A newly formed ransomware collective calling itself the Trinity of Chaos has published a data leak site (DLS) on the TOR network exposing the stolen records of 39 prominent corporations, including Google Adsense, CISCO, Toyota, FedEx and Disney/Hulu.
The alliance comprises threat actors from Lapsus$, Scattered Spider and ShinyHunters, signaling a shift toward traditional ransomware extortion tactics and raising alarm across multiple industries.
The Trinity of Chaos first emerged by combining the reputations and technical capabilities of three notorious groups.
Although no fresh intrusions have been claimed, the collective released previously unavailable data samples from past breaches, showcasing proof of exfiltrated records.
In one highlighted instance, the group threatened Salesforce following alleged exploitation of its instances via stolen OAuth tokens tied to Salesloft’s Drift AI chat integration.
Salesforce downplayed the claims but acknowledged potential compromises of customer environments. Threat actors claimed to have sought negotiations with the company to avoid disclosure, invoking GDPR obligations and warning of “criminal negligence charges” if regulators were alerted.
Marketing materials posted alongside the DLS tout the trio’s prowess: “Specializing in high-value corporate data acquisition and strategic breach operations,” they proclaimed, citing expertise across automotive, financial, insurance, technology, telecommunications and ISP sectors.
The group asserts operations dating back to 2019, underscoring the sophistication of its long-term intrusion campaigns.
Past victims whose data samples were shared include Vietnam Airlines, which was infiltrated over three years beginning in late 2020, and the National Credit Information Center of Vietnam, where over 160 million records were exposed.
During this period, the group, operating under the alias “1973cn,” which has not been publicly detailed, may also have been responsible for attacks at Noi Bai Airport and Tan Son Nhat Airport.
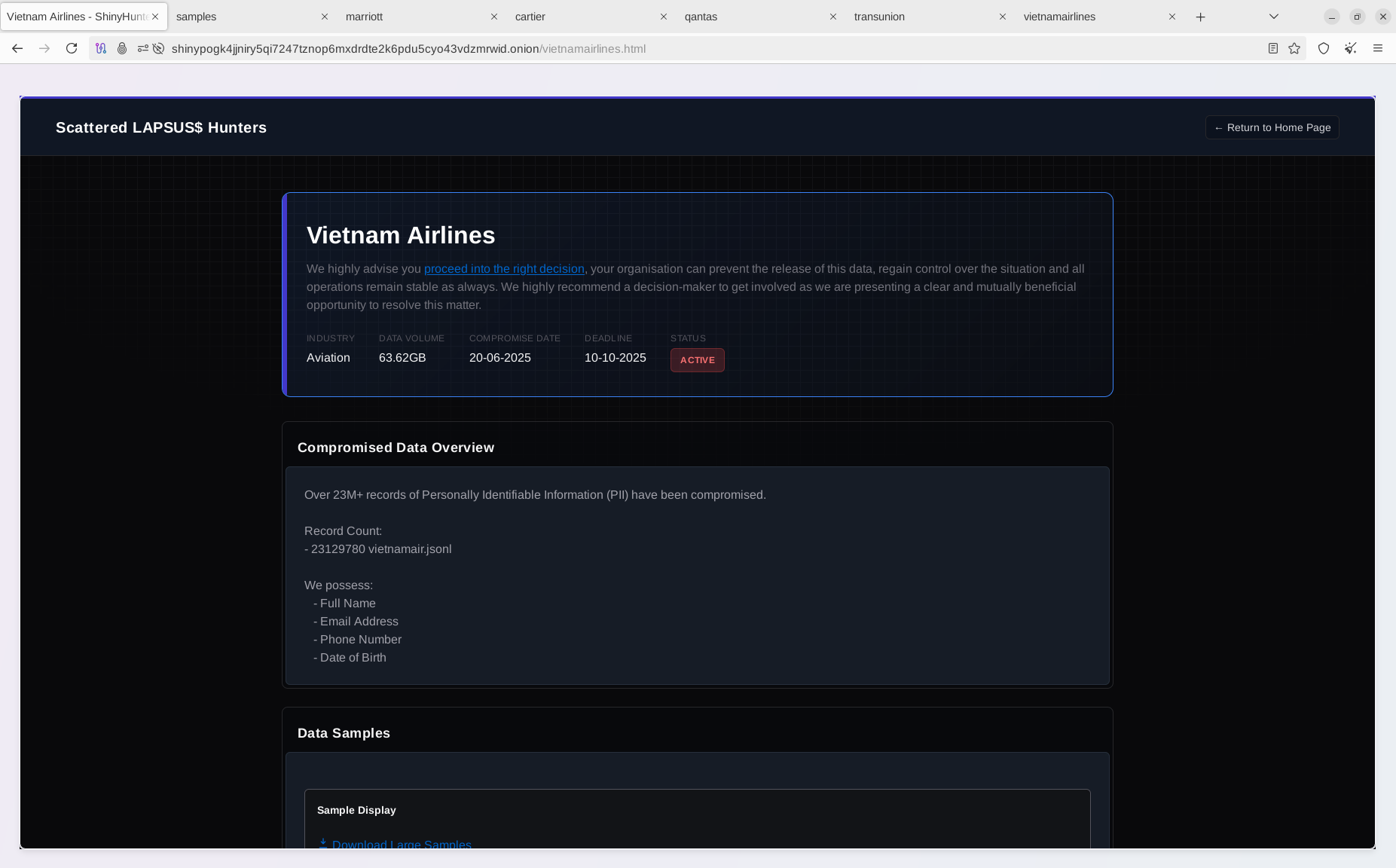
The alliance has also claimed responsibility for breaches of Aeroméxico in July 2025 and Jaguar Land Rover, the latter disrupting vehicle production and retail activities in September. Resecurity’s threat intelligence team validated these breaches and provided technical indicators for detection and response.
