Remote monitoring and management (RMM) tools are a go-to for IT teams, but that same power makes them a favorite trick up attackers’ sleeves, too.
In the first half of 2025, ANY.RUN analysts reviewed thousands of real-world malware detonations in the interactive sandbox and spotted a clear trend: five tools were involved in most RMM-related intrusions.
Let’s take a closer look at the five RMM tools most commonly exploited by attackers, and how your team can spot this activity faster, before it turns into something more serious.
If you work in a SOC or handle incident response, this is the kind of pattern worth paying attention to.
Snapshot of the Data
.webp)
This breakdown reflects the frequency of each RMM tool observed across suspicious and malicious sandbox sessions in the first half of 2025.
The numbers are drawn from ANY.RUN’s internal tagging system, which tracks tool usage patterns in real time.
It’s a quick way to see which platforms stood out in attacker activity and how often they appeared in actual malware investigations.
1. ScreenConnect: 3,829 Sandbox Sessions
ScreenConnect (now branded as ConnectWise Control) is a legitimate remote support and desktop access tool used by IT teams and MSPs.
Unfortunately, its powerful remote control features also make it an easy choice for threat actors looking to silently access and manage compromised machines.
In the following sandbox session, we can clearly see how ScreenConnect is used in a phishing campaign that mimics a Zoom meeting link:
View sandbox session

The fastest way to catch threats like this is through interactive sandboxes like ANY.RUN.
In the top-right panel of the session, the platform immediately flags the activity as Malicious, assigning clear behavioral tags such as “screenconnect”, “rmm-tool”, and “remote”.

The process tree highlights the malicious executable (ScreenConnect.WindowsClient.exe) and provides rich context like the command line, YARA detections, and more, saving your time and guesswork.
Cut investigation time, reduce alert fatigue, and catch hidden threats faster with ANY.RUN’s interactive sandbox -> Try ANY.RUN now
Rather than digging through logs or relying on static detection, this real-time visibility helps teams spot abuse early, even when attackers use legitimate tools.

2. UltraVNC: 2,117 Sandbox Sessions
UltraVNC is an open-source remote desktop tool often used by IT support teams to view and control another computer over a network. It’s lightweight, free, and easy to configure.
In the sandbox session below, UltraVNC is used as part of an Agent Tesla campaign.
View sandbox session
.webp)
ANY.RUN’s interactive sandbox flags the behavior right away, labeling the session as Malicious and tagging it with “ultravnc”, “rmm-tool”, and “stealer”.
The process tree reveals how RegAsm.exe launches with suspicious behavior and is tied to Agent Tesla activity, including credential theft.
With real-time detection, detailed indicators, and visualized execution flow, ANY.RUN helps analysts quickly connect the dots, without having to reverse engineer every step manually.
3. NetSupport: 746 Sandbox Sessions
NetSupport Manager is a legitimate remote access tool often used in corporate and educational settings. But when deployed from unusual locations and without user consent, it’s a red flag.
Attackers commonly use it as a stealthy Remote Access Trojan (RAT) thanks to its built-in capabilities for screen viewing, file transfer, and command execution.
