The MOVEit transfer service pack has been found to have three vulnerabilities, namely two SQL injections and one instance of Reflected Cross-Site Scripting (XSS). The vulnerabilities exhibit a variety of severity levels, spanning from 6.1 (Medium) to 8.8 (High). The MOVEit transfer service, which is operated by Progress, saw widespread exploitation by malicious actors that targeted many enterprises in a ransomware operation. The MOVEit vulnerability has reportedly impacted many firms, include Shell, BBC, British Airways, CalPERS, Honeywell, and other US government institutions. Progress has just issued a security alert with an exhaustive inventory of the products that have been impacted, along with a detailed enumeration of the vulnerabilities that have been discerned.
The vulnerability identified as CVE-2023-42660 pertains to a SQL injection vulnerability in MOVEit Transfer.
The presence of a SQL injection vulnerability was identified inside the MOVEit Transfer machine interface, potentially enabling unauthorized access to the MOVEit Transfer database. The vulnerability in question might be exploited by a threat actor via the submission of a well constructed payload to the MOVEit Transfer machine interface.
The potential outcome of a successful exploitation is the alteration and exposure of the MOVEit database’s content. Nevertheless, in order to exploit this vulnerability, it is required for a threat actor to undergo authentication. The severity of this vulnerability has been assessed as 8.8 (High) by the organization monitoring progress.
The products that are impacted by this issue include MOVEit Transfer, including MySQL and MSSQL databases, across all versions. It is recommended for users to update to the September Service Pack in order to address this issue.
The vulnerability identified as CVE-2023-40043 pertains to a SQL injection flaw in MOVEit Transfer.
The MOVEit Transfer online interface has an additional SQL injection vulnerability that has the potential to result in unauthorized access to the MOVEit Transfer database. The vulnerability in question may be exploited by a malicious actor that submits a well prepared payload to the online interface of MOVEit Transfer.
The potential outcome of a successful exploitation is the alteration and exposure of the MOVEit database’s content. In order for a threat actor to exploit this vulnerability, it is necessary for them to possess access to a MOVEit system administrator account. The severity of this vulnerability has been assessed by Progress as 7.2, indicating a high level of risk.
The products impacted by this issue include MOVEit Transfer, including MySQL and MSSQL databases, across all versions. In order to mitigate this issue, it is advised that users upgrade to the September Service Pack and restrict access to the administrator account.
The identified vulnerability, CVE-2023-42656, pertains to a reflected cross-site scripting (XSS) issue in MOVEit Transfer.
The identified vulnerability is a Reflected Cross-Site Scripting (XSS) in the online interface of MOVEit Transfer. This vulnerability may be exploited by a malicious payload during the package construction phase. A potential adversary have the capability to create a harmful payload with the intention of specifically targeting users of MOVEit Transfer. The threat actor has the ability to run malicious JavaScript on the victim’s browser during the interaction with the payload.
The severity of this vulnerability has been assessed by Progress as 6.1, indicating a medium level of severity. The vulnerability in question has a significant impact on several products, including MOVEit Transfer and either MySQL or MSSQL DB, across all versions. In order to mitigate this issue, it is advised that users upgrade to the September Service Pack and restrict access to the administrator account.
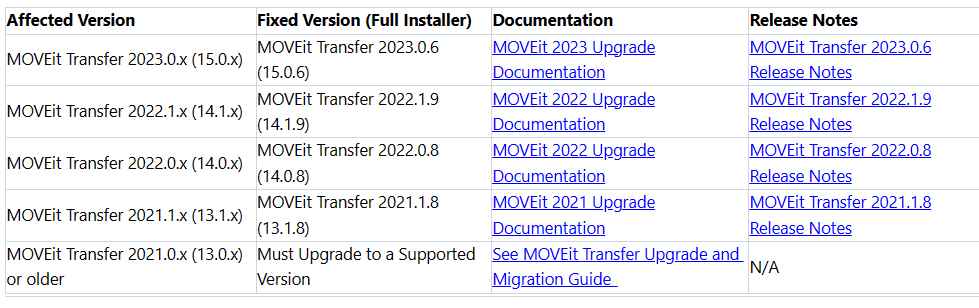
Below, we provide a thorough compilation of susceptible product versions, documentation, release notes, and corrected versions.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.




