How do you lead a security team when threats evolve faster than your tools? It’s a challenge many CISOs face daily.
Detection gaps, constant alert noise, and slow incident response make it harder to protect the organization and support the team.
The real issue often comes down to visibility. Without seeing how a threat actually behaves, it’s difficult to prioritize, act quickly, or respond with confidence.
An interactive sandbox changes that. It gives analysts the context they need, watching malware run in real time, interacting with it, and collecting meaningful insights.
Here are three common problems security leaders deal with and how a sandbox helps solve them.
1. Low Detection Rate
Threats don’t stand still. Attackers constantly experiment with new techniques, obfuscation methods, and delivery vectors, making it harder for static or automated tools to keep up.
That’s why relying only on signatures or basic sandboxing often leads to blind spots. To catch modern threats, you need to see how they behave in action.
A fully interactive environment lets analysts step into the malware’s path; opening files, following redirects, and triggering actions just like a real user would.
That level of engagement reveals behavior that static tools simply miss.
With ANY.RUN, your team can safely detonate and interact with suspicious files across Windows, Linux, and Android environments, giving them a much clearer picture of what’s really going on.
Example: Interactive Analysis of a Phishing Attack
Let’s take a look at a real phishing case uncovered using ANY.RUN:
View analysis session

In this analysis session, we start with an email that looks fairly routine; a closing package sent via Outlook, containing an HTML attachment.
Open the file, and it launches a webpage with a CAPTCHA prompt.
.webp)
Once verified, the victim is silently redirected to a fake Microsoft login page designed to steal credentials.
.webp)
As ANY.RUN runs in a fully interactive environment, we can follow the entire chain, from the initial email to the credential harvesting site, in real time.
The sandbox flags the behavior as malicious, highlights the phishing indicators, and provides full visibility into processes, connections, and URLs involved.
It’s the kind of attack that could easily slip past static tools. But here, it’s exposed in a matter of seconds.
Boost detection, reduce alert fatigue, and accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
2. Alert Fatigue
Security teams are overwhelmed not because they lack alerts, but because they get too many.
Sifting through endless notifications to find the real threats slows everyone down and increases the chance of missing something critical.
ANY.RUN helps reduce alert fatigue by showing results as they happen.
Analysts don’t have to wait for the session to end; the sandbox highlights malicious activity in real time, flags important behaviors, and gives visual cues that make analysis faster and easier, even for junior team members.
On top of that, Automated Interactivity provided by ANY.RUN takes it further. It simulates user behavior inside the sandbox, automatically clicking through prompts and launching files, which means faster verdicts and less manual work.
Example: Automated Detection of Remcos via ANY.RUN Sandbox
Let’s take a look at how ANY.RUN helps cut through alert fatigue by surfacing results in real time, without any manual steps:
View analysis session
.webp)
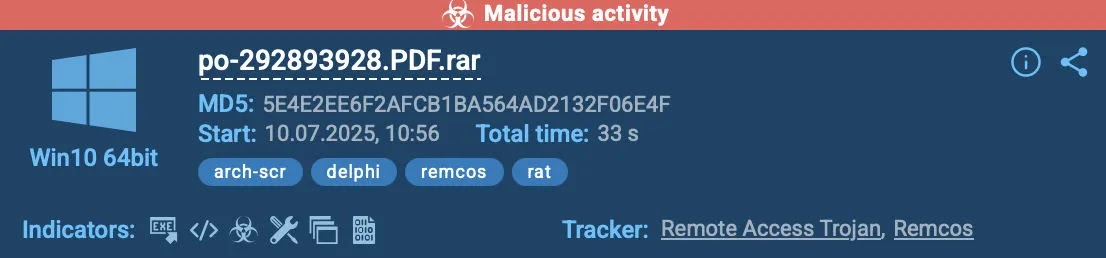
In this case, we’re dealing with a suspicious RAR archive named po-292893928.PDF.rar. Inside is a JavaScript file that launches once the archive is extracted.
ANY.RUN’s Automated Interactivity takes over, simulating user behavior and triggering the execution path automatically.
.webp)
As the file runs, the sandbox detects Remcos RAT activity almost instantly. It extracts the configuration file and reveals the command-and-control (C2) IPs, all within just 30 seconds of starting the session.
.webp)
Thanks to the real-time analysis and automated interaction, the session highlights every malicious step clearly, reducing time to verdict and helping cybersecurity professionals avoid drowning in noise.
It’s a practical way to reduce alert fatigue and give even junior analysts the clarity they need to act with confidence.
3. Slow Response
When your team doesn’t have the full picture, even small incidents can turn into bigger problems.
Delays in understanding what a threat is doing, where it’s connecting, or how it entered the system slow down containment and leave room for damage.
Rushing a response without knowing what you’re dealing with can lead to incomplete remediation, missed persistence mechanisms, or even reinfection.
