The Socket Threat Research Team has uncovered a surge in supply chain attacks where threat actors weaponize open source software libraries to deliver malicious payloads such as infostealers, remote shells, and cryptocurrency drainers.
With modern development heavily reliant on ecosystems like npm, PyPI, Go Module, Maven Central, and RubyGems where 70–90% of codebases consist of third-party packages the implicit trust in these dependencies has become a prime target for exploitation.
The complexity of dependency graphs, exemplified by tools like npmgraph.js.org for the popular express package, illustrates how a single library can pull in dozens of nested dependencies, each a potential entry point for attackers.
This vast and shifting attack surface, compounded by developers rarely inspecting transitive dependencies and AI tools accelerating both legitimate and malicious activities, has enabled adversaries to infiltrate software supply chains with alarming precision.
Techniques Target Developer Ecosystems
Threat actors employ a range of sophisticated techniques to maximize their impact across package registries, as detailed in Socket’s research.
Typosquatting, for instance, involves registering packages with names nearly identical to popular libraries such as “metamaks” mimicking “metamask” exploiting lexical similarity in search results and developer oversight, often amplified by overconfident AI code assistants.
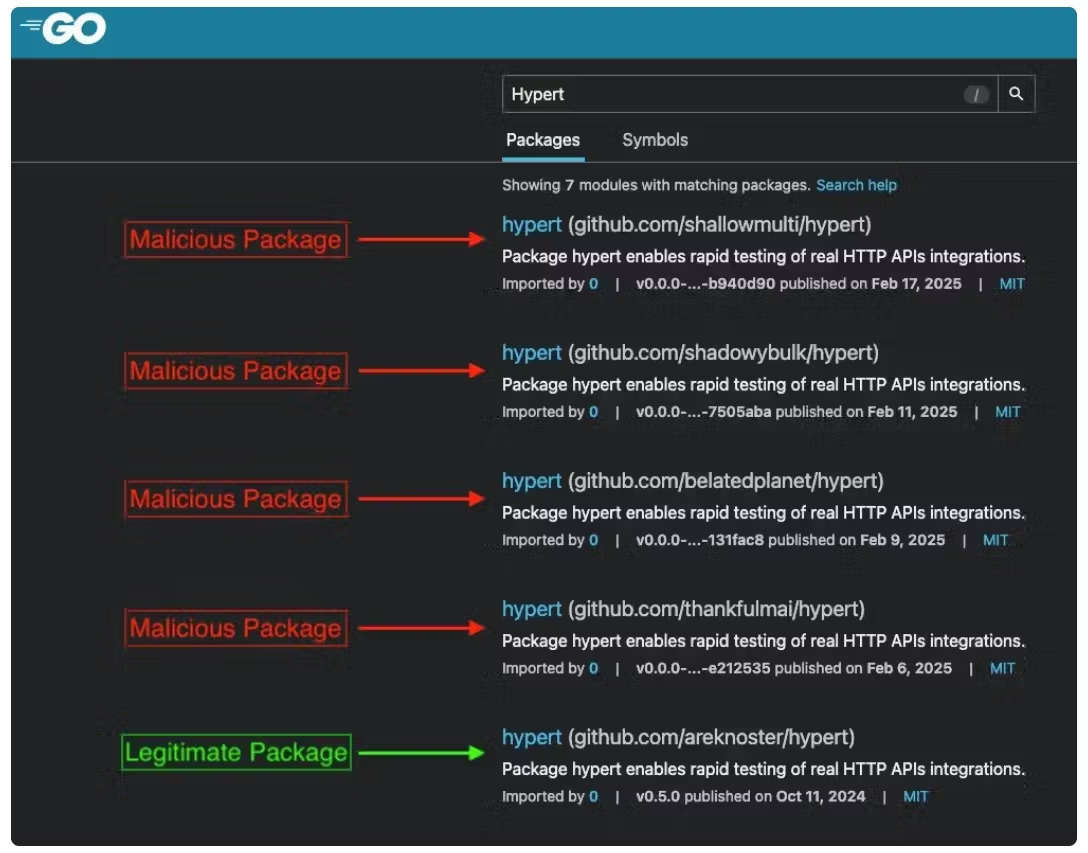
In one PyPI incident, a typosquatted package harvested Chrome credentials and exfiltrated data via Discord webhooks.
Similarly, repository and caching abuse, like the three-year persistence of a backdoored clone of boltdb/bolt in the Go Module Mirror, demonstrates how infrastructure meant for efficiency can be turned against users, enabling remote code execution through hidden command-and-control (C2) servers.
Obfuscation techniques further conceal malicious behavior by using randomized variable names, compressed code, and encoded payloads to evade static analysis, while multi-stage malware, such as the North Korean-linked BeaverTail loader, delays harmful actions by fetching advanced backdoors like InvisibleFerret post-installation.
Multi-Layered Attack Vectors Evade Detection
Moreover, automation and AI have supercharged attackers’ capabilities, allowing them to mass-produce typosquatted packages, obfuscate code with hidden shell commands, and deploy hundreds of malicious packages in hours, as seen in a campaign that published 280 npm packages over a weekend.
AI’s darker side also emerges through “slopsquatting,” where threat actors register hallucinated package names suggested by language models, while search engines like Google’s AI Overview inadvertently boost malicious packages by echoing legitimate README content.

Finally, the abuse of trusted services-such as using nodemailer to exfiltrate Solana keys via Gmail or repurposing Sentry for fake error reports highlights how legitimate tools are weaponized for covert C2 channels, blending malicious traffic into routine network activity.
According to the Report, Socket’s defensive recommendations urge developers to automate checks for lookalike names, monitor install-time network behavior, sandbox runtime actions, and scrutinize outbound connections to trusted domains.
As open source ecosystems continue to underpin modern software, these evolving threats underscore the urgent need for vigilance and robust security measures to protect the integrity of development pipelines from increasingly cunning supply chain attacks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!




