In July 2025, cybersecurity firm CYFIRMA uncovered an active phishing campaign targeting Linux-based operating systems used by Indian government and military organisations.
This operation, attributed to TransparentTribe (also known as APT36 or Operation C-Major), is the latest in a series of ongoing cyber espionage campaigns supporting Pakistan’s strategic interests.
TransparentTribe, a Pakistani-nexus threat group active since at least 2013, has evolved its tactics to exploit current events and local unrest within India, aiming to compromise sensitive government entities.
The initial wave of attacks, detected in June 2025, involved sophisticated delivery and infection mechanisms purpose-built for Linux environments—especially the Bharat Operating System Solutions (BOSS) distribution mandated across many Indian government agencies.
While prior TransparentTribe campaigns exploited third-party cloud services like Google Drive for payload delivery, recent attacks have transitioned to dedicated staging servers, increasing stealth and control.
The campaign’s infection chain starts with phishing emails containing a malicious ZIP archive—either directly attached or linked via an external URL.

These ZIP files conceal a cleverly crafted DESKTOP file, masquerading as official government documentation.
Upon execution, the DESKTOP file triggers a multi-stage Bash one-liner that downloads a base64-encoded payload from a remote server, decodes it, writes it to the /tmp/ directory, and executes it—all while opening a legitimate-looking PDF decoy in Firefox to distract the user.


The malicious Bash commands are strategically hidden between blocks of commented embedded PNG data, making detection challenging.
Our investigation revealed that TransparentTribe’s ZIP archive, dubbed MoM_regarding_Defence_Sectors_by_Secy_Defence_25_Sep_2025.zip, contained all necessary elements for this attack, including deceptive icon and application metadata to enhance stealth.
While the execution chain appears robust, it relies on Linux built-ins like curl, eval, and xxd. Ironically, xxd is not installed by default on BOSS Linux, potentially disrupting the payload execution—a design flaw in an otherwise meticulous attack chain.
Technical Analysis and C2 Infrastructure
The campaign ultimately delivers DeskRAT, a remote access trojan (RAT) written in Golang. DeskRAT demonstrates several notable features.
Its function names are uniformly descriptive—mainly evasion techniques for Linux environments, indicating likely assistance from large language models (LLMs) during development.
The sample analyzed is not obfuscated; its core routine simulates legitimate system and memory operations, yet most functions serve as “fodder,” with their outputs unused.
Persistence is achieved through Linux-specific methods: systemd service creation, crontab scheduling, autostart desktop files, and bash startup scripts.
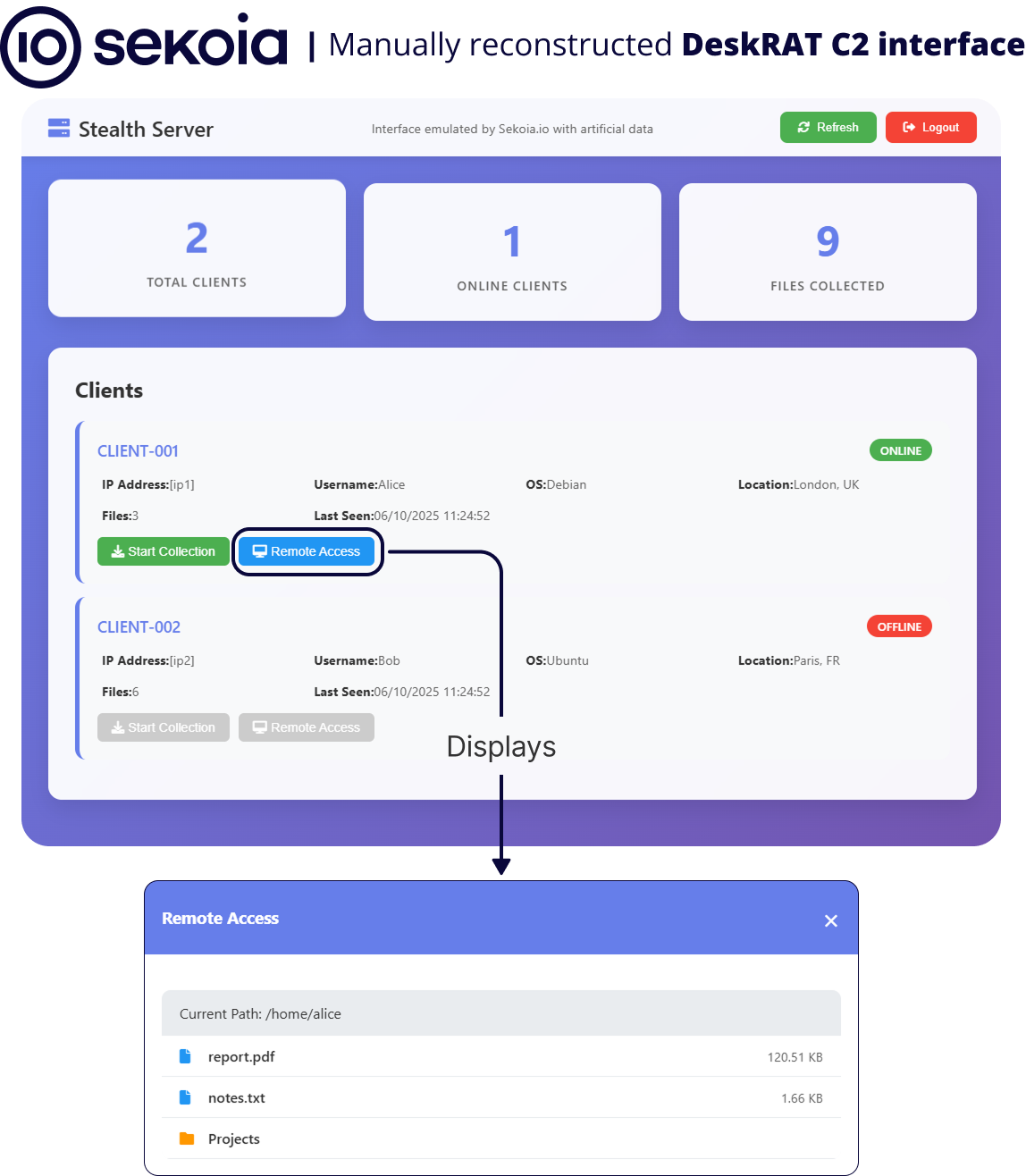

