Eaton Zveare, a hobbyist white hat hacker located in Sarasota, Florida, gained access to the C360 customer relationship management online program. This tool is used by the Japanese automobile manufacturer to handle the information of its Mexican clients. In October, he gained access to the system and informed the automobile manufacturer. The security breach at Toyota was patched up. This past week, Zveare disclosed it to the public. Zveare gained access to the names, addresses, phone numbers, email addresses, and tax IDs of customers of Toyota in Mexico. He also gained access to the customers’ car, service, and ownership histories for an unknown number of those consumers. He got through the automaker’s corporate login screen and altered the development environment for the program. Before the program is made available to the public, its functionality is tested at this location.
The application programming interface, which is a section of code that is linked to a web server, is where the security flaw was discovered. Using the application programming interface (API), web-based apps and Internet-connected items that run on a variety of software are able to interact with one another and exchange data in order to run more effectively. When one server’s API connects with the API of another server, the endpoint of the first server’s API will specify where data may be accessible by the second server’s API. A server’s or service’s URL may be included in an endpoint if it is available.
The C360 application from Toyota compiles information on customers from many parts of the firm. An employee may see a customer’s name, address, contact information, gender, and interactions with the firm all within a single view of the customer’s profile. This information comprises a record of previous purchases, payment information, complaints about service, a social presence, and channel preferences.
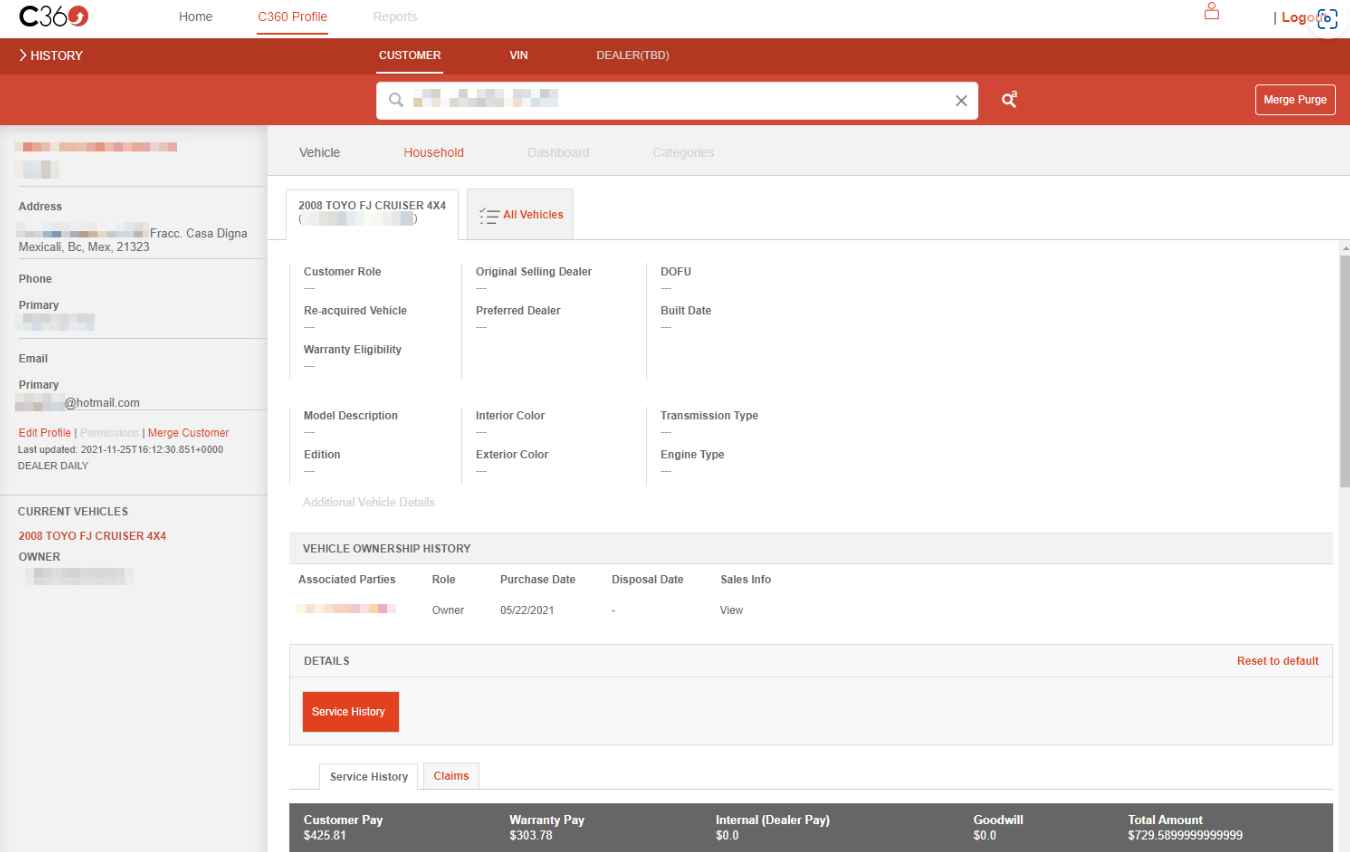
Since the application’s settings did not need to be validated as well, Toyota’s customer information was exposed. Toyota resolved the problem by removing some of the websites from service and modifying the application programming interfaces (APIs) such that they now demand an authentication token.
According to the researcher “Since the production app was password protected, Toyota most likely anticipated that no one would be able to access the production API endpoint. Instead, it seems that their engineers included it in the development app. The application’s loading experience is improved with the help of ngx-ui-loader, which is why the API endpoints were included in the code. Nevertheless, the API routes were left out so that any potential issues could be avoided. Improving the speed at which an application loads content is not in and of itself a bad thing; but, in this situation, the developers exposed all of their private API endpoints in every environment by mistake.
If they hadn’t been included in the code for the development app, it’s likely that it would have been hard to locate the production and qa API endpoints that make use of Amazon API Gateway.”
The automobile manufacturer said that there was no proof of unauthorized access to Toyota systems and that it valued the study carried out by Zveare. It extended an invitation to other hackers to collaborate with it by directing them to its security vulnerability disclosure program hosted on HackerOne.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