In the sandbox session below, the attack begins with a text file containing obfuscated PowerShell code, which triggers the execution of client32.exe; a NetSupport binary dropped into the user’s roaming profile:
View sandbox session

The process tree shows client32.exe running from:
C:UsersadminAppDataRoamingbDabSkclient32.exe. This is a typical location used by malware to avoid detection. 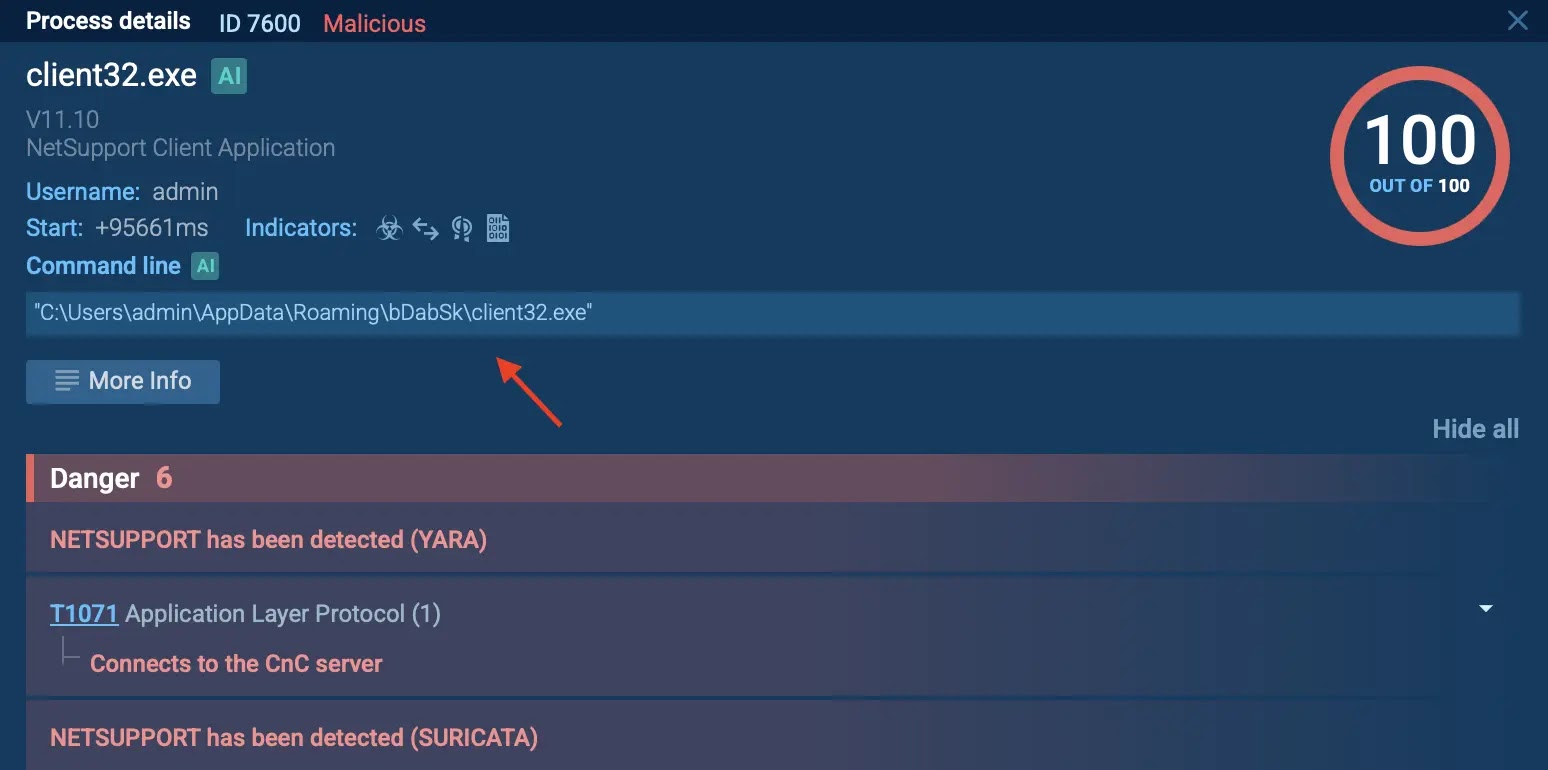
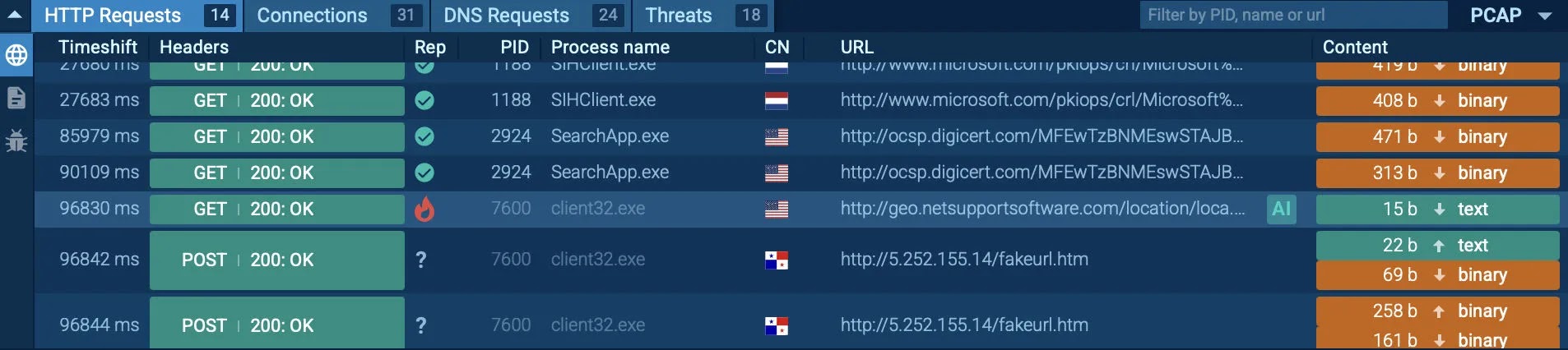
Below, in the HTTP request section, we can see a connection to the suspicious domain geo.netsupportsoftware.com, confirming the use of NetSupport for command-and-control.
Combined with POST traffic to a fake C2 server, this behavior helps analysts connect the dots quickly and confidently.
.webp)
4. PDQ Connect: 230 Sandbox Sessions
PDQ Connect is a cloud-based system management tool that allows IT teams to deploy software, run scripts, and manage endpoints remotely, without needing domain access.
It is a target for abuse in phishing and initial access campaigns.
In the sandbox session below, the attack starts with a fake government verification page; a phishing site attempting to lure the victim into downloading a malicious payload:
View sandbox session
.webp)
Shortly after the phishing page loads, we see a suspicious connection from pdq-connect-agent.exe to a remote IP address (162.159.141.50) over port 443, as shown in the network stream.
The executable appears alongside a companion updater process, pdq-connect-updater.exe, hinting at a stealthy installation and command channel.
.webp)
This kind of setup can easily fly under the radar in static or rule-based systems.
But ANY.RUN’s interactive sandbox reveals it in seconds, highlighting the exact process that makes the outbound request and giving analysts the full picture of what’s happening, from the fake CAPTCHA to the live network activity.
5. Atera: 171 Sandbox Sessions
