Cybersecurity analysts at Horizon3 detected that thousands of Apache Superset servers are exposed to RCE attacks at default configurations.
This could allow the threat actors to perform the following illicit activities:-
- Access data
- Modify data
- Harvest credentials
- Execute commands
Apache Superset is an open-source tool that is used for:-
- Data visualization
- Data exploration
Initially, this tool was developed for Airbnb, but in 2021, it became a top-level project at the Apache Software Foundation.

Technical Analysis
Attackers could take advantage of the default Flask Secret Key utilized by Apache Superset for signing authentication session cookies to create fake session cookies.
Consequently, servers that haven’t altered the key may be susceptible to unauthorized access with elevated privileges.
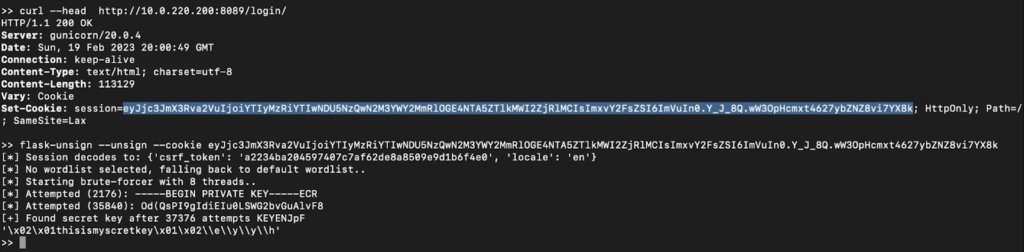
While Horizon3 affirmed that they had identified this vulnerable default configuration in 2,000 internet-exposed servers. Most of these exposed servers belong to several organizations:-
- Universities
- Corporations of varying sizes
- Government organizations
Superset facilitates the exploration of data and the creation of visualizations by supporting integrations with multiple databases.
Attackers can execute arbitrary SQL statements against linked databases using the powerful SQL Lab interface.
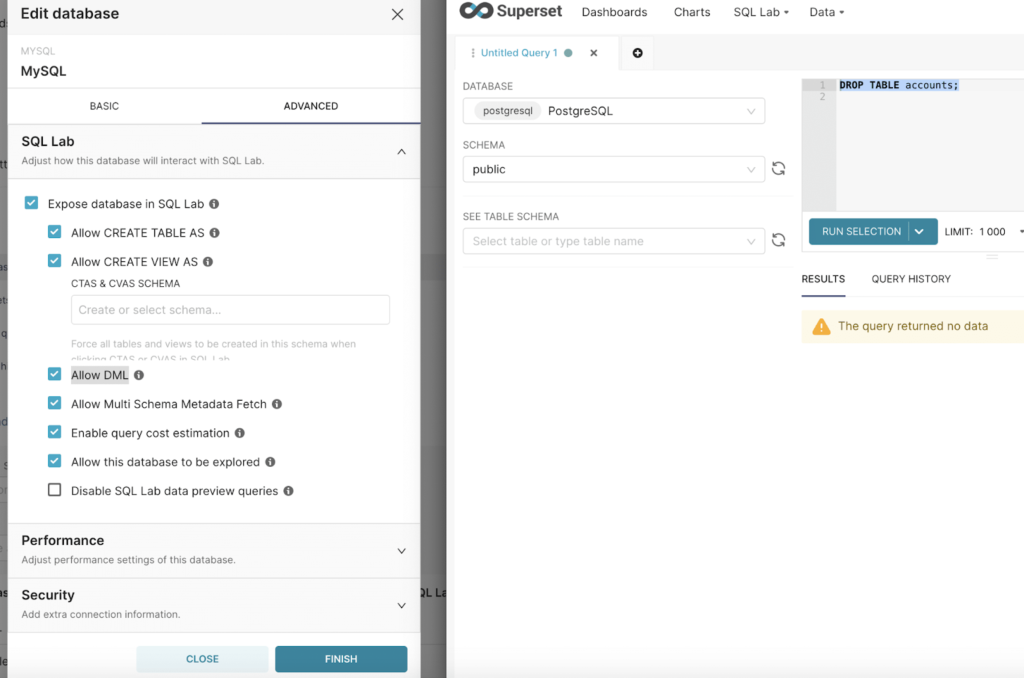
While apart from this, administrators can avoid this attack by changing the default key to an unknown value unfamiliar to the attackers.
