I hope you’ve been doing well!
The “Full Utah” Experience
Last weekend I got to hang out with my friend Scott Piper, and he gave me the “full Utah” experience.
I felt a sense of peace dirt biking down a gravelly dirt road in the desert, with the wind in my hair and a dog running in front of me, chasing a wild antelope.
I waved to the families chilling by their trucks in an outcroppings of trees, who’d smile and wave back.
Later, I saw this on a car:
Not the type of bumper sticker you’d typically see in San Francisco 😆
Differences, in any relationship (friendship, romantic, political, etc.), can cause friction.
But they’re also a source of growth, and make us better.

Scott and I slaying 3 pizzas.
P.S. Thank you so much to everyone who attended Daniel Miessler and I’s webinar yesterday on AI + security 🙏 So many great questions and ideas! I’ll share more next week.
📣 Secure it, torch it, or hope for the best
Material offers a novel approach to classifying and securing sensitive data in employee mailboxes.
We all know that employees’ cloud email accounts are rich and vulnerable targets. We try to implement email retention policies to protect against risk, but employees complain about the impact to productivity.
Material provides the necessary balance: We find and redact sensitive content in emails and bring it back, only when needed, via your pre-existing user-authentication processes (i.e. Okta, Duo, etc).
Customers like Mars, Databricks, and PagerDuty keep sensitive content safe by leveraging Material.
📜 In this newsletter…
AppSec: Modernizing Secrets Scanning, semantic secret scanning tool, tool to extract URLs, paths, secrets from JS
Threat Modeling: CMS Threat Modeling Handbook, Threat Composer
Mobile Security: Visualizing Android code coverage, Semgrep rules for Android security, iOS deep link attacks
Cloud Security: Tool to escalate SSRF in cloud envs, Abusing Overpermissioned AWS Cognito Identity Pools, AWS CloudTrail cheat sheet
Container Security: Kubernetes Security Basics Series
Machine Learning + Security: PentestGPT, NVIDIA’s AI Red Team
Machine Learning: Open source language server for local models, have agents run multiple tools at a time, AI film festival, Midjourney adds “zoom out”, AI-generated websites stealing ad $, GPT-4’s pitch decks outperform humans
Career: Security study plan, security interview questions, awesome AWS security, how James Kettle chooses a research topic, fix the lifestyle you want- then work backwards from there
Misc: Steve Jobs in his own words, Musk/Zuckerberg cage match
AppSec
tech/deepsecrets
A tool for secret scanning that uses lexing and parsing techniques to understand code and detect secrets, by Avito’s Nikolai Khechumov. You could also leverage Semgrep rules to do this with no custom tooling effort.
BishopFox/jsluice
A command-line tool for extracting URLs, paths, secrets, and other interesting data from JavaScript source code, by Bishop Fox’s Tom Hudson.
📣 Cloud Detection and Response Survey Report
We surveyed more than 500 security, engineering, and IT practitioners and leaders to understand as much about their cloud environments and security practices as possible. We compared the results with other industries surveys and benchmarks, as well as actual data taken from thousands of customer data published through large cloud service providers.
What did we find? Significant cognitive disconnect in cloud security perception vs. readiness. More than 80% of organizations are confident their current tools and team would cover their organization from a well orchestrated attack, but 95% expressed concern over their ability to detect a threat actor in their environment. Read the survey to learn more.
Threat Modeling
CMS Threat Modeling Handbook
Overview of the benefits of threat modeling and how it is used to help identify potential weaknesses, by Aquia’s Robert Hurlbut et al. Always interesting to see how big government orgs think about security.
