A recent investigation has uncovered a flaw in internet-connected doorbell cameras, specifically affecting Ivanti’s Pulse Secure appliances.
The NVISO Incident Response team discovered the discovery, which identified two covert TLS-based backdoors, SparkCockpit and SparkTar, allowing attackers to hijack these devices and gain unauthorized access to internal networks.
The investigation was triggered by a critical-sector organization that observed a compromise of their Ivanti appliance, leading to the discovery of these sophisticated backdoors.
Sophisticated Attack Techniques
Both SparkCockpit and SparkTar employ selective interception of TLS communication towards legitimate Ivanti server applications, which helps them avoid detection.
SparkTar is particularly advanced and capable of surviving factory resets and appliance upgrades.
It also allows for file uploads, command execution, and setting up SOCKS proxies to relay attacker traffic directly into the organization’s network.
The NVISO team found that these backdoors could evade detection by most network-based security solutions, offering attackers persistence and remote access capabilities, including traffic tunneling through SOCKS proxies.
SparkCockpit: A Closer Look
SparkCockpit was deployed through an evolution of the Pulse Secure BUSHWALK web shell and provides basic upload/download capabilities alongside command execution.
It achieves boot persistence by patching the configuration of the RemoteSpark’s server component, SparkGateway, to load a malicious security.jar plugin.
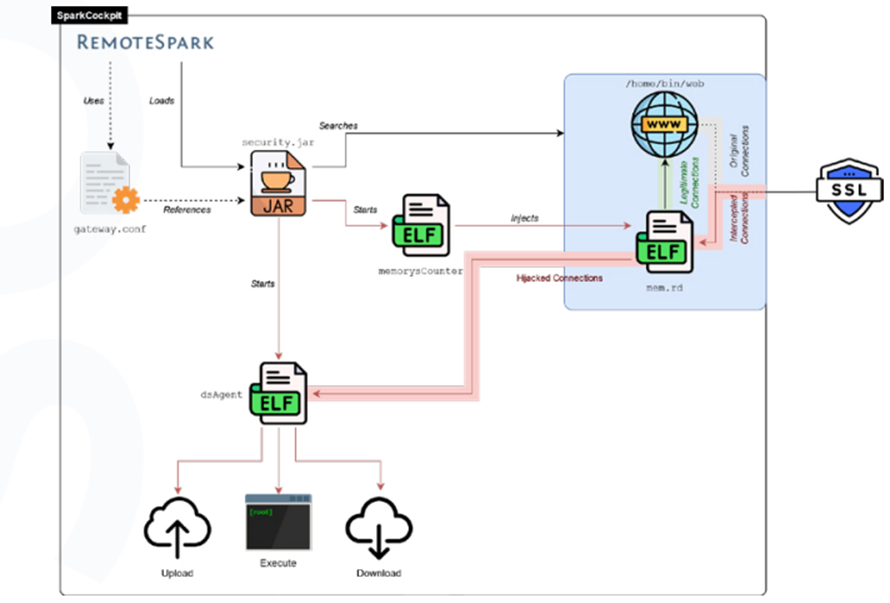
SparkTar: A More Complex Threat
SparkTar, on the other hand, is more complex and provides a more flexible toolset for attackers. It includes input/output streaming for commands and deeper persistence mechanisms.
The backdoor controller libchilkat, which is unrelated to legitimate Chilkat commercial tools, is responsible for launching the backdoor and ensuring its persistence.
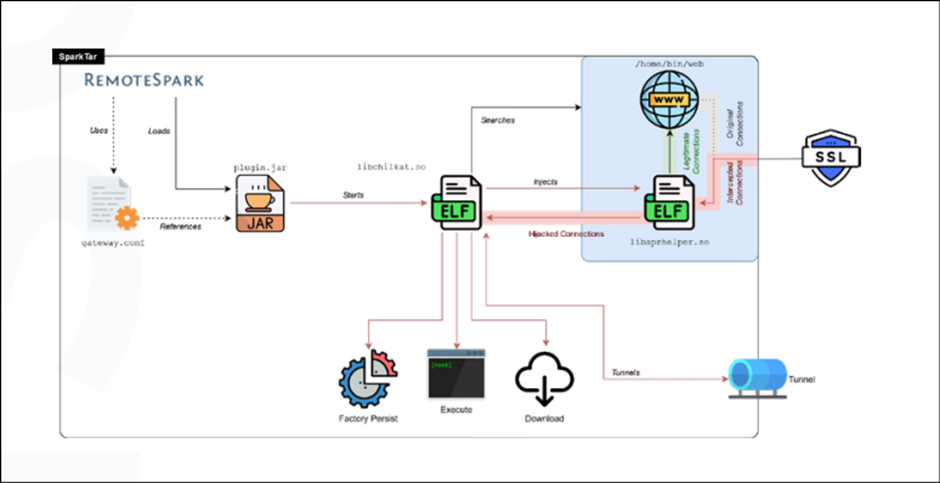
NVISO’s Response and Community Support
NVISO has created detection rules to help organizations determine if these backdoors have impacted them.
The company, a European cybersecurity leader, is committed to sharing knowledge and supporting organizations in protecting against advanced and evolving cyber threats.
NVISO’s findings have been corroborated by research from Mandiant and partially observed by Fortinet.
A recent tweet from NVISO Labs released an Incident response about covert TLS n-day backdoors: SparkCockpit & SparkTar
Implications for Security
The presence of these backdoors in Ivanti’s Pulse Secure appliances highlights the need for increased vigilance and improved security measures for internet-connected devices.
Organizations using Ivanti devices are advised to review NVISO’s report and apply the provided detection rules to safeguard against potential compromises.
In conclusion, the discovery of SparkCockpit and SparkTar backdoors serves as a critical reminder of the persistent and sophisticated nature of cyber threats. Organizations must continuously enhance their security posture and resilience to protect against such advanced tactics.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
