Threat actors have claimed responsibility for a massive data breach involving 1.1TB of Disney’s internal Slack chats.
The breach, first reported on July 12 by a hacktivist named NullBulge on a dark web forum, has sent ripples through the cybersecurity community and raised concerns about the security of corporate communication platforms.

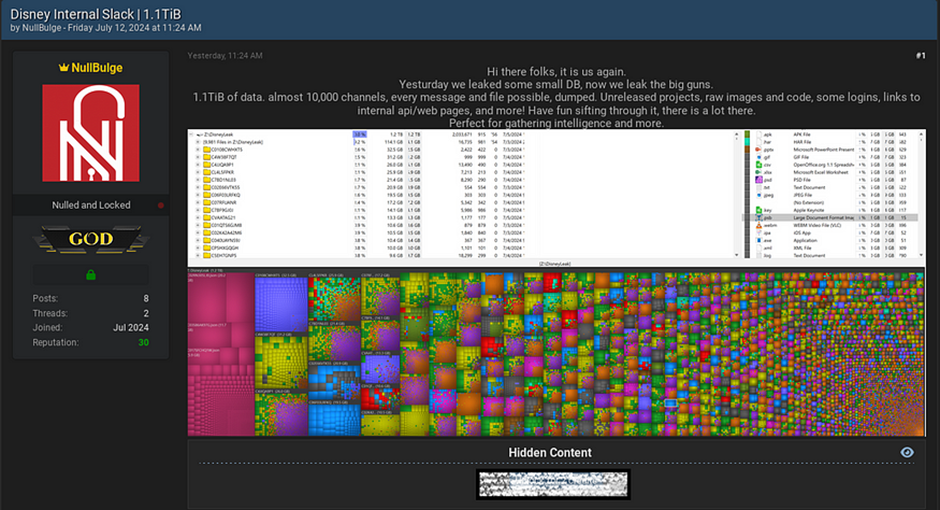
The original post, shown above, detailed that the leaked database includes every message and file from nearly 10,000 channels.
The data purportedly contains unreleased projects, raw images, code, logins, and links to internal APIs.
According to NullBulge, the breach resulted from the Club Penguin fans’ intrusion into Disney’s corporate servers almost exactly a month ago.
NullBulge claims that “Our mission is to enact ways to ensure that theft from artists is reduced and to promote a fair and sustainable ecosystem for creators. Our hacks are not those of malice, but those to punish those caught stealing. Big and small theft, meet the same fate. Be wary where you get content from, because we will work tirelessly to develop and implement solutions that protect the rights and livelihoods of artists in the digital age.”
Are you from SOC/DFIR Teams? - Sign up for a free ANY.RUN account! to Analyse Advanced Malware Files
“Now We Leak the Big Guns”
The threat actors have been vocal about the scale of the breach. Their post stated, “Now we leak the big guns,” indicating that the initial estimate of the data leak at 2.6GB was grossly underestimated.
The actual size of the breach, at 1.1TB, is significantly larger and more damaging than initially thought.
This revelation has sparked a flurry of activity on various dark web forums, with more posts like the one shown below appearing, suggesting that the data has already been widely disseminated within the dark web community.
Researchers at Cyber Press discovered an Excel document that includes the admin username and password in plain text for various platforms such as AmericanExpress.com, T-Mobile, Mailchimp, OpenAI, Namecheap, and others.

The initial breach into Disney’s corporate servers was reportedly carried out by individuals associated with the Club Penguin fan community. Club Penguin, a popular online game once owned by Disney, has a dedicated fan base, some of whom may possess advanced technical skills.
Once the attackers gained access to Disney’s corporate servers, they were able to infiltrate the internal communication systems, including Slack.
The claimed database contains files, unreleased projects, raw images, code, logins, and links to internal APIs.
The attackers could have used several methods to access this data:
- Credential Theft: The attackers might have stolen login credentials through phishing attacks or by exploiting weak password policies.
- Exploiting API Vulnerabilities: Slack APIs, if not properly secured, can be a gateway for attackers to access internal data. The attackers might have found and exploited such vulnerabilities.
- Lateral Movement: After gaining initial access, the attackers could have moved laterally within Disney’s network to find and extract data from Slack channels.
Cybersecurity experts are urging companies to bolster their security measures, particularly for internal communication tools like Slack, to prevent similar breaches in the future.
Disney has yet to release an official statement regarding the breach.
"Is Your System Under Attack? Try Cynet XDR: Automated Detection & Response for Endpoints, Networks, & Users!"- Free Demo
