Advanced Persistent Threat (APT) group known as ToddyCat, new insights have emerged regarding their sophisticated methods of hijacking network infrastructure to steal sensitive data from governmental organizations across the Asia-Pacific region.
This group, previously reported on for using data collection and exfiltration tools, has now been observed employing advanced traffic tunneling and data extraction techniques to maintain persistent access to compromised systems.
ToddyCat’s operations focus on governmental entities, some involved in defense.
The group’s primary objective is the extraction of large volumes of sensitive information, a task that requires automated processes to handle the scale of data theft.
According to Securelist, ToddyCat has successfully and extensively automated data harvesting, ensuring continuous access to the systems it targets.
Free Webinar | Mastering WAAP/WAF ROI Analysis | Book Your Spot
One critical strategy employed by ToddyCat involves creating secure tunnels to route traffic from the compromised network to its controlled servers.
This technique helps exfiltrate the data stealthily and allows the attackers to maintain a persistent presence within the network.
Tools like PsExec and Impacket have been noted, facilitating the transfer and execution of malicious payloads.
SoftEther VPN
A notable tool in ToddyCat’s arsenal is the SoftEther VPN server utility, which establishes robust VPN tunnels.
This utility supports various protocols and provides strong encryption, making it an ideal choice for secure communication between the compromised host and the attacker’s server.
To launch the VPN server, the attackers used the following files:
- vpnserver_x64.exe: a digitally signed VPN server executable
- hamcore.se2: a container file that includes components required to run vpnserver_x64.exe
- vpn_server.config: server configuration
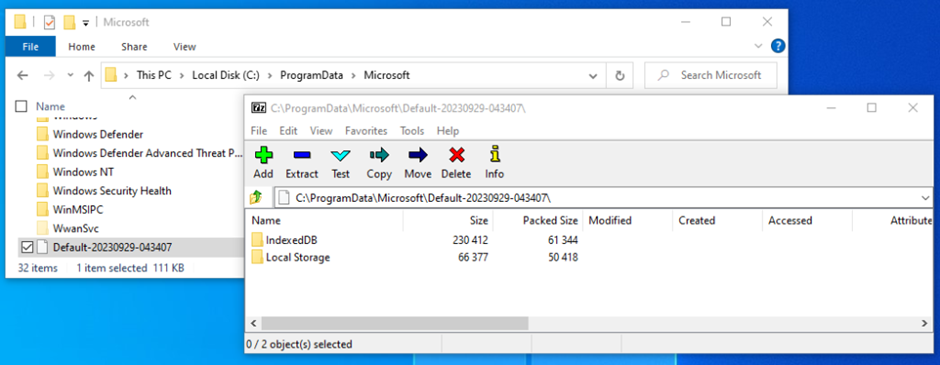
Recently, ToddyCat integrated a new tool named ‘cuthead’ into its operations.
This tool, a .NET compiled executable, is specifically designed to search and extract documents from the compromised systems.
The name ‘cuthead’ originates from the file description field of the sample analyzed, highlighting the tool’s primary function in the group’s cyber espionage activities.
The continuous evolution of ToddyCat’s toolkit poses significant challenges for cybersecurity defenses, particularly within the targeted governmental sectors.
The group’s ability to adapt and integrate new tools for data extraction and traffic tunneling indicates a high level of sophistication and resourcefulness.
The persistent activities of the ToddyCat APT group underscore the critical need for robust cybersecurity measures and constant vigilance in the digital domain.
As they continue to refine their techniques and expand their toolkit, the threat posed by this group remains significant.
It is crucial for organizations, especially those in sensitive governmental sectors, to implement comprehensive security strategies to protect against such advanced threats.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP