Google has warned about a method by which hackers could exploit its Calendar service to create a covert Command-and-Control (C2) channel. The technique involves using Google Calendar Events for C2 communications through a Gmail account. The tool, known as Google Calendar RAT (GCR), allows the compromised machine to poll Calendar event descriptions for new commands, execute those commands, and then update the event description with the results. Since the tool operates on legitimate infrastructure, it’s challenging for defenders to detect suspicious activity.
This method is part of a broader trend where threat actors abuse cloud services to blend into victim environments and avoid detection. For example, an Iranian nation-state actor used macro-laced documents to deploy a .NET backdoor named BANANAMAIL, which used email for C2 communications. Google has disabled the Gmail accounts used by this malware as part of its response.
The exploitation of Google Calendar by hackers for Command-and-Control (C2) operations involves a multi-step process that turns an innocent feature into a covert channel:
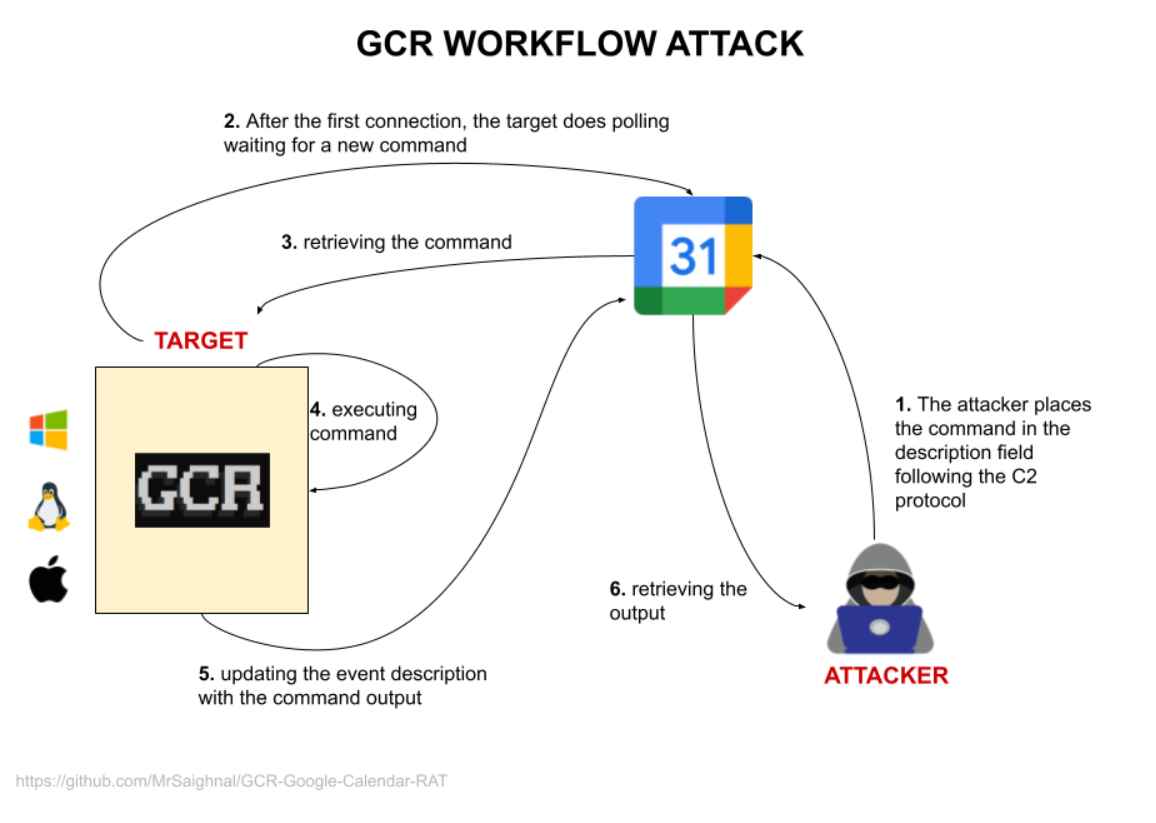
- Google Calendar RAT (GCR) Tool: Hackers developed a tool called Google Calendar RAT, which stands for Remote Access Trojan. This tool uses the Google Calendar service to issue commands to compromised systems.
- Event Descriptions as Covert Channels: GCR exploits the event descriptions in Google Calendar. It essentially creates calendar events with descriptions that contain encoded commands.
- Polling and Execution: A compromised machine with GCR running will periodically check these calendar events for new descriptions—that is, for new commands. When it finds them, it executes the commands on the target device.
- Command Results: After executing the commands, the malware updates the event description with the output from the command execution, which can then be read by the attacker.
- Legitimate Infrastructure: Because GCR uses Google’s legitimate infrastructure, it’s harder for network defenders to discern between normal traffic to Google services and malicious C2 communications.
- In the Wild: While Google reported that it hadn’t observed the use of GCR in the wild, it was noted that the proof-of-concept (PoC) exploit was shared on underground forums. This indicates that threat actors are aware of the method and could potentially adopt it for malicious purposes.
- Similar Tactics: Highlighting a similar abuse of cloud services, Google also reported on an Iranian nation-state actor using a small .NET backdoor, BANANAMAIL, which uses IMAP to connect to an email account controlled by attackers for C2 purposes.
- Countermeasures: In response to such threats, Google has taken action by disabling the Gmail accounts associated with the malware, cutting off the C2 communication channel.
This method is part of a broader strategy by threat actors to leverage the ubiquity and trust in cloud services to carry out their operations discreetly.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.