Cybersecurity researchers have uncovered a concerning development as malicious actors began exploiting SHELLTER, a commercial anti-virus and endpoint detection response (EDR) evasion framework, to deploy sophisticated malware payloads.
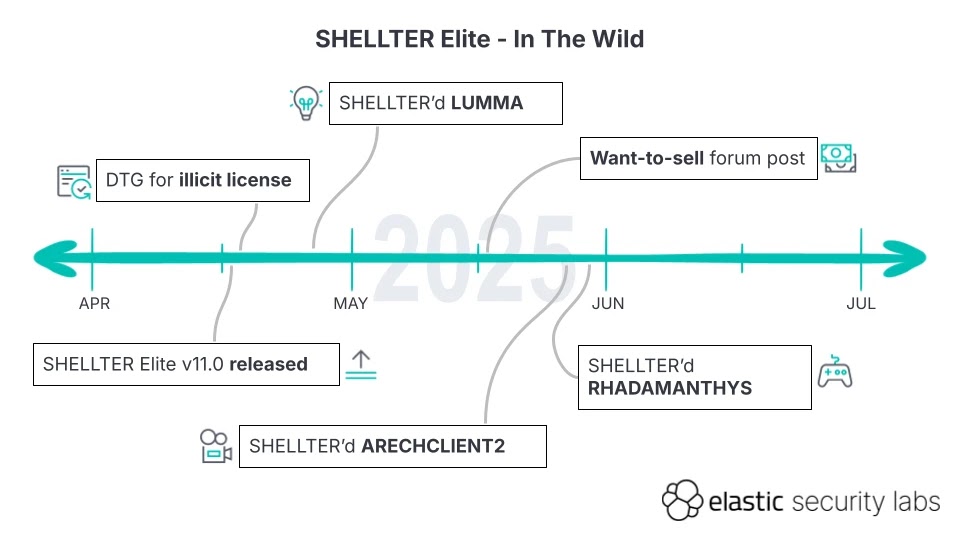
Originally designed for legitimate penetration testing operations, this framework has been weaponized by cybercriminals since late April 2025, marking a significant escalation in evasion capabilities available to threat actors.
The illicit use of SHELLTER represents a troubling trend where legitimate offensive security tools are repurposed for malicious activities.
The commercial framework, specifically Elite version 11.0 released on April 16, 2025, provides advanced capabilities allowing malware to bypass modern security solutions through sophisticated obfuscation and evasion techniques.
Its polymorphic code generation and ability to embed malicious payloads within legitimate applications have made detection significantly more challenging.
Elastic Security Labs researchers identified multiple financially motivated campaigns utilizing SHELLTER-protected payloads, including deployment of notorious information stealers such as LUMMA, RHADAMANTHYS, and ARECHCLIENT2.
These campaigns primarily targeted content creators and gaming communities through carefully crafted phishing emails and malicious links distributed via YouTube comments and file-sharing platforms like MediaFire.
All analyzed samples share a consistent license expiry timestamp of 2026-04-17 19:17:24.055000, suggesting use of a single illicitly acquired license.
.webp)
The distribution strategy demonstrates sophisticated social engineering tactics, with attackers impersonating legitimate brands including Udemy, Skillshare, Pinnacle Studio, and Duolingo.
.webp)
Victims are lured into downloading malicious archive files containing SHELLTER-protected executables, often disguised as promotional content or software updates.
Advanced Evasion Mechanisms and Technical Implementation
The technical sophistication of SHELLTER’s evasion capabilities represents a significant challenge for cybersecurity professionals.
The framework employs AES-128 CBC encryption to protect final payloads, with encryption keys either embedded directly within malware or fetched from attacker-controlled servers.
This dual-key approach provides flexibility while maintaining strong cryptographic protection against analysis efforts.
SHELLTER’s most notable feature is its implementation of polymorphic junk code insertion, generating legitimate-looking instructions that serve no functional purpose other than confusing static analysis tools and signature-based detection systems.
.webp)
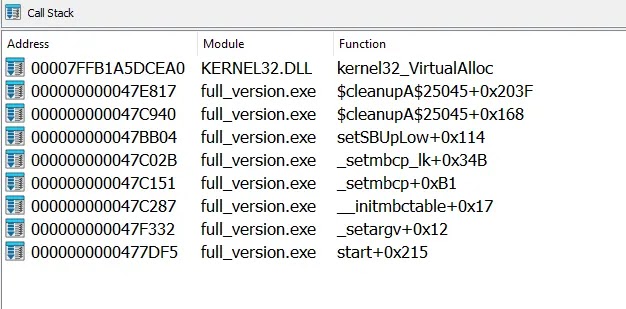
The framework utilizes indirect syscalls and call stack corruption techniques to bypass user-mode API hooking mechanisms commonly employed by EDR solutions.
These techniques involve preparing the stack with addresses of clean syscall instructions from ntdll.dll and using return instructions to redirect execution flow.
The framework’s memory protection mechanisms further complicate analysis through runtime encoding and decoding of critical code sections.
SHELLTER continuously modifies memory page permissions using functions like NtQueryVirtualMemory and NtProtectVirtualMemory, ensuring sensitive code remains obfuscated when not actively executing.
This dynamic protection scheme, combined with virtualized environment detection and debugging tool identification, creates multiple defense layers against security researchers and automated analysis systems.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
