In a concerning development within cybersecurity, attackers have been leveraging DocuSign’s API capabilities to send out fraudulent invoices that closely mimic genuine documents. These campaigns have been rising in frequency, with reports over the past five months highlighting a significant uptick in incidents. In the context of cybersecurity, the abuse of DocuSign’s API represents a significant shift away from traditional phishing methods. Conventional phishing attacks typically involve sending spoofed emails that mimic trusted brands to trick victims into clicking malicious links or entering sensitive data, such as login credentials. Email and anti-spam filters have evolved to detect and block these deceptive tactics effectively, making it more difficult for attackers to succeed using traditional methods.
However, when malicious emails originate from reputable services, such as DocuSign, it becomes far more challenging for users and security tools to detect and flag them. This is because these emails are sent from legitimate accounts and utilize genuine templates from well-known brands, enhancing their credibility. For instance, attackers can create realistic invoices using actual DocuSign branding and send them through the platform, which bypasses many conventional filters designed to catch phishing attempts.
Cybercriminals have previously used other legitimate online services, such as sharing documents via Google Docs, to deliver malicious content. The current trend involves leveraging DocuSign, an e-signature service trusted by many organizations, to propagate scams at a scale that traditional phishing attempts rarely achieve. This approach integrates fraudulent activities seamlessly into standard communication workflows, making them appear trustworthy and increasing the likelihood of success.
This evolving method poses a significant threat as it targets the inherent trust users place in legitimate services and their communications, leading to a higher risk of compliance and payment-related fraud.
How the Scheme Operates
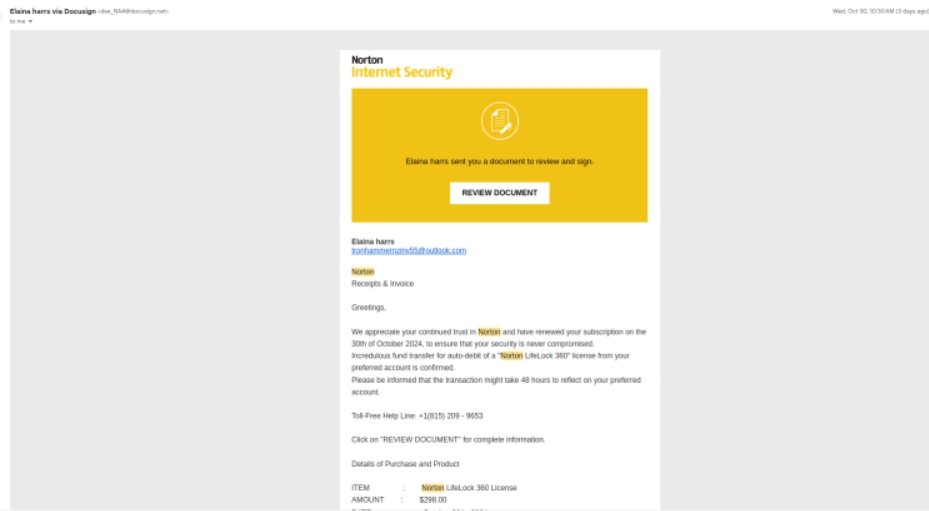
Attackers establish legitimate, paid DocuSign accounts, enabling them to customize templates and use the platform’s API to send out documents that appear authentic. Common targets include software companies, such as Norton Antivirus, whose branding is imitated to make these invoices look convincing. These documents may feature correct pricing or additional charges, such as activation fees, and are designed to elicit payments from unwary recipients.
Once a victim e-signs the document, attackers either send the signed document to finance departments for payment or use it to make direct payment requests outside of DocuSign. Because these invoices originate from trusted sources within DocuSign’s network, they evade detection by email and phishing filters, presenting a formidable challenge for standard cybersecurity measures.
How Attackers Create and Use Paid DocuSign Accounts
Attackers have found a way to exploit the legitimate infrastructure provided by DocuSign to propagate fraudulent activities. The process begins with the creation and use of paid DocuSign accounts, which allows attackers to leverage the platform’s full suite of tools and features. Here’s how they carry out these schemes:
- Setting Up Legitimate Accounts:
- Attackers register for paid DocuSign accounts, ensuring that they have access to premium features, including the ability to create and customize templates and utilize API capabilities.
- By using legitimate payment methods or stolen credit card information, they avoid raising immediate red flags during account registration.
- Crafting Customized Templates:
- Once an account is established, attackers use DocuSign’s tools to create templates that closely mimic those of reputable companies. This could include well-known software brands like Norton Antivirus or other prominent firms.
- These templates feature authentic branding, logos, and design elements, making the invoices appear highly credible to recipients.
- API Utilization for Mass Deployment:
- The use of DocuSign’s API, particularly the Envelopes: create endpoint, allows attackers to automate the process of sending these fraudulent invoices on a large scale.
- By integrating automation, attackers can deploy scams quickly and efficiently, reaching numerous targets with minimal manual effort.