Impact
On October 11, 2021, Horizon3 discovered and reported the flaw to the Apache Security team.
The developers released version 1.4.1 of the software on January 11, 2022, which replaced the default ‘SECRET_KEY’ with a new string.
In addition, a warning was included in the logs to indicate the detection of the default string during startup.
Horizon3 found 2 default keys, used Shodan to search instances using them, and found 67% were misconfigured which totals around 2,124 total.
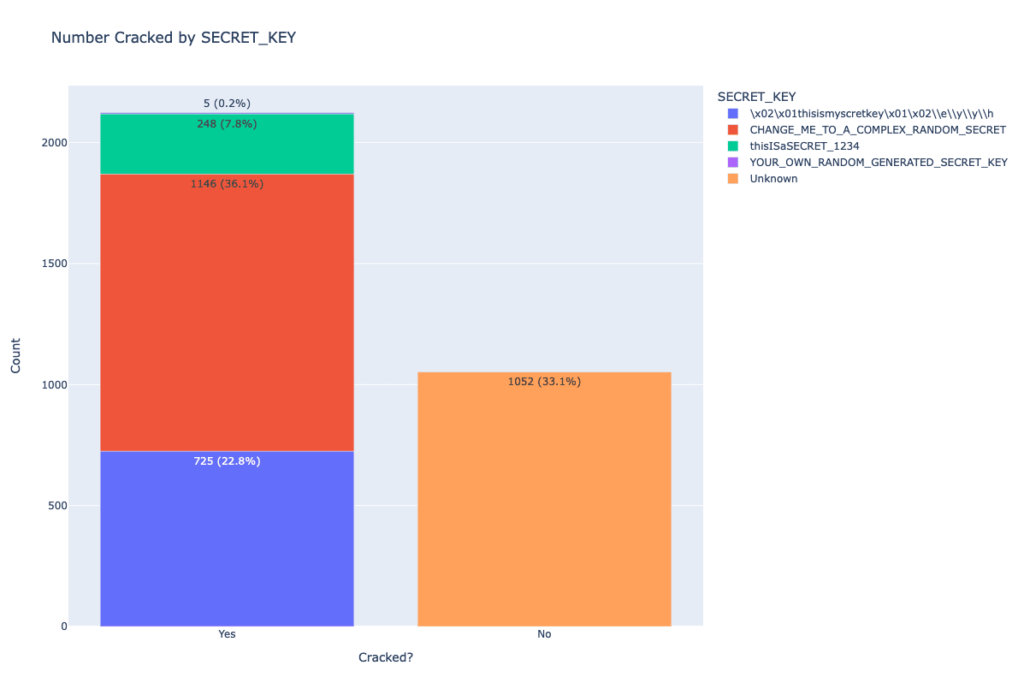
Horizon3 contacted Apache again and warned organizations to change their configuration in February 2023.
On April 5, 2023, the Superset team released version 2.1 which blocks default ‘SECRET_KEY’ at server startup.
Version 2.1 of Superset prevents new risky deployments but doesn’t fix over 2,000 existing misconfigurations.
Timeline
Here below, we have mentioned the complete timeline:-
- Oct. 11, 2021: Initial communication to the Apache Security team
- Oct. 12, 2021: Superset team says they will look into the issue
- Jan. 11, 2022: Superset team changes default SECRET_KEY and adds warning to logs with this Git commit
- Feb. 9, 2023: Email to the Apache Security team about new data related to the insecure default configuration. Started notifying specific organizations.
- Feb. 24, 2023: Superset team confirms code change will be made to address default SECRET_KEY
- Mar. 1, 2023: Pull request merged with a code change to address default SECRET_KEY
- Apr. 5, 2023: Superset 2.1 release
- Apr. 24, 2023: CVE disclosed
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus

