DocuSign has emerged as a cornerstone for over 1.6 million customers worldwide, including 95% of Fortune 500 companies, and boasts a user base exceeding one billion.
However, this widespread adoption has made DocuSign a prime target for cybercriminals.
Leveraging the platform’s trusted reputation, threat actors are increasingly deploying sophisticated phishing campaigns to harvest corporate credentials, infiltrate networks, and execute financial fraud.
Rising Cyber Threats Targeting a Trusted Platform
As phishing accounts for 19% of data breaches and 60% involve a human element, per Verizon’s findings, understanding these threats is critical for organizations aiming to safeguard sensitive data.
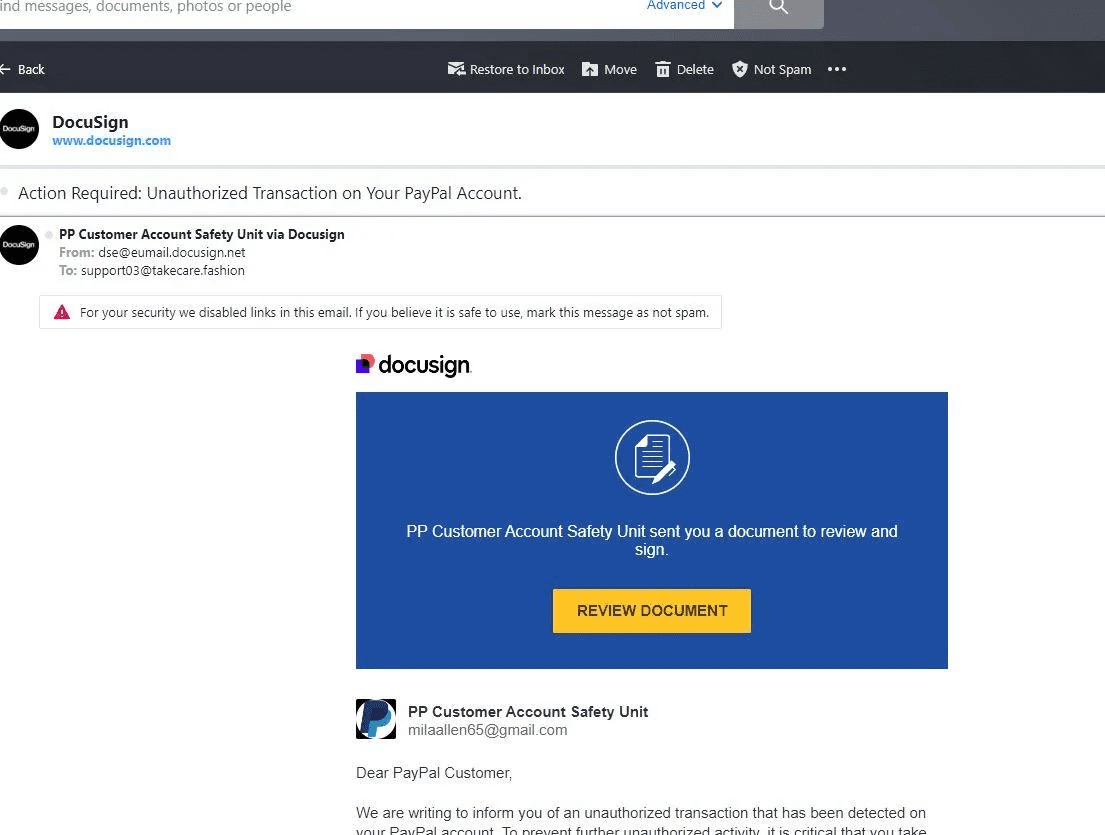
DocuSign-themed phishing campaigns employ social engineering tactics to deceive users into compromising their security.
Victims often receive emails mimicking legitimate DocuSign “envelopes,” complete with urgent prompts to “review documents” via clickable yellow buttons or QR code attachments.
These lead to malicious sites, such as counterfeit Microsoft login pages, where users are tricked into entering credentials or financial details.
QR codes pose a unique risk, as mobile devices used to scan them often lack robust security software, making it easier for attackers to bypass defenses.
Beyond data theft, these attacks can serve as entry points for privilege escalation, lateral movement within corporate networks, and even ransomware deployment or data exfiltration.
Example of a scam abusing people’s trust in Docusign for data theft
Mechanisms of DocuSign-Themed Phishing Attacks
Recent incidents highlight the diversity of these scams, with cybercriminals registering real DocuSign accounts to send authentic-looking envelopes spoofing trusted entities like suppliers or municipal agencies.
Others orchestrate fake invoice scams to trick companies into transferring funds or employ refund frauds that coax victims into divulging personal information over the phone.
Additionally, some attackers exploit DocuSign’s APIs to craft seemingly legitimate notifications, blending authenticity with deception.
These emails may impersonate HR or payroll departments, creating a sense of urgency that prompts users to act without scrutiny.
The result is often unauthorized access to corporate systems, financial losses, or stolen personal data surfacing on the dark web.
For businesses, the stakes are high, as a single compromised account can cascade into a full-scale breach.
According to ESET Report, protecting against DocuSign phishing requires a multi-layered approach.
Organizations must prioritize employee education through updated phishing awareness programs, teaching staff to scrutinize emails for suspicious sender addresses, mismatched signatures, or grammatical errors, and to verify destination URLs before clicking links.
Legitimate DocuSign emails include security codes for direct document access on their platform, never through email links or initial attachments.
Implementing multi-factor authentication (MFA) across corporate accounts, enforcing strong password hygiene via managers, and deploying advanced security solutions like ESET for malicious link and attachment detection are essential technical safeguards.
Policies should discourage interaction with unsolicited emails, encouraging users to report suspicious messages to IT teams and DocuSign’s spam reporting address.
If a breach occurs, swift action such as password resets, malware scans, device isolation, and dark web monitoring is crucial to contain damage and inform future prevention strategies.
Whether used for business or personal purposes, DocuSign’s convenience must be balanced with vigilance to outmaneuver cybercriminals exploiting trust in digital tools.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
