A sophisticated threat actor has orchestrated a multi-stage ransomware attack spanning nine days, leveraging compromised Remote Desktop Protocol (RDP) credentials to infiltrate a corporate network, exfiltrate sensitive data, and deploy Lynx ransomware across critical infrastructure.
The attack initiated with a successful RDP login using pre-compromised credentials a critical indicator that the threat actor obtained valid authentication details through an initial access broker, credential-stealing malware, or reused passwords from previous data breaches.
The intrusion demonstrates a methodical approach combining hands-on keyboard activity with legitimate tools for reconnaissance and lateral movement.
Notably absent were any failed authentication attempts, suggesting the attacker possessed working credentials before launching the assault.
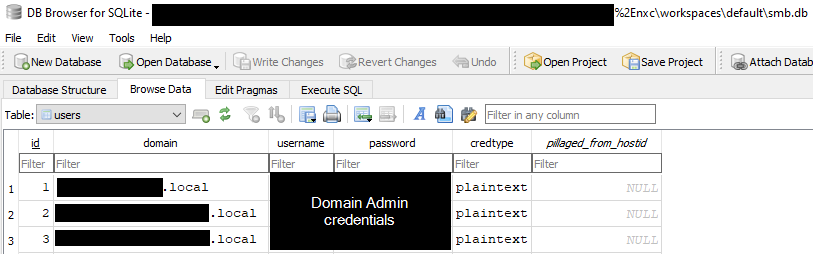
Within ten minutes of initial access, the threat actor escalated privileges by connecting to a domain controller using separate compromised domain administrator credentials.
This quick pivot to privileged infrastructure reveals the attacker’s preparedness and access to multiple credential sets.
Once on the domain controller, the threat actor established persistence by creating three new user accounts with names mimicking legitimate system accounts: “administratr,” “Lookalike 1,” and “Lookalike 2.”
All three accounts were configured with non-expiring passwords and added to privileged security groups, including Domain Administrators, ensuring lasting access even if initial credentials were discovered.
Systematic Network Reconnaissance
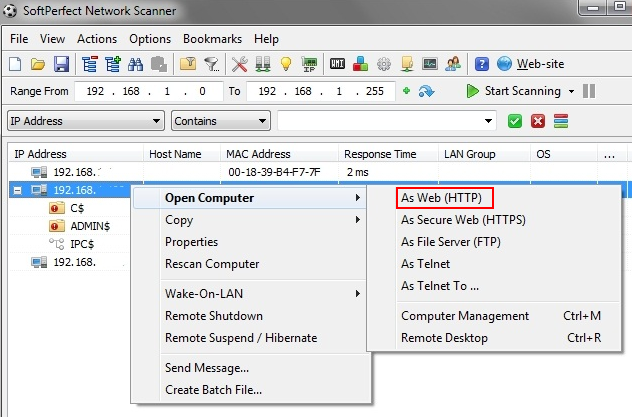
Over the following six days, the threat actor conducted extensive network reconnaissance using SoftPerfect Network Scanner configured with domain administrator credentials.
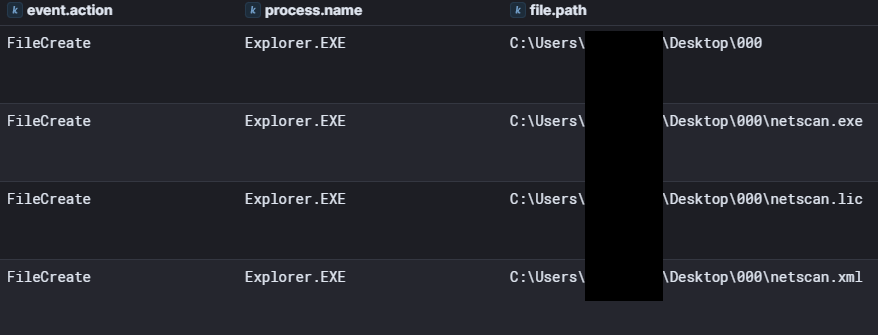
The scanner was meticulously configured to enumerate file shares, workstations, and network infrastructure across the entire environment.
