Advanced persistent threat actors continue to develop sophisticated techniques for compromising corporate communications, with the ToddyCat APT group demonstrating remarkable evolution in their operational capabilities.
Recent research from Kaspersky reveals how this highly organized espionage group has refined methods for covertly accessing internal employee communications at target organizations throughout the second half of 2024 and early 2025.
Email remains the cornerstone of business correspondence for companies worldwide, delivered through either in-house infrastructure such as Microsoft Exchange Server or cloud-based services like Microsoft 365 and Gmail.
While organizations often assume cloud services provide superior confidentiality protection keeping email data outside company infrastructure even when internal systems are compromised the ToddyCat group has proven this assumption dangerously false.
Their latest attack vectors demonstrate that even cloud-hosted communications remain vulnerable to determined threat actors who establish a foothold within target networks.
ToddyCat has significantly upgraded their TomBerBil toolkit, previously written in C# and C++, with a new PowerShell variant discovered in incidents during May and June 2024.
This modified version executes on domain controllers with privileged access, remotely targeting browser files across the network via SMB protocol.
The tool systematically harvests cookies, saved passwords, and browsing history from Chrome, Edge, and newly supported Firefox browsers on user workstations.
The PowerShell TomBerBil reads host names from a configuration file, establishes SMB connections to network shares, and extracts critical browser files including Login Data databases containing encrypted credentials, Local State files with decryption keys, and Cookies databases.
Critically, the tool also copies DPAPI encryption keys stored in user profiles, enabling attackers to decrypt all stolen browser data offline using victims’ SIDs and passwords.
This network-based approach significantly hampers detection compared to previous versions that ran directly on compromised hosts.
Outlook Email Storage
When browser-focused techniques attracted security monitoring attention, ToddyCat pivoted to directly targeting corporate email stored in Outlook OST files.
These Offline Storage Table files cache complete copies of mailboxes for offline access, but remain locked while Outlook runs. To overcome this protection, attackers deployed TCSectorCopy, a specialized 32-bit tool written in C++ that performs sector-by-sector disk reading at the hardware level.
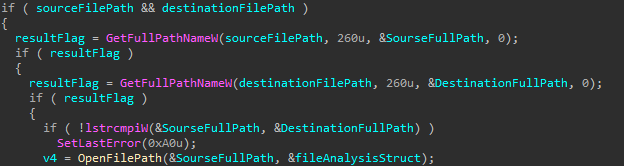
TCSectorCopy bypasses standard Windows file access APIs by opening disk devices directly in read mode and sequentially copying file contents, effectively circumventing application-level locks.
After extracting OST files, attackers process them using XstReader, an open-source C# utility that exports email messages and attachments into HTML, RTF, or text formats for analysis. This combination allows complete mailbox exfiltration while applications continue running normally.

ToddyCat’s most sophisticated evolution targets Microsoft 365 environments by stealing OAuth 2.0 access tokens from application memory.
Using SharpTokenFinder written in C#, attackers locate processes for Teams, Outlook, Word, Excel, and other Microsoft 365 applications, then create memory dumps containing JWT tokens.
These tokens encode base64 authorization credentials that authenticate API requests to Microsoft cloud services.
When endpoint protection blocked SharpTokenFinder attempts, operators switched to the legitimate Sysinternals ProcDump utility to create complete process dumps of Outlook and other Office applications.
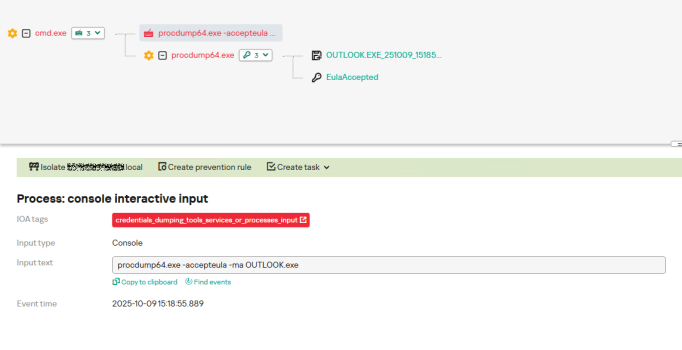
The extracted access tokens, though temporary, provide sufficient time to retrieve entire mailboxes from Microsoft 365 cloud infrastructure without triggering on-premise monitoring systems.
Detection Requires Comprehensive Monitoring
The extracted access tokens, though temporary, provide sufficient time to retrieve entire mailboxes from Microsoft 365 cloud infrastructure without triggering on-premise monitoring systems.
Organizations should implement auditing for browser folder access via network protocols, monitoring Windows Event ID 5145 for SMB connections to sensitive Chrome, Firefox, and Edge data directories.
DPAPI encryption key folder access should trigger alerts, while Sysmon Event ID 9 detections can identify raw disk access attempts targeting OST files.
Command-line monitoring for ProcDump execution against Office 365 process names provides critical visibility into token theft attempts.
Kaspersky recommends deploying both endpoint protection and advanced threat monitoring platforms with current threat intelligence to counter ToddyCat’s evolving techniques effectively.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
