A ransomware group recently targeted Cyberport, a business park in China housing numerous digital and technology companies, as well as a retail entertainment complex in Hong Kong.
The company’s authorities confirmed the Cyberport cyber attack, stating in a press release that they detected unauthorized third-party access.
Cyberport is Hong Kong’s flagship enterprise that encourages entrepreneurship with over 1,900 members, over 800 onsite, and 1,100 offsite start-ups. Cyberport is owned by the Hong Kong SAR Government.
Details About the Cyberport Cyber Attack
The Cyberport ransomware attack was claimed by the Trigona group, which added samples of data exfiltrated from the victim’s systems.

Falcon Feeds, a Threat Intelligence platform posted screenshots from the dark web portal of the ransomware group. The above screenshot of blurred samples allegedly from the Cyberport cyber attack showed documents, ID cards, and graphics of users.
The cybercriminals from the Trigona ransomware group demanded a sum of $300,000 against the exfiltrated data. The dark web post reflected a time of 23 days and around 14 hours to make the ransom payment.
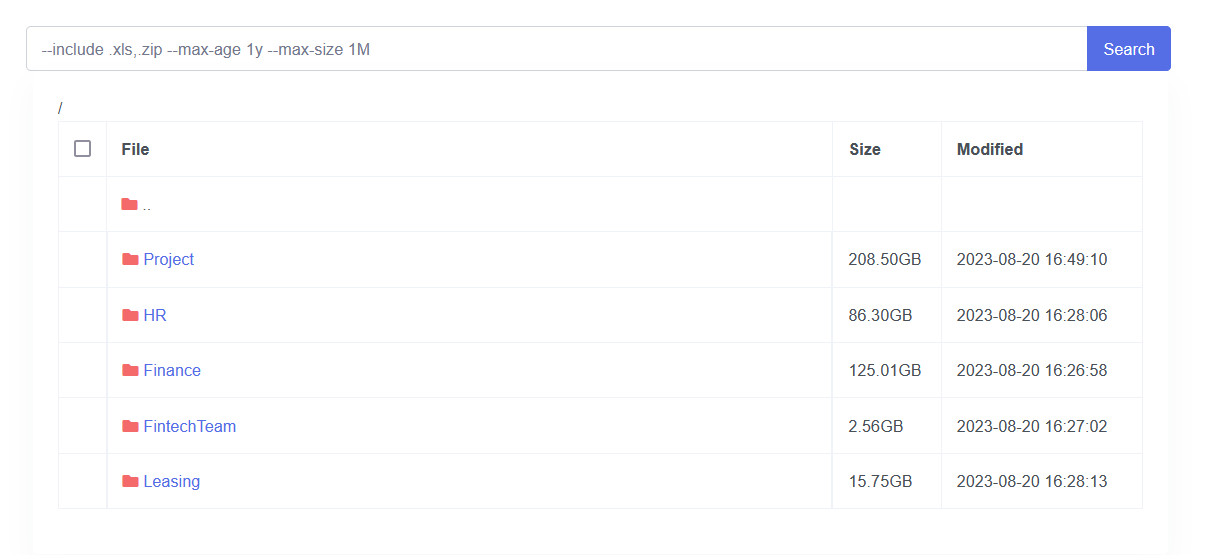
The Trigona ransomware group has been active since October 2022 and has targeted high-profile organizations with strong cybersecurity defences suggesting that they have sophisticated tools to breach most systems.
Among the data types exfiltrated by Trigona during the Cyberport cyber attack were 208.50 GB of project files, 86.30GB of HR-related data, 125.01GB of financial data, 2.56 GB of FinTechTeam data, and 15.75 GB of leasing information.
The stolen data via the Cyberport data breach amounts to over 436GB. The ransomware group threatened to release it all after the deadline of nearly 23 days from the date of posting was over.
What the Cyberport Press Release Read
In an official press release, Cyberport has confirmed the occurrence of a cybersecurity incident, leading to the immediate shutdown of affected computer equipment. The Cyberport data breach has now become the subject of investigation by the Hong Kong Police Force.
Condemning the Cyberport data breach and the samples posted on the dark web, the company wrote, “Cyberport monitored earlier today the circulation of information on the internet suspected to be related to the incident during security surveillance.”
“Cyberport strongly condemns any form of cybercrime and will fully cooperate with law enforcement departments in their investigations,” the press release added.
What We Know About the Trigona Ransomware Group

Cybersecurity Analyst Dominic Alvieri shared a screenshot from Trigona’s updated dark web portal. The captured post confirmed the group’s responsibility for the Cyberport cyber attack.

Besides breaching the security of Cyberport, the Trigona ransomware group named the website of Unimed in Brazil. The Portuguese language website is of a medical work cooperative and health insurance operator.
“It is considered the largest of its kind in the world, with more than 105,000 affiliated physicians, 386 branches, and more than 15 million beneficiaries,” read a World Economic Forum post about Unimed.
Trigona ransomware group allegedly exfiltrated over 12GB of data from the Unimed data breach. The ransomware group stole financial data among others from the Unimed cyber attack.
Trigona demands ransom only in Monero cryptocurrency, wrote a BleepingComputer report. The hackers have been known to employ brute force to guess common login credentials and hack into systems to deploy ransomware.
The developers of the Trigona ransomware have updated it over a span of a year to increase its capabilities in launching cyber attacks.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