Corporations and Negotiation Deadlines
October 3, 2025, marked a critical date for Fortune 100 companies. The DLS lists 39 organizations required to enter ransom negotiations by October 10 to prevent further data publication.
Affected entities span global brands such as UPS, Home Depot, Marriott, McDonald’s, Adidas, Cartier, Chanel and IKEA. Notably, the automotive giant Stellantis confirmed a breach affecting its North American customer data in September, attributing it to a third-party provider compromise.
Victims face potential regulatory inquiries, legal actions and reputational damage, especially in regions with stringent privacy laws.
Google’s corporate Salesforce instance was reportedly compromised in early June, impacting Google AdWords users and digital media partners worldwide, although Google did not specify the affected service initially.
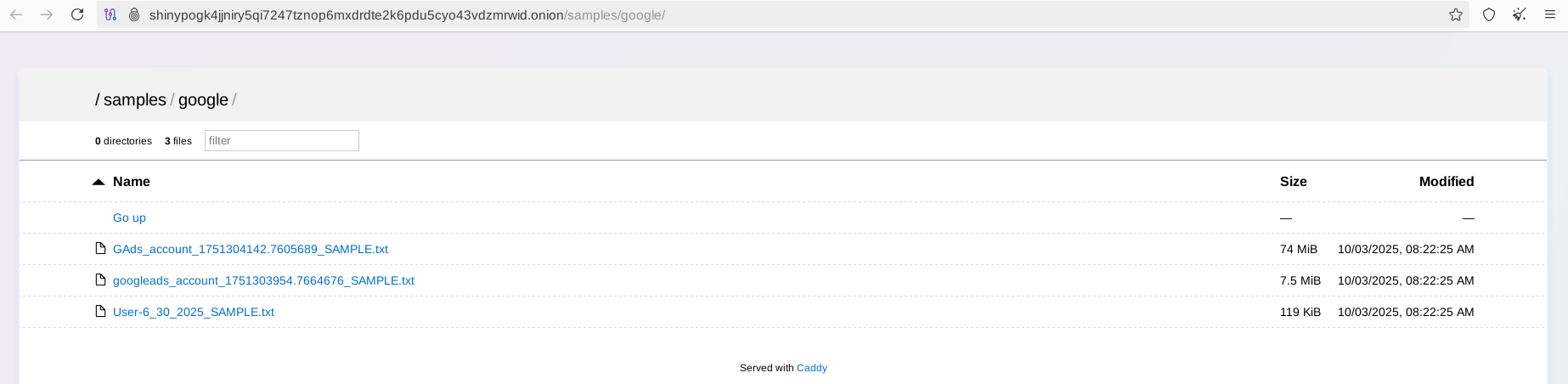

In Cisco’s case, leaked Salesforce records revealed internal communications and customer information, including data on law enforcement and military personnel from agencies such as the FBI, DHS and NASA, as well as international defense organizations.
Actors provided an official contact email previously circulated on Dark Web forums and Telegram channels, instructing victims to use corporate email addresses to verify identity and discuss ransom terms.