- Content and Tactics:
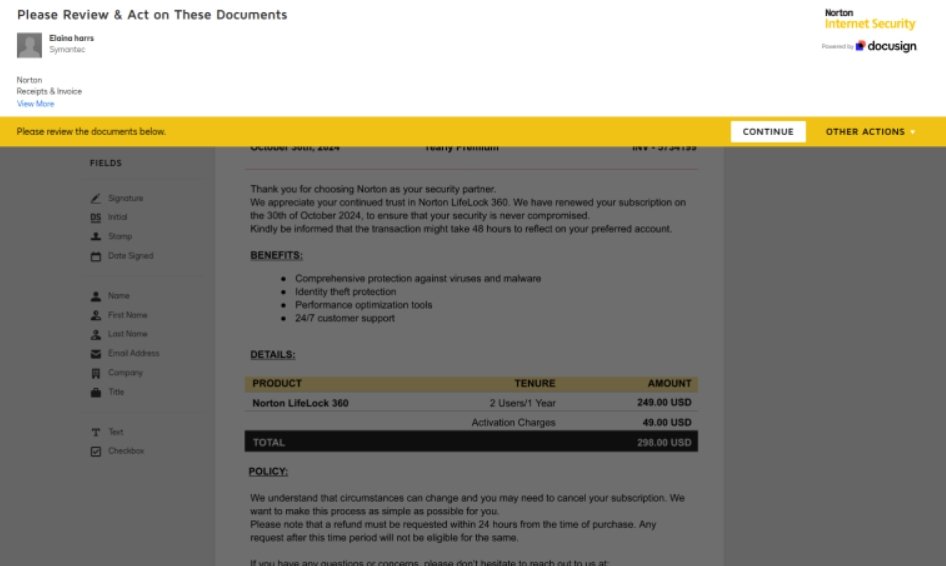
- The invoices often contain accurate pricing details and may include additional fees like activation charges to enhance the illusion of authenticity.
- Tactics may also involve direct wire instructions or other payment information to redirect funds to the attackers’ accounts.
- Execution of Payment Requests:
- If the victim e-signs the document, attackers can utilize the signed document to submit payment requests directly to finance departments or request payment through other communication channels.
- Because these documents are sent through DocuSign’s legitimate infrastructure, they easily pass through email services and anti-phishing filters, reducing the likelihood of detection.
This calculated misuse of paid accounts and API capabilities reflects a sophisticated level of planning and understanding of platform functionality. It highlights the need for vigilant security practices within organizations to identify and prevent exploitation of trusted services like DocuSign.
The Role of API Automation in Scaling Attacks
The automation capabilities provided by DocuSign’s API, such as the Envelopes: create endpoint, have enabled attackers to deploy these scams at scale with minimal manual input. This abuse underscores how tools meant to improve business operations can also be exploited by cybercriminals. The ability to customize invoices using official templates, complete with unauthorized branding, amplifies the perceived legitimacy of these scams.
Challenges in Detection
The use of DocuSign’s legitimate platform for fraudulent activities introduces significant obstacles for traditional detection mechanisms. Here’s why these scams are particularly challenging to identify:
- Legitimate Source of Emails:
- Unlike traditional phishing scams that often use fake or suspicious email addresses, the emails involved in these DocuSign-based scams come from legitimate DocuSign accounts. This complicates detection because email services and anti-phishing tools are designed to trust communication from reputable sources like DocuSign.
- Absence of Malicious Links or Attachments:
- Conventional phishing detection methods rely on identifying suspicious links or attachments within emails. However, the scams conducted through DocuSign typically do not include these elements. Instead, the danger lies in the document itself, which may look perfectly legitimate and contain requests for payments or financial authorizations.
- Use of Authentic Branding and Templates:
- Attackers often use genuine templates provided by DocuSign or create highly accurate replicas of branded documents from reputable companies. These templates include real logos, designs, and official-looking layouts, making it nearly impossible for recipients to distinguish between a fraudulent and a legitimate invoice without closer inspection.
- Bypassing Email Filters:
- Since these emails originate directly from DocuSign’s platform, they inherently pass through email filters and spam detectors that are typically set up to identify untrusted or poorly constructed phishing attempts. This level of authenticity significantly reduces the likelihood that the emails will be flagged or quarantined.
- User Trust in DocuSign Communications:
- DocuSign is a widely trusted e-signature service used by many companies for secure document handling. As a result, recipients are more likely to trust communications and requests sent through DocuSign, increasing the chances of success for these scams.
- Minimal Anomalies in Email Headers:
- Advanced phishing attacks using DocuSign leverage legitimate email headers and domains (e.g., from the docusign.net domain). This makes them harder to spot during a cursory review and further enables these scams to evade detection mechanisms that scan for discrepancies in email metadata.
- Increased Automation:
- The attackers’ use of DocuSign’s API for automated delivery of fraudulent documents at scale means that these attacks can happen at a rapid pace, outpacing manual review processes. The automation also ensures a consistent format across large volumes of scams, making it harder to distinguish between genuine and fraudulent documents based solely on appearance.
These challenges highlight the need for updated and advanced strategies in both organizational training and technology to detect and prevent sophisticated attacks leveraging trusted platforms. Enhanced vigilance and multi-layered verification processes are key to minimizing the risk of falling victim to such scams.
Recommended Security Measures
Organizations are advised to adopt a multifaceted approach to safeguard against these types of threats:
- Verify Sender Information: Always confirm the credentials and associated accounts of senders, especially if invoices are unexpected or contain unusual fees.
- Internal Approval Processes: Implement rigorous procedures for financial transactions, requiring review by multiple team members to minimize the risk of unauthorized payments.
- Employee Training: Conduct training sessions to inform employees about the characteristics of such scams and promote a culture of vigilance.
- Anomaly Detection: Keep a close watch on unexpected or irregular invoices.
- Follow Provider Guidelines: Stay updated on best practices from DocuSign and other service providers for identifying and mitigating phishing threats.
For service providers, it is crucial to conduct threat modeling, apply rate limiting to API endpoints, and employ monitoring tools to identify potential abuse patterns.
This misuse of DocuSign’s API for distributing fraudulent invoices represents a sophisticated evolution in phishing tactics. By embedding scams within genuine platforms, attackers heighten their chances of bypassing conventional detection methods. As cybercriminals continue to adapt, organizations must prioritize proactive defense measures, focusing on API security and comprehensive employee training.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
