Researchers at the RWTH Aachen University in Germany published a study revealing that tens of thousands of container images hosted on Docker Hub contain confidential secrets, exposing software, online platforms, and users to a massive attack surface.
Docker Hub is a cloud-based repository for the Docker community to store, share, and distribute Docker images. These container-creation templates include all of the necessary software code, runtime, libraries, environment variables, and configuration files to easily deploy an application in Docker.
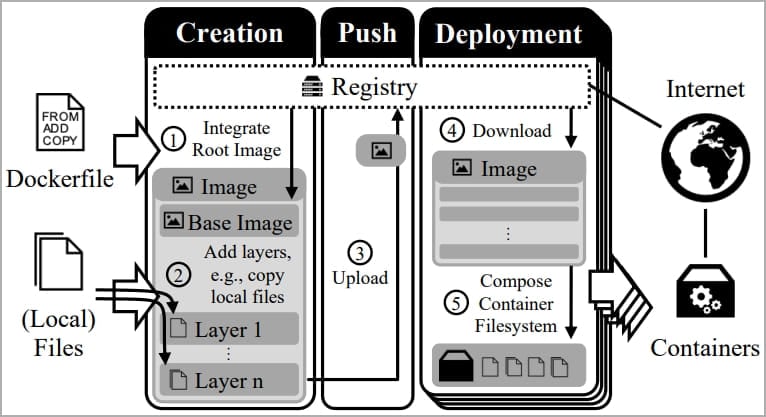
The German researchers analyzed 337,171 images from Docker Hub and thousands of private registries and found that roughly 8.5% contain sensitive data such as private keys and API secrets.
The paper further shows that many of the exposed keys are actively used, undermining the security of elements that depend on them, like hundreds of certificates.
(Inadvertently) exposing secrets
The study assembled a massive dataset of 1,647,300 layers from 337,171 Docker images, sourcing the latest image versions from each repository when possible.
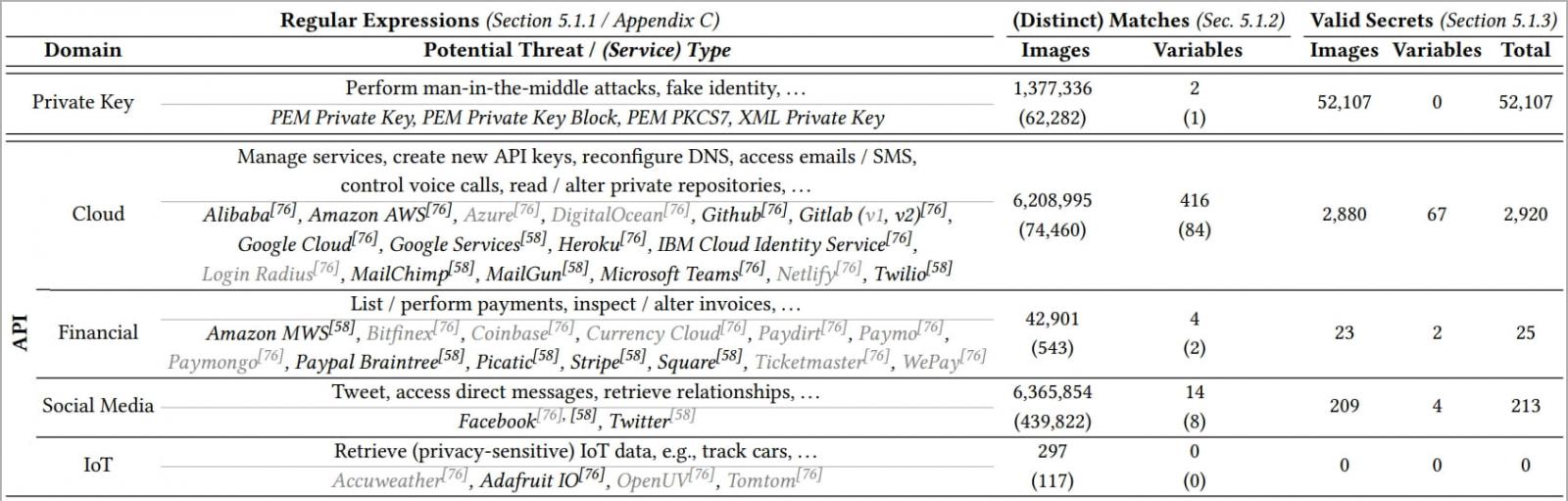
Data analysis using regular expressions to search for specific secrets revealed the exposure of 52,107 valid private keys and 3,158 distinct API secrets in 28,621 Docker images.
The above figures were validated by the researchers excluding test keys, example API secrets, and invalid matches.
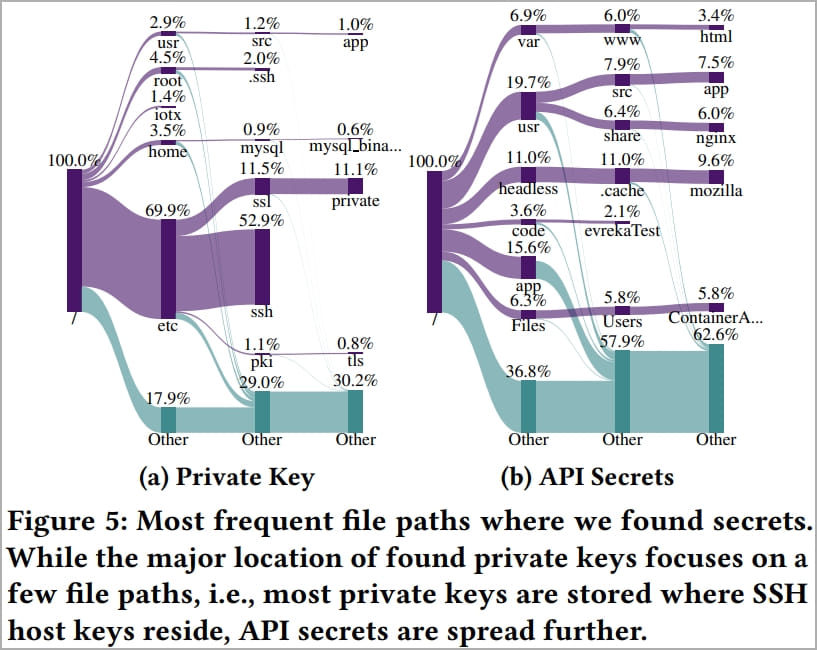
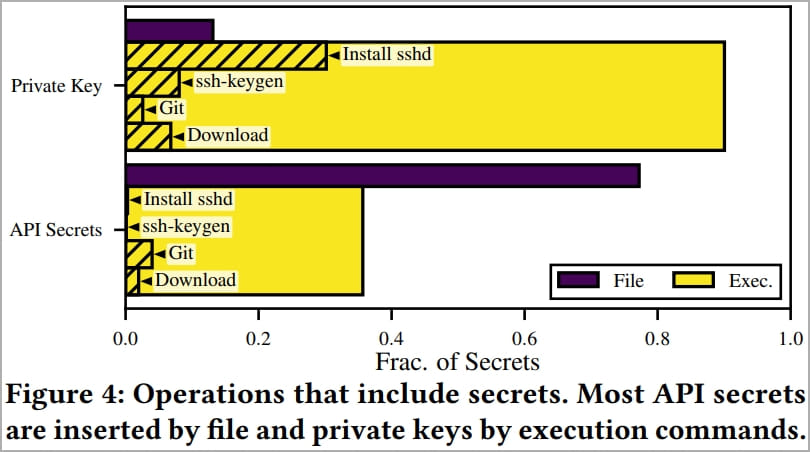
Most of the exposed secrets, 95% for private keys and 90% for API secrets, resided in single-user images, indicating that they were likely unintentionally leaked.
The highest impact was on Docker Hub, which had a percentage of secret exposure of 9.0%, while images sourced from private registries exposed secrets at a rate of 6.3%.
This difference may indicate that Docker Hub users typically have a poorer understanding of container security than those setting up private repositories.
Use of exposed keys
Next, the researchers needed to determine the actual use of the exposed secrets to appreciate the attack surface size.
Alarmingly, 22,082 compromised certificates relying on the exposed private keys were found, including 7,546 private CA-signed and 1,060 public CA-signed certificates.
The thousand CA-signed certificates are of particular concern, as these certificates are typically used by a large number of users and are universally accepted.
At the time of the study, 141 CA-signed certificates were still valid, somewhat lessening the risk.
To further determine the use of the exposed secrets in the wild, the researchers used 15-month worth of internet-wide measurements provided by the Censys database and found 275,269 hosts that rely on the compromised keys.
These include:
- 8,674 MQTT and 19 AMQP hosts that potentially transfer privacy-sensitive Internet of Things (IoT) data.
- 6,672 FTP, 426 PostgreSQL, 3 Elasticsearch, and 3 MySQL instances that serve potentially confidential data.
- 216 SIP hosts used for telephony.
- 8,165 SMTP, 1,516 POP3, and 1,798 IMAP servers used for email.
- 240 SSH servers and 24 Kubernetes instances that use leaked keys which can lead to remote-shell access, extension of botnets, or further data access.
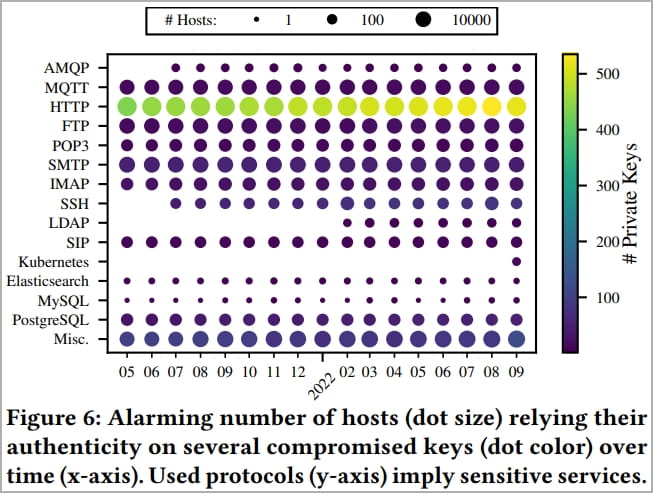
This level of exposure highlights a massive problem in container security and an carelessness on the creation of images without first sanitizing them of secrets.
Regarding the API exposure, the analysis found that most of the containers (2,920) belong to cloud providers like Amazon AWS, but some pertained to financial services such as Stripe.
However, the researchers cited ethical limitations in validating exposed API secrets against their service endpoints, so their use in the wild is unknown.
