifically targets the AmsiScanBuffer() function within the amsi.dll library, effectively disabling the Antimalware Scan Interface that allows security software to scan scripts and content in memory before execution.
Advanced Defense Evasion Through System-Level Manipulation
XWorm’s most concerning capability lies in its multi-layered approach to evading Windows security mechanisms.
The malware deploys specialized components that systematically disable key monitoring and detection systems through direct memory manipulation.
The first component focuses on AMSI bypass, using the following technique to patch the scanning function:-
IntPtr intPtr = Program.a(Program.d, Program.e);
byte[] array2 = array;
uint num;
Program.c(intPtr, (UIntPtr)((ulong)((long)array2.Length)), 64U, out num);
Program.copy(array2, intPtr);Simultaneously, XWorm deploys a second evasion mechanism targeting Event Tracing for Windows (ETW) by patching the EtwEventWrite() function.
This technique effectively blinds system monitoring tools by preventing the logging of malicious activities.
The malware achieves persistence through multiple vectors, including registry run keys and scheduled tasks that reference VBS scripts and batch files dropped in the %appdata% directory.
.webp)
The infection chain demonstrates remarkable sophistication in its use of process injection techniques, specifically targeting legitimate Windows processes including Taskmgr, explorer, and svchost.
XWorm injects shellcode into these processes while simultaneously hooking various Windows APIs to hide its presence and maintain stealth operations.
This comprehensive approach to system manipulation represents a significant evolution in RAT capabilities, requiring equally sophisticated detection and mitigation strategies from security teams.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
