A sophisticated new “packer-as-a-service” tool known as Shanya has emerged in the cybercriminal underground, rapidly becoming a preferred weapon for major ransomware groups looking to neutralize endpoint defenses.
According to new research from Sophos, Shanya is an evolution in the “EDR killer” market, effectively succeeding previous tools like HeartCrypt.
The malware is designed to blind security monitors and terminate protection processes, clearing the path for ransomware payloads such as Akira, Medusa, and Qilin to encrypt victim networks without interference.
Researchers first identified the tool in late 2024 on Russian-language underground forums. Marketed as “VX Crypt” by an entity using the handle “Shanya” a reference to a river in western Russia the service promised advanced evasion capabilities.
Its feature set included non-standard module loading, unique stub generation for each customer, AMSI (Antimalware Scan Interface) bypassing, and resistance to sandboxing.
The malware’s creators also boasted of runtime protection for .NET assemblies and the ability to run undetected for extended periods, a claim that has unfortunately held true in recent incidents.
How Shanya Works
Shanya operates primarily through DLL side-loading, a technique where malicious code mimics legitimate system libraries to trick trusted applications into running it.
In analyzed attacks, the malware frequently abused consent.exe a legitimate Windows User Account Control component to load a malicious DLL, often named msimg32.dll.
Once active, Shanya deploys a “bring your own vulnerable driver” (BYOVD) attack. It drops a legitimate but vulnerable driver, such as ThrottleStop.sys, alongside a malicious kernel driver.
By exploiting the vulnerable driver, Shanya gains kernel-level write access, allowing it to forcibly terminate a vast list of processes and services associated with antivirus and EDR (Endpoint Detection and Response) products.
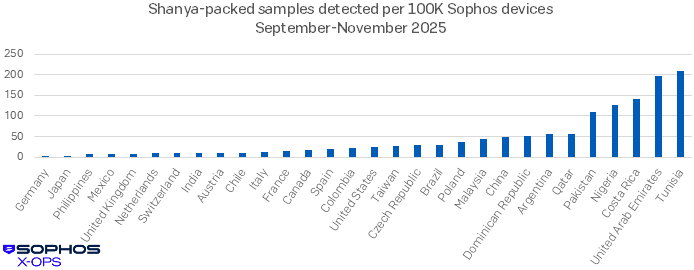
Geographic distribution for nascent malware can be useful information. In Shanya’s case, we have encountered the packer in all four hemispheres over the course of 2025.
The loader itself is highly obfuscated, using “junk code” and API hashing to frustrate analysis. It hides its configuration in the Process Environment Block (PEB) and modifies system DLLs in memory to execute its payload covertly.
Real-World Impact
Throughout 2025, telemetry has shown Shanya deployed globally, with notable concentrations in the UAE and parts of Asia.
The loader loads a second instance of a Windows system DLL. In all the cases we analyzed, this system component was shell32.dll.
Its most destructive application has been as a precursor to ransomware. Since its debut in a Medusa attack in April 2025, it has become a staple for the Akira ransomware group.
As the market for evasion tools matures, researchers warn that “packer-as-a-service” offerings will likely remain a critical component of the ransomware supply chain, necessitating constant vigilance from defenders.

In September 2025, the tool was also linked to a “ClickFix” campaign targeting the hospitality sector.
Attackers used fake Booking.com verification pages to trick hotel staff into downloading the malware, which subsequently deployed the CastleRAT backdoor.
Security vendors have updated their signatures to detect this threat. Sophos identifies the packer and its components under the family names ATK/Shanya-B, ATK/Shanya-C, and ATK/Shanya-D.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