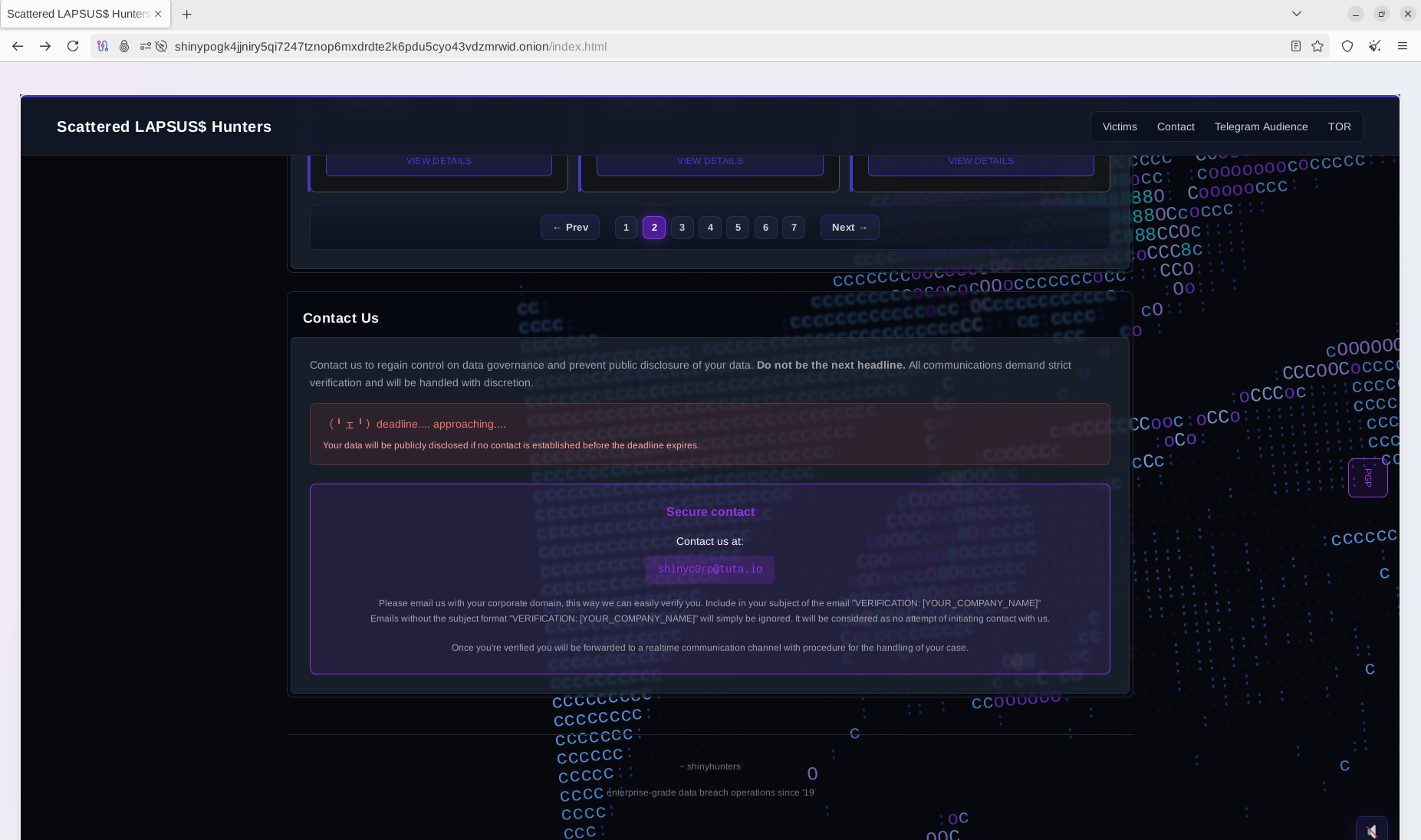

Alongside the DLS launch, the group reactivated its Telegram presence under “SLSH 6.0 Part 3,” promising to expand the leak site after October 10 to include over 1.5 billion records from 760 companies if demands are unmet.
Future Risks and Expert Warnings
Cybersecurity experts warn that publication of these records could fuel large-scale social engineering, phishing campaigns and identity theft.
The leaked data sets, heavily populated with personally identifiable information (PII) but lacking passwords, offer a treasure trove for malicious actors seeking to craft targeted exploits or AI-driven attacks.
The FBI’s flash warning on the exploitation of Salesforce and Salesloft integrations underscores the urgency for organizations to audit their cloud environments and implement robust monitoring.
Industry analysts also note the unfortunate timing of the DLS debut during the U.S. government shutdown, potentially hindering federal agencies’ ability to respond to cybercrime.
Demonstrating resilience, affected organizations are racing to contain fallout, engage forensic teams and bolster defenses against further DDoS or extortion attempts.
As the Trinity of Chaos alliance signals its intention not to re-ransome cooperative victims, the coming weeks will test how far major corporations will go to safeguard sensitive data and preserve customer trust.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



