Cybersecurity researchers have uncovered a sophisticated malware campaign where threat actors are exploiting Hangul Word Processor (.hwp) documents to distribute the notorious RokRAT malware.
This marks a significant shift from the malware’s traditional distribution method through malicious shortcut (LNK) files, demonstrating the evolving tactics of advanced persistent threat groups.
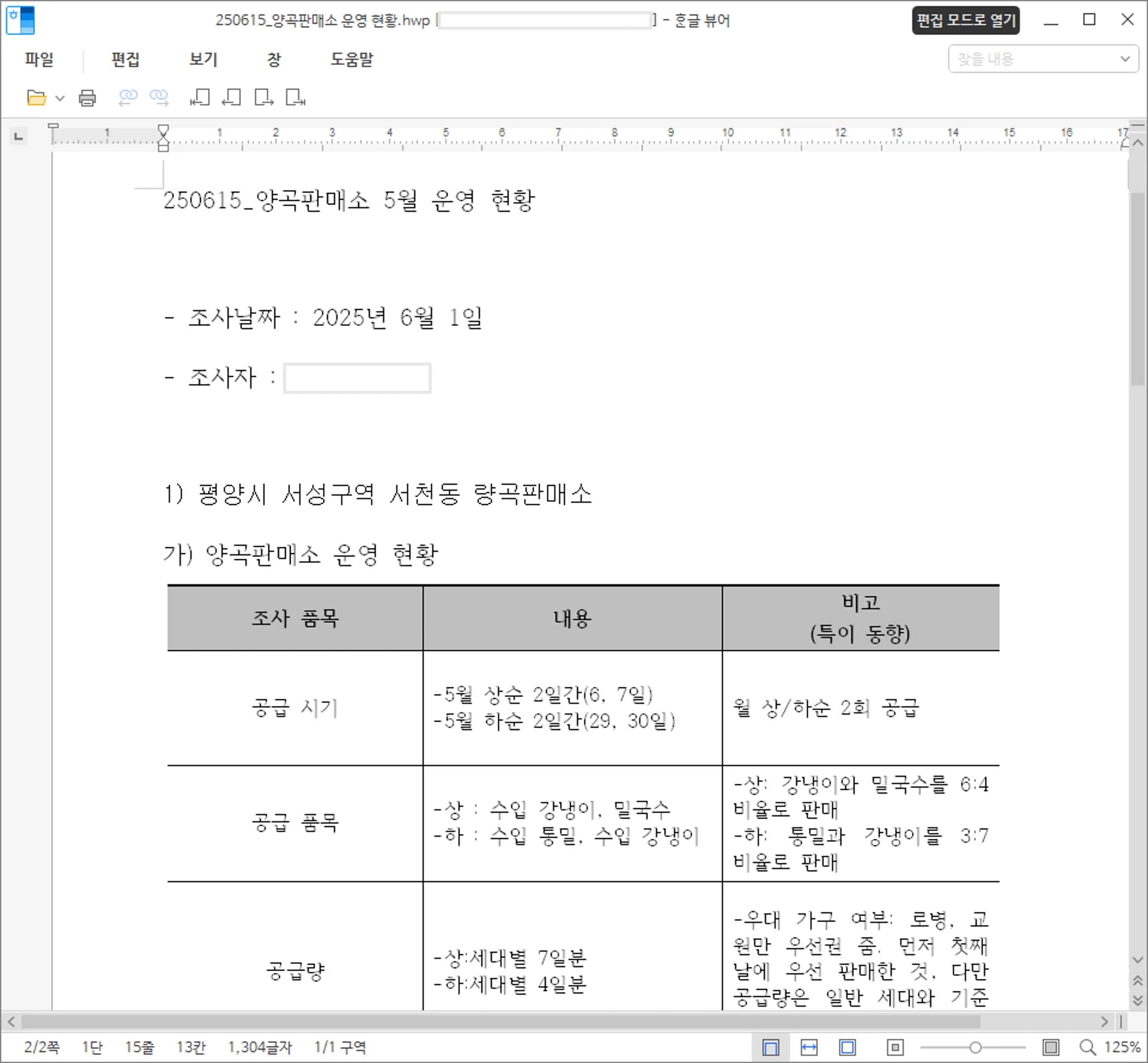
The attack campaign utilizes carefully crafted social engineering lures with document names such as “250615_Operation status of grain store.hwp” and “[Notice] Q1 VAT Return Filing Deadline (Final)” to entice victims into opening malicious attachments.
.webp)
These documents contain seemingly legitimate content about North Korean grain distribution points, effectively masking their malicious intent while building credibility with targeted users.
ASEC analysts identified that the malware leverages a sophisticated technique involving embedded OLE (Object Linking and Embedding) objects within the HWP documents.
.webp)
When victims access the document page containing these objects, the Hangul process automatically creates malicious files including ShellRunas.exe and credui.dll in the system’s temporary directory (%TEMP% path).
The attack chain concludes with victims clicking a hyperlink labeled “[Appendix] Reference Materials.docx” at the document’s bottom, triggering a security warning that prompts execution of the embedded malware components.
DLL Side-Loading Attack Mechanism
The malware employs a sophisticated DLL side-loading techniqueables to bypass security controls.
.webp)
The primary attack vector utilizes ShellRunas.exe, a legitimate Windows utility, which automatically loads the malicious credui.dll from the same directory path.
Legitimate Program: ShellRunas.exe (Microsoft-signed)
Malicious Payload: credui.dll (loaded via DLL side-loading)
Final Stage: Downloads Father.jpg containing RokRAT shellcodeThis technique allows threat actors to execute malicious code while appearing to use trusted system components, significantly complicating detection efforts and enabling the deployment of RokRAT’s comprehensive data collection capabilities.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