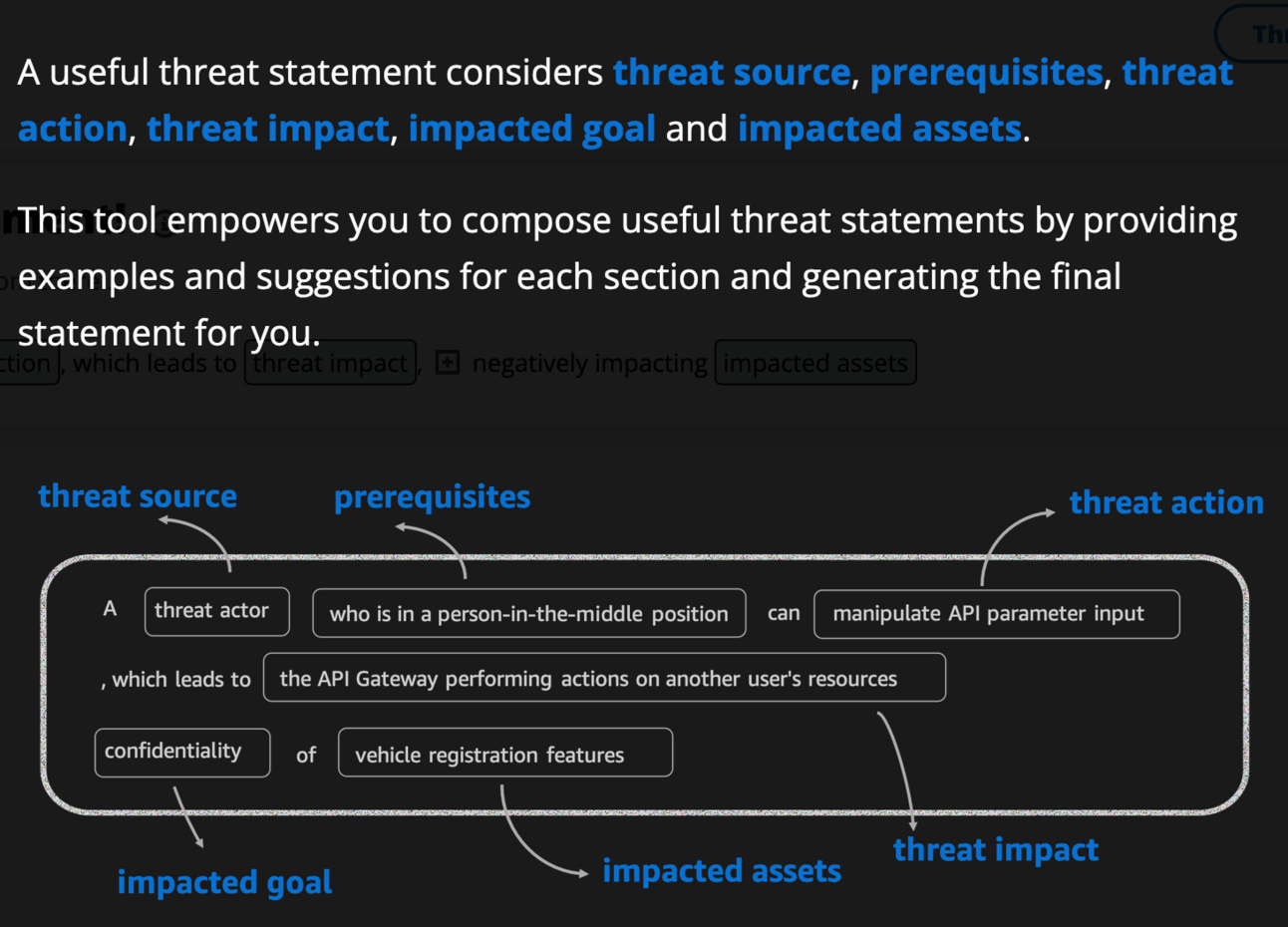
awslabs/threat-composer
A threat modeling tool to help humans to reduce time-to-value when threat modeling. It provides a prescriptive threat articulation structure, dynamic suggestions, complete threat statement examples, and import/export capabilities to enable persistent storage and sharing.
Mobile Security
iOS Deep Link Attacks Part 2 – Exploitation
In part 1, 8ksec discusses the various types of deep link schemas used in iOS apps and how to identify them. In part 2, they delve into exploitation scenarios including phishing attacks, HTML injection, and CSRF vulnerabilities utilizing deep links and inadequate URL validation, as well as mitigation strategies.

Cloud Security
assetnote/surf
By Assetnote’s Shubham Shah: A tool that helps you escalate SSRF vulnerabilities on modern cloud environments by filtering a list of hosts, returning a list of viable SSRF candidates.
Abusing Overpermissioned AWS Cognito Identity Pools
Wes Ladd discusses how identity pools with excessive privileges can allow attackers to authenticate with the AWS Cognito service and carry out restricted actions, including accessing sensitive data, manipulating services, and performing privilege escalation. The article also provides a detailed explanation of the process involved and few commands to exploit this issue.