/dashboard with artificial data.Once installed, DeskRAT establishes communication with one of several command-and-control (C2) servers via unsecured WebSocket.
The initial JSON message sent includes fake and irrelevant metadata—hardcoded Office and Chrome version numbers, random CPU statistics—possibly aimed at obscuring the RAT’s true platform.
DeskRAT enables C2 operators to browse files, collect sensitive data, drop and execute secondary payloads, and remotely control infected systems.
Its dashboard offers advanced client management, real-time file operations, and interactive post-exploitation access. The underlying WebSocket protocol is simple, with a minimal JSON schema for command exchange.
Decoy Documents and Geopolitical Context
To entice targets, the campaign leverages real-world events. Decoy documents, like CDS_Directive_Armed_Forces.pdf, urge immediate operational responses from Indian defense officers.
These documents are closely tied to significant incidents—such as violent protests in the Ladakh region in September 2025 and opposition marches in New Delhi in August 2025.
By timing phishing lures to coincide with public unrest, TransparentTribe capitalizes on heightened anxiety and reduced vigilance among targeted government staff.
The Ladakh region, bordering China and Pakistan, remains geopolitically sensitive, with ongoing demands for autonomy and regular protests. The exploitation of these social tensions is a hallmark of TransparentTribe’s opportunistic targeting.
TransparentTribe’s campaign highlights significant advancements in delivery and evasion techniques, including custom tooling, dedicated infrastructure, and context-aware lures.
The use of LLMs in malware development enables rapid iteration, challenging defenders to adapt equally quickly. DeskRAT’s focus on Linux systems—particularly the BOSS distribution—signals a strategic shift in targeting Indian governmental environments.
Ongoing monitoring has revealed evolving versions of both the DeskRAT payload and the associated C2 domains, suggesting that TransparentTribe will continue to refine their methods. Security teams must remain vigilant and enhance detection capabilities to counter these adaptive threats.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
