The well-known advanced persistent threat (APT) group Turla, based in Russia, is said to be going after the European Ministry of Foreign Affairs.
This new cyber espionage attempt shows how innovative and persistent Turla is.
The group has been active since 2004 and is known for its high-profile attacks on government agencies and key businesses worldwide.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
The Attack Vector: Microsoft Outlook Exploited
According to Trendmicro reports, the operation, which was due in August 2018, targeted Microsoft Outlook and The Bat!, an Eastern European favorite email client.
Turla wanted to access private information by hacking these sites and sending all outgoing emails to attackers.
This method not only let the group listen in on conversations but also used email to send information to its command and control (C&C) servers.
LunarWeb and LunarMail were used to compromise a European MFA and its diplomatic missions.
A big part of Turla’s strategy in this operation was using specially made PDF files, which were probably also used to do the first breach.
Once they got into the systems, the group used their complex toolkit, which includes backdoors and custom malware, to stay on top of them and keep power over them.
Despite not knowing the whole initial compromise, researchers detected an installation-related component in one of the server compromises: a compiled ASP.NET web page from these source files:
- aspnet_clientsystem_web.aspx
- aspnet_clientsystem_web.cs
System_web.aspx is a known IoC of China-aligned APT Hafnium, which exploits Microsoft Exchange Server vulnerabilities. We think this is a coincidence or false flag.
The system_web.aspx page returns a harmless-looking Zabbix agent log. The SMSKey cookie secretly requires a password. Using the password and salt Microsoft.SCCM.Update.Manager, an AES-256 key, and IV are generated to decode two embedded blobs, which are dropped to two temporary files in a directory restricted from scanning.
Analyzers don’t know the password, but the file sizes match the Stage 1 loader and Stage 2 blob with the LunarWeb backdoor.
After looking at the installers in the last part, look at the loaders, and finish by looking at their payloads, researchers didn’t know about two backdoors before.
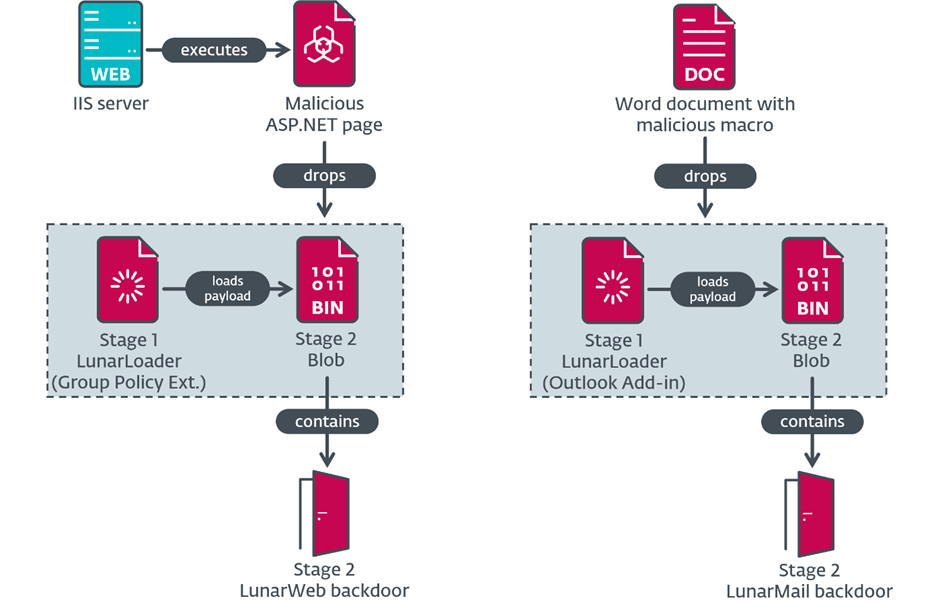
LunarLoader starts the execution sequence.
It decrypts the Stage 2 blob route and reads an encrypted payload using RC4, a symmetric key cipher.
Instead of a mutex or event, it opens and creates a mailslot with a unique name to ensure only one loader instance is active.
The MD5 hash of the computer’s DNS domain name generates and verifies a decryption key.
The payload is decrypted with AES-256 to create a PE file. LunarLoader allocates PE image memory and decrypts an exported PE function name to run in a new thread. The function has a reflective loader.
Payload decryption using DNS is an execution barrier. The loader only works in the intended organization, which may hinder analysis without the domain name.
LunarLoader can run alone or in trojanized open-source software.
