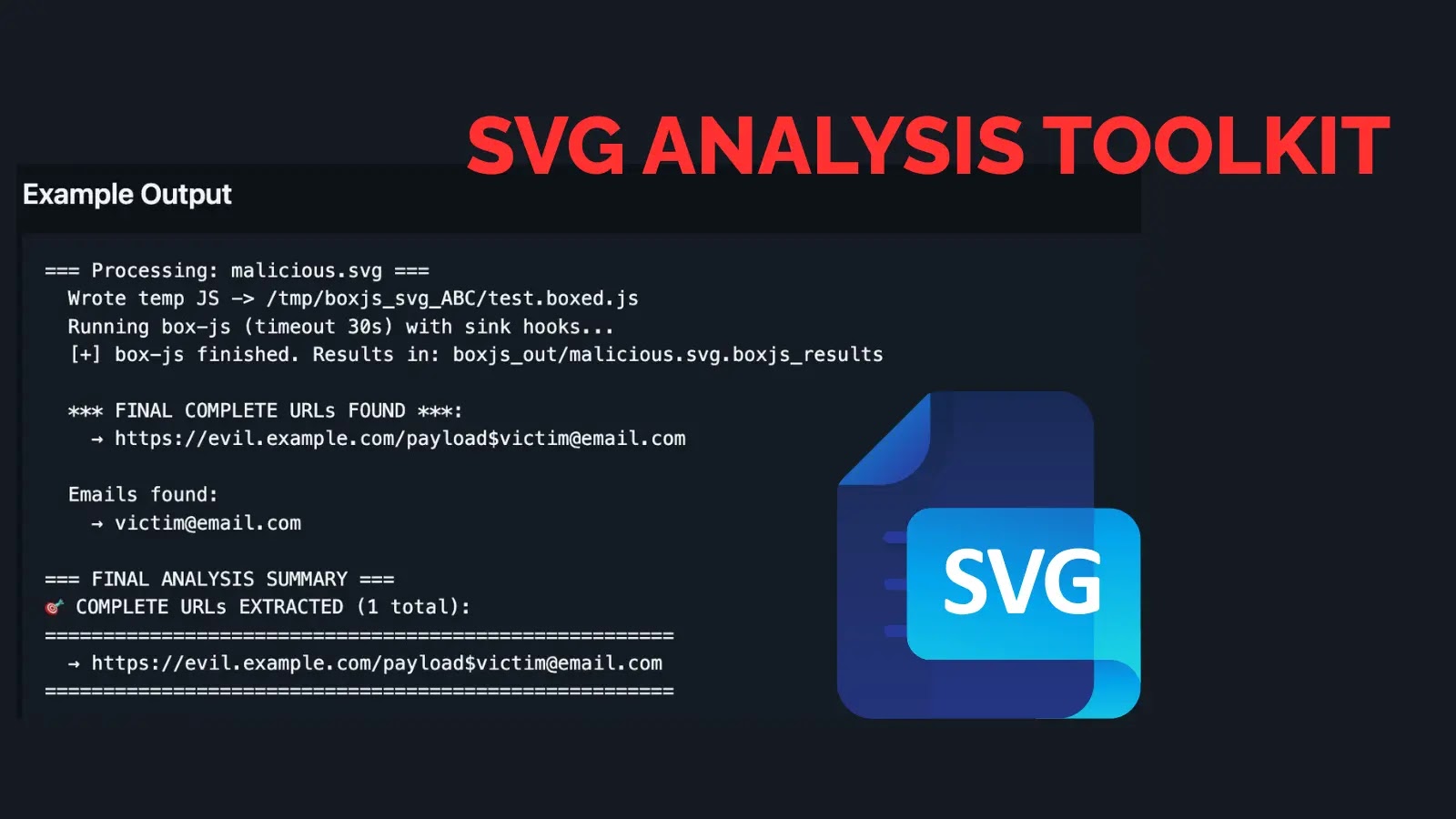
Trend Micro has disclosed a critical vulnerability in its Deep Security 20 Agent software that could potentially allow attackers to execute remote code on affected systems.
The vulnerability was identified as “CVE-2024-51503,” was discovered on November 18, 2024, and has been assigned a high severity rating with a CVSS 3.0 score of 8.0.

The security flaw, classified as a manual scan command injection vulnerability, affects Windows-based Deep Security Agent versions prior to 20.0.1-21510 and the Deep Security Notifier on DSVA version 20.0.0-8438.
This vulnerability could enable an attacker to escalate privileges and execute arbitrary code on compromised machines.
Researchers at Trend Micro observed that the vulnerability, dubbed ZDI-CAN-25215, is rooted in an OS Command Injection weakness (CWE-78).
Maximizing Cybersecurity ROI: Expert Tips for SME & MSP Leaders – Attend Free Webinar
Technical Analysis
It allows attackers with legitimate domain access to potentially inject commands remotely to other machines within the same domain.
However, it’s important to note that exploiting this vulnerability requires an attacker to first gain the ability to execute low-privileged code on the target system.
Trend Micro has promptly addressed the issue by releasing security updates. For the Deep Security Agent, version 20.0.1-21510 (20 LTS Update 2024-10-16) is now available for Windows platforms.
Users of the Deep Security Notifier on DSVA are advised to install the DSA 20.0.1 full package or a later version to update the Notifier function.
Cybersecurity experts emphasize the importance of timely patch application. While exploiting this vulnerability typically requires physical or remote access to a vulnerable machine, Trend Micro strongly urges customers to update to the latest builds as soon as possible.
Additionally, organizations are advised to review remote access policies for critical systems and ensure that perimeter security measures are up-to-date.
The discovery of this vulnerability is credited to Simon Zuckerbraun of Trend Micro’s Zero Day Initiative, highlighting the ongoing efforts within the cybersecurity community to identify and address potential threats.
Security experts urged for the regular software updates and robust security practices in safeguarding digital assets against potential exploits.
Are you from SOC/DFIR Teams? – Analyse Malware Files & Links with ANY.RUN -> Try for Free