A significant breakthrough in bypassing Windows activation has been achieved with the introduction of TSforge, a powerful exploit developed by researchers.
This tool is capable of activating every edition of Windows since Windows 7, as well as all Windows add-ons and Office versions since Office 2013.
TSforge represents a major milestone in the history of Windows activation exploits, marking the first time a direct attack on the Software Protection Platform (SPP) has been successfully implemented.
Background on SPP and the CID Trick
The Software Protection Platform (SPP) is a complex system responsible for managing licenses and activation statuses in Windows.
It involves several key components, including sppsvc.exe/slsvc.exe for user-mode services and sppobjs.dll for product key validation.
The researchers’ journey began with the discovery of the “CID trick” in 2023, which allowed them to bypass confirmation ID (CID) validation.

This trick involved patching the CID validation code in sppobjs.dll, enabling the use of a fake CID for activation.
Notably, this activation persisted even after restarting the service, indicating that once written, the activation data was not validated again.

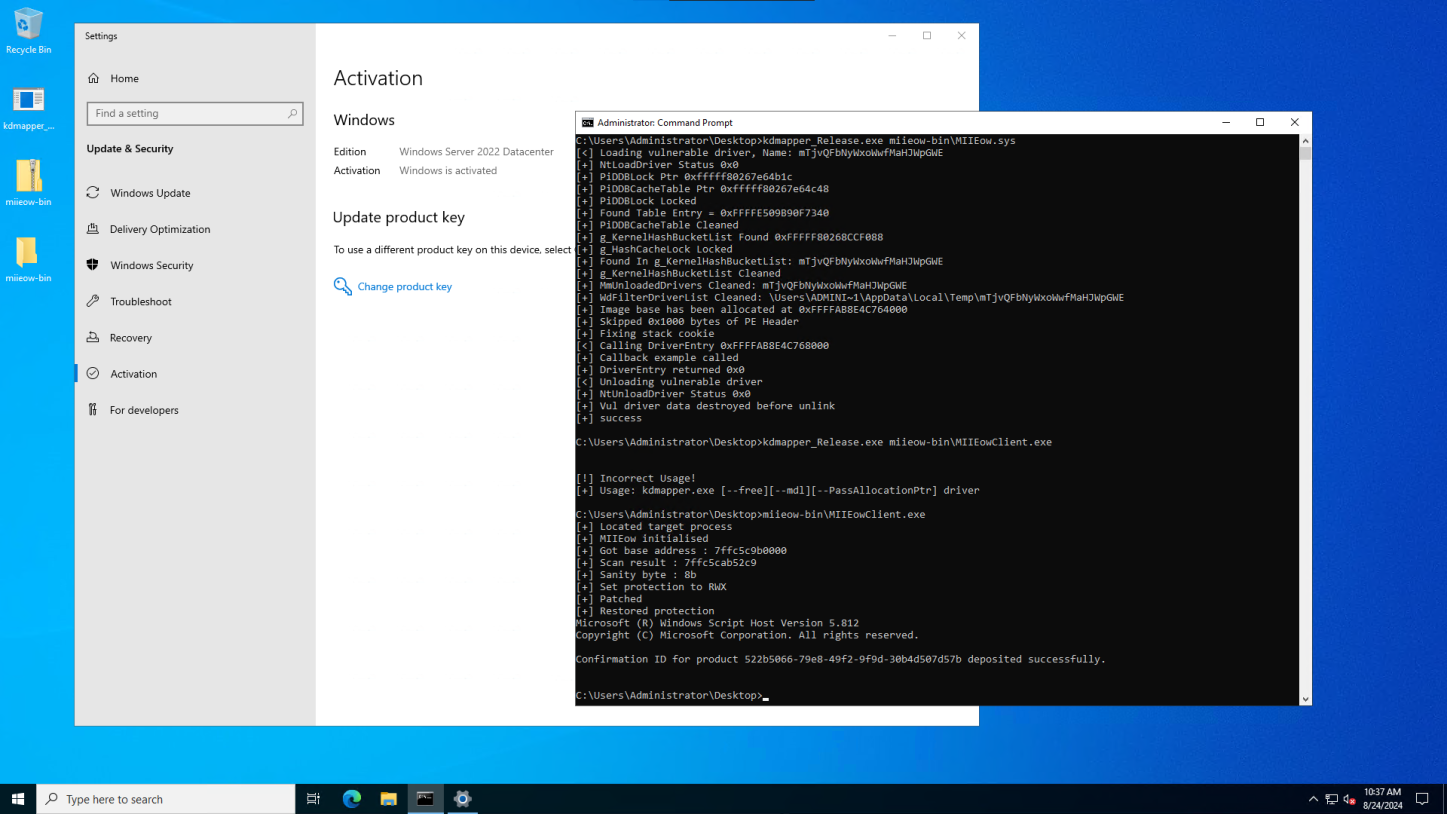
Technical Breakthroughs
To develop TSforge, researchers had to understand where and how activation data was stored.