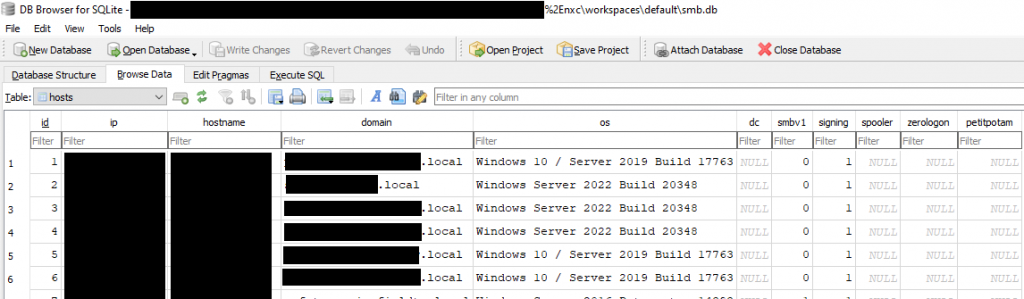
Supplementing this tool, the attacker deployed NetExec, a network exploitation utility, to perform password spraying and SMB enumeration across port 445, successfully identifying multiple domain controllers, hypervisors, and file servers.
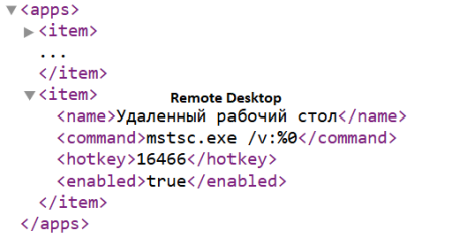
Netscan also had default hotkeys enabled for Remote Desktop and Computer Management, mapped to CTRL + R and CTRL + M.

The reconnaissance activities were interspersed with visits to backup servers, hypervisor infrastructure, and network appliances, including firewalls and VPN devices.
On day six, the threat actor targeted multiple file servers, using 7-Zip to compress sensitive files from network shares into archives before uploading them to temp.sh, a temporary file-sharing service.
Numerous visits to the upload portal correlated with the creation of several large archives, confirming the exfiltration of substantial amounts of data.
Microsoft Management Console with the Active Directory Users & Computers snap‑in (dsa.msc), allowing them to browse and manipulate AD objects.
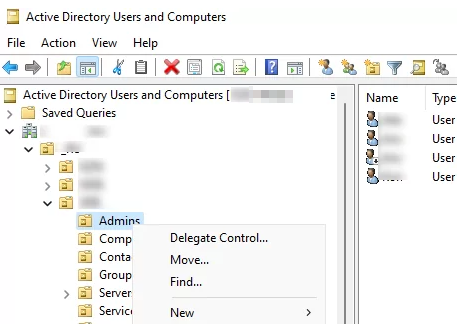
The attack reached its climax on day nine when the threat actor connected to backup servers via RDP and executed a devastating two-pronged strategy.
First, using the Veeam Backup & Replication console, they deleted existing backup jobs and removed backups from the configuration database effectively eliminating the organization’s recovery options.
This action is critical to ransomware operators, as it eliminates the victim’s ability to restore systems without paying the ransom.
Immediately following backup destruction, the threat actor deployed Lynx ransomware executable “w.exe” across multiple backup and file servers.
Infrastructure and Attribution
The ransomware was executed with parameters specifying target directories (E: drives), fast encryption mode (5% of files), and suppression of printer ransom notes.
The threat actor used the open ‘As Web (HTTP)’ shortcut within the Netscan GUI to view the appliances’ web portals in the browser.
The Time to Ransomware (TTR) from initial access to encryption was approximately 178 hours, distributed across nine calendar days allowing sufficient time for reconnaissance while maintaining operational security.
All attacker activity originated from IP addresses hosted on Railnet LLC infrastructure, identified as a front for Virtualine, a Russia-based bulletproof hosting provider known for enabling cybercriminal activity.
The consistent use of the same hostname “DESKTOP-BUL6K1U” across sessions and the methodical approach suggest either a single operator or a well-coordinated team with detailed preparation and pre-existing network access.
This intrusion underscores the critical importance of enforcing multi-factor authentication on RDP endpoints, maintaining comprehensive backup redundancy offline, and implementing robust credential hygiene practices to prevent the initial compromise.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
