ToddyCat, a sophisticated cyber-espionage threat group also known as Websiic and Storm-0247, has emerged as a significant risk to organizations across Europe and Asia.
The group’s operations, which began in December 2020 by targeting Microsoft Exchange servers in Taiwan and Vietnam, have since evolved into complex, multi-stage campaigns that leverage advanced evasion techniques and specialized malware tools.
These early attacks culminated in the installation of Samurai, a passive backdoor that maintained persistent access to compromised systems.
The threat landscape shifted dramatically in February 2021 when ToddyCat pivoted to exploiting the widely-known ProxyLogon vulnerability a critical vulnerability in Microsoft Exchange Server that allows unauthenticated remote code execution.
This vulnerability, CVE-2021-31207, became the primary vector for a rapid escalation of attacks against high-profile organizations throughout Europe and Asia.
Despite changing their initial infection vector, ToddyCat maintained consistency in their subsequent attack chains, suggesting a standardized methodology for post-exploitation activities.
The initial December 2020 campaign demonstrated ToddyCat’s technical sophistication. The group exploited an unidentified vulnerability to deploy the China Chopper web shell on Exchange servers, creating a foothold that enabled subsequent infection chains.
Introduction to ToddyCat Malware
By September 2021, ToddyCat’s operational scope had expanded beyond server infrastructure to include desktop systems in Central Asia. Tools also attempt to copy files associated with Microsoft Credentials and DPAPI master keys.
During this phase, the group distributed loaders for the Ninja Trojan via Telegram, leveraging social engineering and alternative communication channels to bypass traditional network defenses. This diversification reflected an adaptive threat actor with expanding operational capabilities.
Recent activity documented in 2024 reveals the group’s continued evolution. In early 2024, security researchers detected a suspicious file named version.dll in temporary directories on compromised machines.
This artifact was identified as TCESB, a sophisticated tool designed to exploit vulnerabilities in the ESET command-line scanner.
Between May and June 2024, a new PowerShell variant of the TomBerBil tool was discovered executing on domain controllers, explicitly targeting the harvesting of credentials and cookies from Chrome, Edge, and Firefox browsers via SMB shares.
ToddyCat’s operational methodology demonstrates exceptional technical maturity. The group employs PowerShell and Windows Command Shell extensively to execute malicious scripts, automating data theft and system reconnaissance.
Persistence is maintained through scheduled tasks and reverse SSH tunnels, enabling long-term access to compromised environments.
Their defense evasion strategies are particularly noteworthy, incorporating the “Bring Your Own Vulnerable Driver” (BYOVD) technique through the installation of vulnerable drivers like DBUtilDrv2.sys, as well as DLL side-loading attacks that execute malicious code within the context of trusted processes.
Mitigations
Data exfiltration represents a critical component of ToddyCat’s workflow. The group utilizes specialized tools such as TCSectorCopy to bypass file locks on Outlook Offline Storage Table (OST) files a sophisticated technique that opens disk devices at the driver level to circumvent standard Windows API restrictions.
Stolen data is compressed using WinRAR or 7-Zip utilities before transmission through established command-and-control channels.
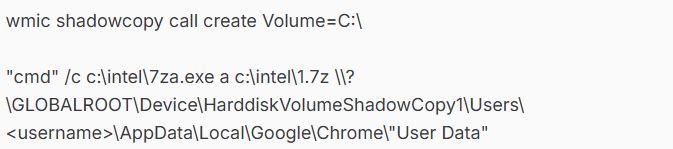
The group’s credential theft strategies encompass OAuth token extraction from process memory, browser credential harvesting, and Windows Credential Manager exploitation.
Lateral movement across compromised networks is facilitated through SMB protocol access to administrative shares, enabling the group to transfer tools such as SSH clients and extract credentials from user directories across multiple systems.
This systematic approach allows ToddyCat to establish a persistent presence and exfiltrate data from multiple organizational targets within a single incident.
Organizations targeted by ToddyCat should implement comprehensive detection controls focusing on anomalous PowerShell execution, scheduled task creation patterns, and reverse SSH tunnel establishment.
Enhanced monitoring of SMB share access, Outlook file operations, and browser credential repositories remains essential for early threat detection.
The group’s demonstrated sophistication necessitates robust incident response procedures and network segmentation to contain potential breaches.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