They identified key locations such as C:WindowsSystem32sppstore2.0data.dat and tokens.dat, along with registry keys under HKEY_LOCAL_MACHINESYSTEMWPA.
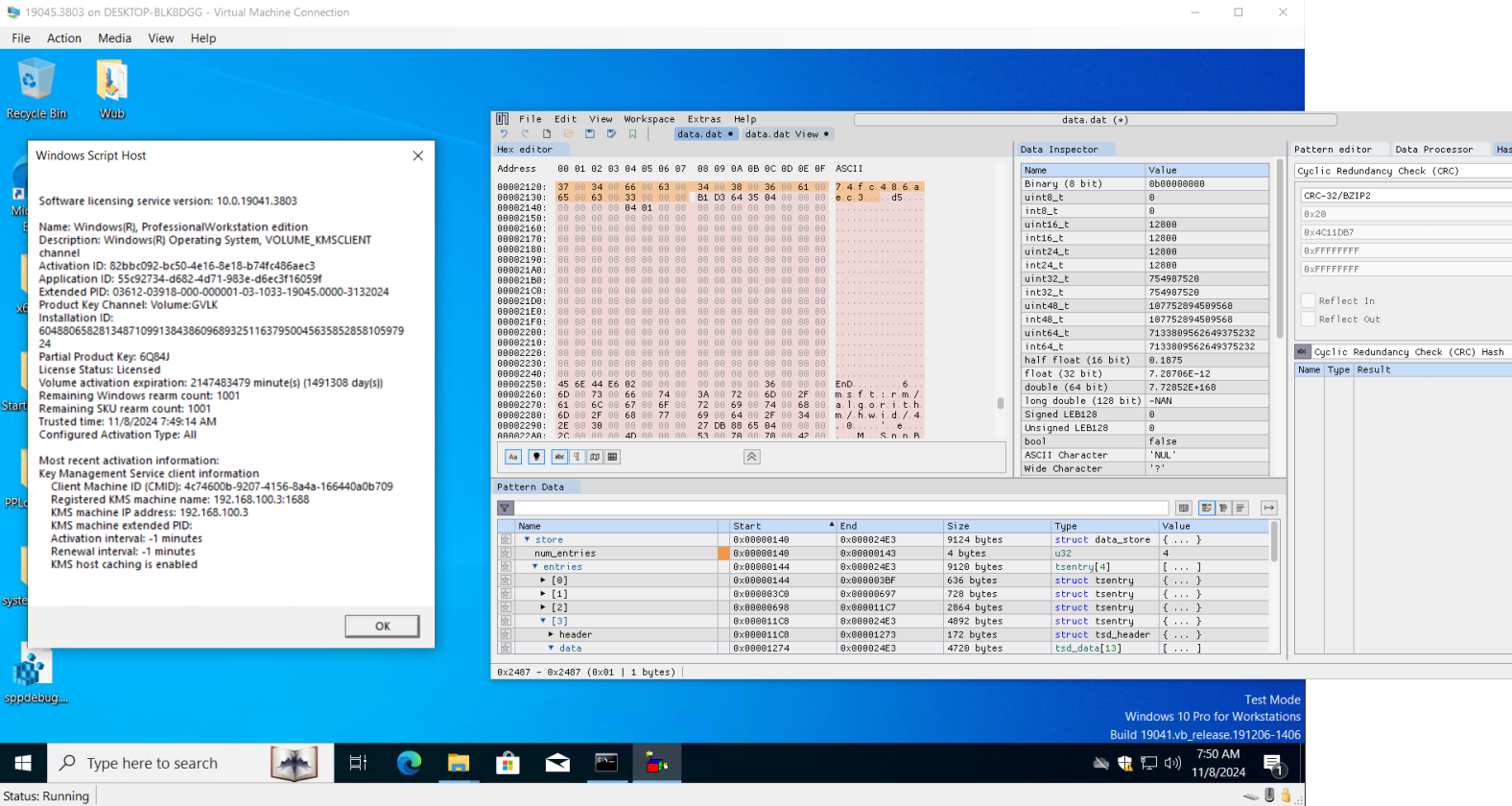
According to MASSGRAVE, these files and keys form the “trusted store,” which holds critical activation data in encrypted form.