ANY.RUN helps security teams reduce investigation time and respond with greater confidence by transforming raw behavior into clear, actionable insight.
Example: Complete Breakdown of a Formbook Infection
Let’s see how ANY.RUN helps security teams go from initial alert to full understanding in just a few clicks.
View analysis session
.webp)
In this session, a suspicious executable is launched.
The sandbox shows the entire execution tree; a clear, visual process graph that helps analysts trace how the malware moves through the system, spawns processes, and maintains persistence.
.webp)
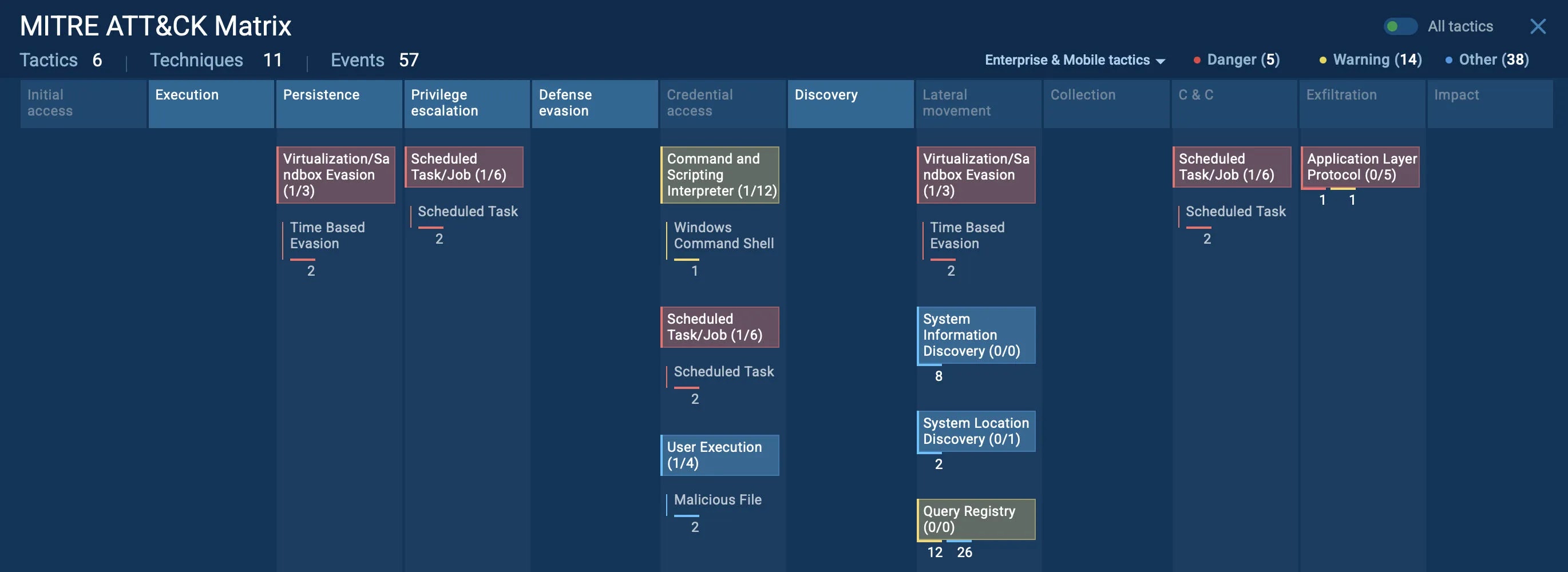
Next, the attack is mapped to the MITRE ATT&CK framework, showing the exact TTPs used, including scheduled tasks for persistence, credential access, and evasion techniques.
This helps teams understand not just what happened, but how the attacker operated.
.webp)
Finally, all IOCs, including domains, IPs, file hashes, and URLs, are automatically extracted and presented in one place. No need to switch tabs, search logs, or dig for data; it’s all ready to export and share.
.webp)
In a short amount of time, your team gets everything needed for deeper analysis, reporting, and a confident response, without wasting time jumping between tools.
Why An Interactive Sandbox Should Be Part Of Every CISO’s Strategy
Modern threats demand more than passive detection and guesswork. To stay ahead, security teams need tools that offer clarity, context, and speed, without adding more noise.
That’s exactly what an interactive sandbox brings to the table.
With ANY.RUN, you’re enabling your team to act on it with precision.
Here’s how ANY.RUN helps CISOs overcome their top challenges:
- Improve detection by revealing behavior missed by static or automated tools
- Cut through noise with real-time analysis and visual threat indicators
- Accelerate response with full process graphs, TTPs, and IOC extraction
- Empower junior analysts with intuitive workflows and automated interactivity
- Reduce risk by enabling faster, more accurate decision-making across the SOC
Whether you’re building detection rules, updating playbooks, or investigating critical incidents, the sandbox gives you the visibility you need to lead with confidence.
Try ANY.RUN for 14 days and see how it transforms your team’s detection and response.