Atera is a remote monitoring and management (RMM) platform designed for IT professionals to remotely manage systems, automate maintenance, and monitor performance.
Like other legitimate tools, it can be quietly installed and misused by attackers for persistence and control, often without triggering alarms.
In the sandbox session below, the file AteraAgent.exe runs from its default directory but triggers multiple warnings related to system service execution, file overwrites, and suspicious process behavior:
View sandbox session
ANY.RUN’s detection engine assigns a Malicious verdict.
The process drops or overwrites executable content and starts SC.EXE to register itself as a Windows service; common behavior in stealthy persistence setups.
.webp)
Below in the Threat Details tab, we also see an outbound connection to agent-api.atera.com, flagged as a Potential Corporate Privacy Violation.
This detection (via Suricata IDS) confirms that the Atera agent is actively communicating with remote infrastructure, whether the user knows it or not.
.webp)
With this level of visibility, teams can quickly spot when a trusted utility crosses the line into unauthorized use and take action before deeper compromise occurs.
Detect Abuse Early And Respond With Confidence
RMM tools aren’t going away but with the right visibility your team doesn’t have to be caught off guard when they’re used against you.
ANY.RUN helps security teams catch misuse faster, investigate smarter, and make better decisions with context-rich, real-time analysis.
From instant verdicts and detailed behavioral tags to network forensics and attack mapping, ANY.RUN gives analysts the solutions they need to stay ahead, without digging through logs or relying solely on static detections.
Whether you’re working in a SOC, running threat hunts, or investigating incidents, it is built for speed, clarity, collaboration, and trust.
Start your 14-day trial of ANY.RUN today and see how much faster your team can catch threats hiding in plain sight.