The team used leaked Windows beta builds to gain insights into the spsys.sys driver, crucial for understanding how the trusted store operates in older Windows versions.
By reverse-engineering and debugging these components, they uncovered encryption routines and were able to derive private RSA keys necessary for decrypting and re-encrypting the physical store.
With the private keys in hand, the researchers could activate any Windows edition without needing debuggers or kernel exploits.
They also developed methods to bypass hardware ID (HWID) validation and the PKEY2005 encoding system used in older versions.
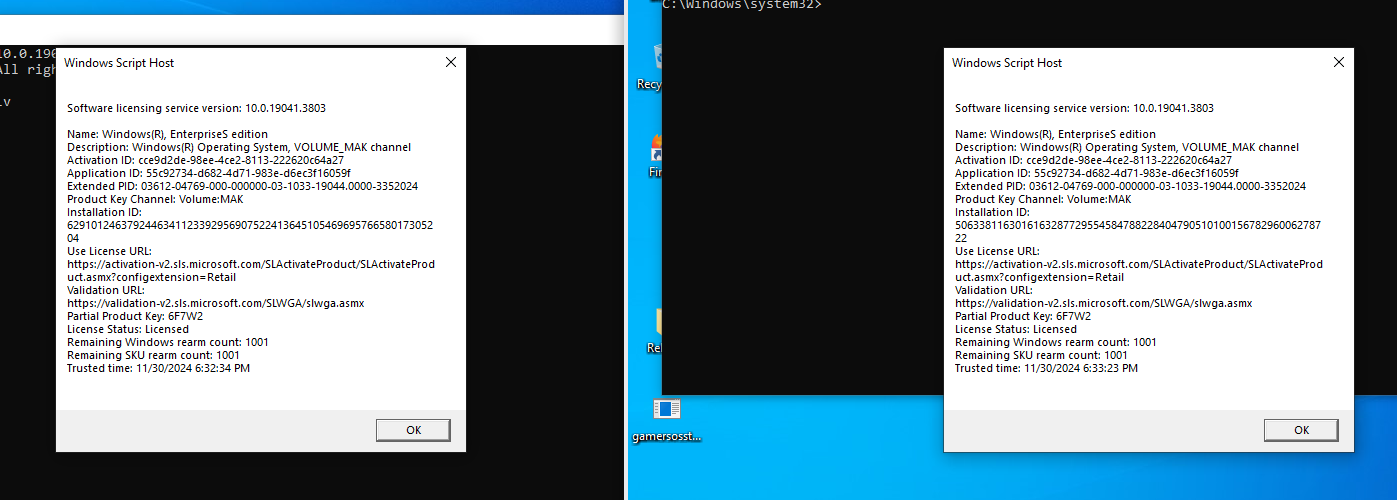

TSforge’s capabilities extend beyond mere activation; it demonstrates a deep understanding of SPP’s internals and highlights vulnerabilities that have been exploited to create a robust activation bypass tool.
Despite the complexity and security of SPP, TSforge shows that with persistence and innovative reverse engineering, even well-built DRM systems can be compromised.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here
