Threat actors were discovered disseminating a malicious, altered version of SonicWall’s SSL VPN NetExtender application in a complex cyberattack that was discovered through a partnership between SonicWall and Microsoft Threat Intelligence (MSTIC).
NetExtender, a critical tool for remote users, facilitates secure connections to corporate networks, enabling seamless access to applications, file transfers, and network resources as if on a local network.
Deceptive Campaign Targets Remote Access Software
However, this deceptive campaign hosts a Trojanized variant of NetExtender version 10.3.2.27 the latest official release on a fraudulent website mimicking SonicWall’s legitimate platform.
The installer, digitally signed by “CITYLIGHT MEDIA PRIVATE LIMITED,” has been flagged as malicious by both SonicWall (GAV: Fake-NetExtender [Trojan]) and Microsoft Defender Antivirus (TrojanSpy:Win32/SilentRoute.A).
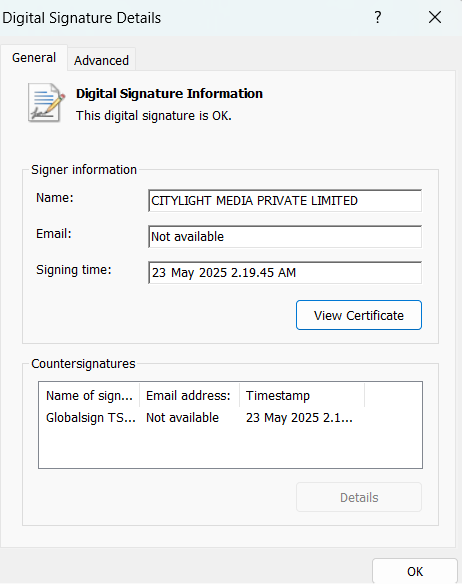
Delving into the technical intricacies, the threat actors have tampered with two core components of the NetExtender installer: NeService.exe and NetExtender.exe.
NeService.exe, the Windows service responsible for running the NetExtender application, includes a function for validating digital certificates of associated components.
In the malicious version, this validation mechanism has been deliberately patched to bypass checks, ensuring the program executes regardless of certificate authenticity.
This tampering allows the compromised software to evade early detection during installation.
Technical Breakdown of the Malicious Modifications
Meanwhile, NetExtender.exe has been injected with additional malicious code designed to exfiltrate sensitive VPN configuration data including usernames, passwords, and domain details to a remote server at IP address 132.196.198.163 over port 8080.

This data theft is triggered as soon as a user inputs credentials and clicks the “Connect” button, with the stolen information undergoing custom validation by the malware before transmission.
The implications of this attack are severe, as compromised VPN credentials can grant attackers unauthorized access to corporate networks, potentially leading to data breaches, lateral movement, and further exploitation.
What makes this campaign particularly insidious is the near-identical appearance of the fake installer to the legitimate software, increasing the likelihood of users falling victim to the ruse.
SonicWall and Microsoft have responded swiftly by working to dismantle the impersonating websites and revoking the fraudulent digital certificate used by the malicious installer.
Their proactive measures include deploying detection mechanisms in security solutions to block this threat at multiple layers.
To safeguard against such attacks, users are urged to exercise extreme caution and download SonicWall applications exclusively from trusted sources, namely sonicwall.com or mysonicwall.com.
SonicWall’s Capture ATP with Real-Time Deep Memory Inspection (RTDMI) and Managed Security Services are equipped to identify and neutralize this threat, underscoring the importance of leveraging updated security tools.
As cyber adversaries continue to exploit trusted software for nefarious purposes, this incident serves as a stark reminder of the evolving threat landscape and the critical need for vigilance in software acquisition and network security practices.
Indicators of Compromise (IOCs)
| Type | Value |
|---|---|
| SHA256 (Installer) | d883c067f060e0f9643667d83ff7bc55a218151df600b18991b50a4ead513364 |
| SHA256 (NEService.exe) | 71110e641b60022f23f17ca6ded64d985579e2774d72bcff3fdbb3412cb91efd |
| SHA256 (NetExtender.exe) | e30793412d9aaa49ffe0dbaaf834b6ef6600541abea418b274290447ca2e168b |
| Network (IP Address) | 132.196.198.163 |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
