Hacking group Team1919 has claimed to successfully executed a cyber attack on BredBand2 AB, one of Sweden’s prominent internet service providers.
Threat intelligence service Falcon Feed took to Twitter to announce the BredBand2 AB cyber attack, sharing details about the security incident.
Alongside the tweet, they also posted a screenshot displaying the hacker group’s claim of breaching the security systems of the Swedish internet provider.
The Cyber Express has reached out to the internet provider to learn more about the alleged cyber attack on BredBand2 AB. However, no official response has been received from the company at the time of writing.

The threat actor first declared the BredBand2 AB cyber attack on their Telegram channel, stating, “We have hacked the Industrial Communication System of Sweden, which belongs to the organization of BredBand2 AB. We will soon release a video demonstrating how we can manipulate their systems. Team1919.”
Cyber attack on BredBand2 AB, but who is Team1919?
BredBand2 AB is a renowned internet service provider in Sweden that offers many communication services, including high-speed fiber broadband connections and communication solutions.
The alleged cyber attack on BredBand2 AB puts the company data at risk and the customers who rely on the company’s services.
The identity and motives of Team1919 are still unknown. This hacker group emerged on the cybersecurity radar in 2023, with attacks primarily focusing on defacing websites.
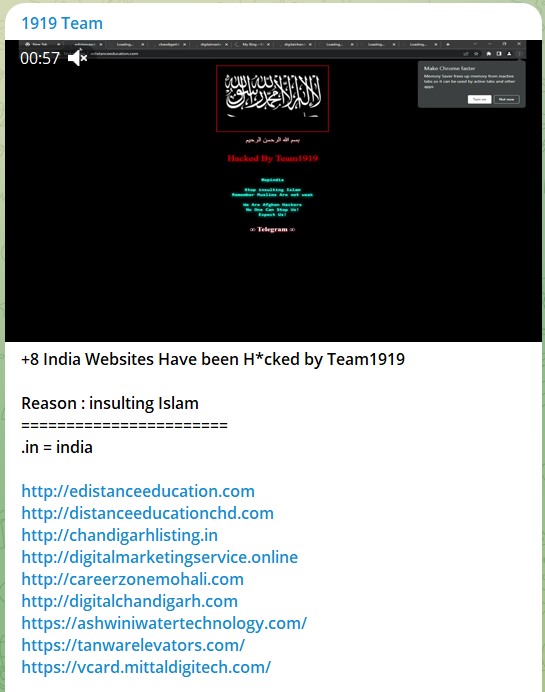
On April 1, 2023, Falcon Feed reported another incident involving this notorious threat actor. The group claimed responsibility for hacking and defacing the websites of nine small businesses based in India.
Interestingly, Team1919 operates a Facebook page where they frequently post about their cyber attacks.
However, it is noteworthy that the page only has 249 followers and often switches languages in its posts, leading to speculation about their origins and affiliations.
The group seems to exhibit a pattern of targeting Indian organizations while promoting Afghanistan, although these assumptions remain unverified.
Unraveling the Actions of Team1919: A Closer Look
On June 12, 2023, the hacker group boasted about their successful targeting of “The National Site Of Ministry Of Defence,” alleging that it had been under a distributed denial-of-service (DDoS) attack from 9 PM to 10 PM.
Their motive behind this attack was purported to draw attention to the concerns of Afghan people regarding the girls’ education system, urging the government of Afghanistan to address these issues.
“The former governor of Nangarhar, Ziaulhaq Amarkhil, wrote: Hijab is the jewel of our society, no one is against it. Depriving girls of education due to hijab or on any other pretext has upset the whole people, so upset that no big project can be opened. #LetAfghanGirlLearn” the group posted on its Telegram channel.
Curiously, the same progressive outlook was hardly visible during its attacks on other countries, including India, as a retort for Islamophobic acts.
The threat actor has claimed multiple attacks via its Telegram and Facebook pages, where the motive behind these attacks has been credited to patriotism, but in other posts, the threat actor claims to target the companies without any serious motive.
Moreover, Team1919 has been posing themselves as the “voice of their nation,” which is evident in the patriotism-based post made by the threat actor on their Telegram channel.
Several threat actors, mainly Anonymous Sudan, has driven the Islamophoic bandwagon to attack nation states, but most of them were found to have other vested interests, promoted by Russia.
However, Anonymous Sudan has been continuously directing its attacks towards Israel and India, both of which have recently established friendly relations with Russia. This complicates efforts to discern the true intentions of the group and identify any discernible patterns in their assaults.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.