Machine Learning + Security
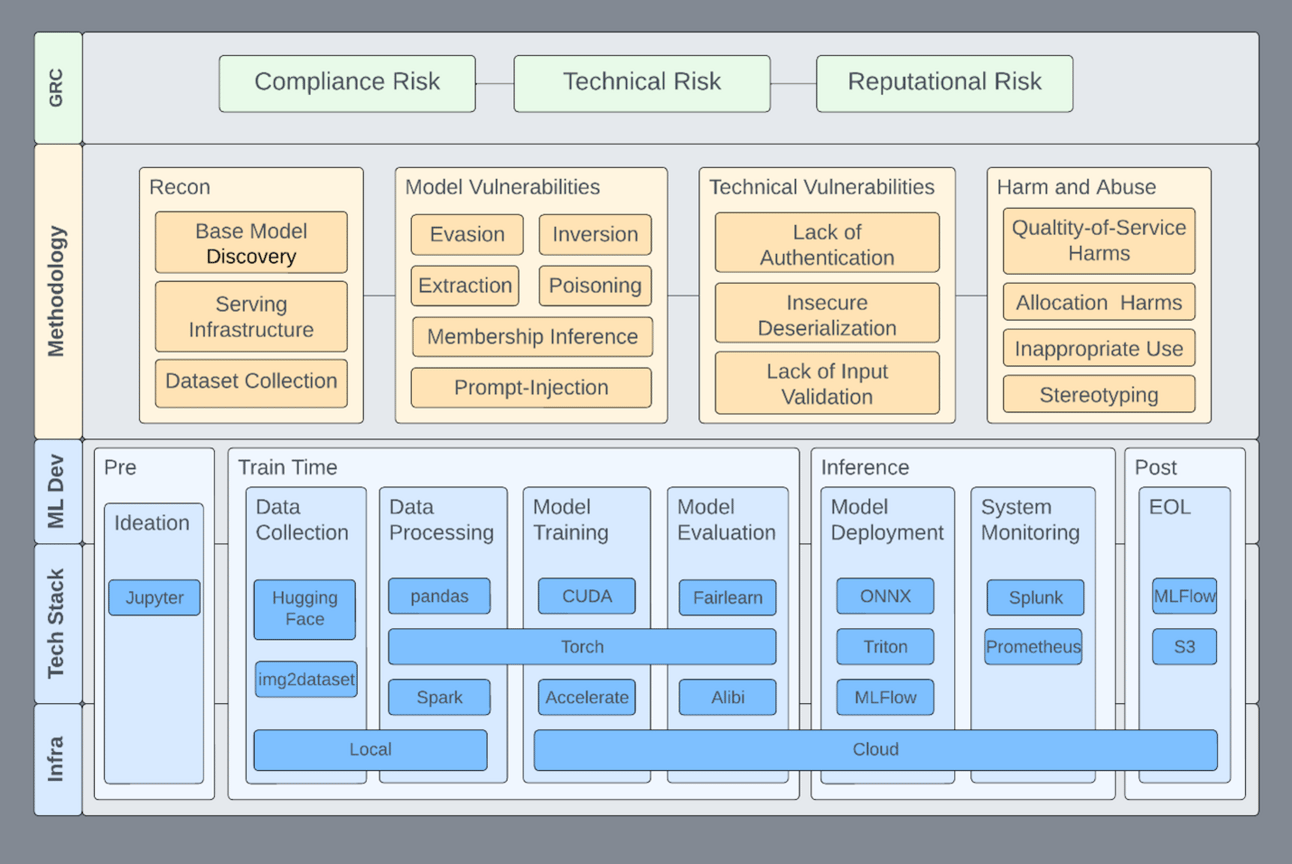
NVIDIA AI Red Team: An Introduction
NVIDIA’s Will Pearce and Joseph Lucas present their AI Red Team framework and methodology, which aims to assess machine learning (ML) systems from a security standpoint. The framework brings together offensive security experts and data scientists to detect and address risks in ML systems, while establishing a basis for ongoing enhancement throughout the ML lifecycle.
Machine Learning
morph-labs/rift
By Morph: an open-source language server and IDE extension that lets everyone deploy a personal AI software engineer — locally hosted, private, open source.
Overall, investors and business owners say GPT-4 generated pitch decks are 2x more convincing than those made by humans.
Overall, investors and business owners were 3x more likely to invest after reading a GPT-4 pitch deck than after reading a human one.
1 in 5 investors and business owners pitched by GPT-4 would invest $10,000 or more.
Career
Considering the required time investment
Exploring topics that push you beyond your comfort zone
Focusing on novel attack techniques
Consider the applicable audience- building on a large body of recent research may make it hard for many to follow
Prioritize personal development
Fix the lifestyle you want. Then work backwards from there.
Starting with a dream lifestyle — as oppose to a dream job — opens up more creativity. When thinking only about jobs, you’ll find yourself considering the same artificially-narrow menu of options troubled over by most talented college grads. A lifestyle, on the other hand, provides much more flexibility — letting you discover potential paths previously hidden from your planning process.
By cutting to the bottom-line — what would make me feel best? — and then working backward from this answer, you are maximizing your odds that you’ll actually get somewhere worth going.
Misc
1972 – Dennis Ritchie invents a powerful gun that shoots both forward and backward simultaneously. Not satisfied with the number of deaths and permanent maimings from that invention he invents C and Unix.
Make Something Wonderful: Steve Jobs in his own words
A curated collection of Steve’s speeches, interviews and correspondence. Steve shares his perspective on his childhood, on launching and being pushed out of Apple, on his time with Pixar and NeXT, and on his ultimate return to the company that started it all.
A Meta spokeswoman said Mr. Zuckerberg’s response “speaks for itself.” Twitter’s media office auto-responded to a request for comment with a poop emoji.
✉️ Wrapping Up
Have questions, comments, or feedback? Just reply directly, I’d love to hear from you.
If you find this newsletter useful and know other people who would too, I’d really appreciate if you’d forward it to them 🙏