The latter occurred with a trojanized AdmPwd, a Windows Local Administrator Password Solution component.
| Persistence method | Loader path(s) | Host process | Note |
| Group policy extension | C:WindowsSystem32en-USwinnet.dll.mui C:Program FilesLAPSCSEAdmPwd.dll* | svchost.exe -k GPSvcGroup | The AdmPwd dll is a known legitimate file path of Microsoft LAPS. |
| System DLL replacement | C:WindowsSystem32tapiperf.dll | wmiprvse.exe | Replacing a legitimate Windows DLL. |
| Outlook add‑in | %USERPROFILE%Gpg4wingpgol.dll | outlook.exe | N/A |
It has been a long time since Turla changed its strategies and tools, which makes it one of the most advanced and tough APT groups.
The group is known for using both common and uncommon malware families, like Carbon and Kazuar, and for having command and control systems that are based on satellites.
Over the years, Turla has regularly targeted government agencies, the military, schools, research labs, and drug companies.
Since this campaign against the European Ministry of Foreign Affairs became public, there have been calls for more cooperation between countries in hacking.
Sharing information and the best ways to do things is seen as very important for countries and groups to fight the threats that come from state-sponsored players like Turla.
Despite sharing a loader, code overlaps, and instructions, the backdoors use different C&C communication techniques. LunarWeb, the first backdoor, employs HTTP(S) to impersonate Windows Update traffic.
LunarMail, the second backdoor, uses PNG or PDF files to steal data from Outlook via email.
MITRE ATT&CK techniques
This table was built using version 15 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Reconnaissance | T1591 | Gather Victim Org Information | LunarMail’s communication method indicates prior knowledge about compromised institutions. |
| Resource Development | T1583.002 | Acquire Infrastructure: DNS Server | Stage 0 macro pings a domain from free DNS hosting provided by ClouDNS. |
| T1583.003 | Acquire Infrastructure: Virtual Private Server | Turla has used VPS hosting providers for C&C servers. | |
| T1584.003 | Compromise Infrastructure: Virtual Private Server | Turla has used compromised VPSes for C&C purposes. | |
| T1586.002 | Compromise Accounts: Email Accounts | Turla has used likely compromised email accounts for communication with the LunarMail backdoor. | |
| T1587.001 | Develop Capabilities: Malware | Turla has developed custom malware, including loaders and backdoors. | |
| Execution | T1047 | Windows Management Instrumentation | LunarWeb obtains system information by using WMI queries. |
| T1059 | Command and Scripting Interpreter | LunarWeb and LunarMail can execute Lua scripts. | |
| T1059.001 | Command and Scripting Interpreter: PowerShell | LunarWeb can execute PowerShell commands. | |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | LunarWeb can execute shell commands via cmd.exe. | |
| T1059.005 | Command and Scripting Interpreter: Visual Basic | Stage 0 Word document contains a VBA macro. | |
| T1106 | Native API | LunarWeb and LunarMail use various Windows APIs. | |
| T1204.002 | User Execution: Malicious File | Data from the Local System | |
| Persistence | T1137.006 | Office Application Startup: Add-ins | LunarMail loader is persisted as an Outlook add-in. |
| T1547 | Boot or Logon Autostart Execution | A LunarWeb loader is persisted as a Group Policy extension. | |
| T1574 | Hijack Execution Flow | A LunarWeb loader is persisted by replacing the system DLL tapiperf.dll. | |
| Defense Evasion | T1027 | Obfuscated Files or Information | LunarWeb and LunarMail are AES-256 encrypted on disk. |
| T1027.003 | Obfuscated Files or Information: Steganography | LunarMail stages exfiltration data into a PNG image or PDF document. | |
| T1027.007 | Obfuscated Files or Information: Dynamic API Resolution | LunarMail dynamically resolves MAPI functions. | |
| T1027.009 | Obfuscated Files or Information: Embedded Payloads | LunarMail installer has payloads embedded in a DOCX format document. | |
| T1036.005 | Masquerading: Match Legitimate Name or Location | Filenames used by LunarWeb and LunarMail loading chains mimic legitimate files. | |
| T1070.004 | Indicator Removal: File Deletion | LunarWeb and LunarMail can uninstall themselves by deleting their loading chain. | |
| T1070.008 | Indicator Removal: Clear Mailbox Data | LunarMail deletes email messages used for C&C communications. | |
| T1140 | Deobfuscate/Decode Files or Information | LunarWeb and LunarMail decrypt their strings using RC4. | |
| T1480.001 | Execution Guardrails: Environmental Keying | LunarLoader decrypts its payload using a key derived from the DNS domain name. | |
| T1620 | Reflective Code Loading | LunarWeb and LunarMail are executed using a reflective loader. | |
| Discovery | T1007 | System Service Discovery | LunarWeb retrieves a list of services. |
| T1016 | System Network Configuration Discovery | LunarWeb retrieves network adapter information. | |
| T1057 | Process Discovery | LunarWeb retrieves a list of running processes. | |
| T1082 | System Information Discovery | LunarWeb retrieves system information such as OS version, BIOS version, domain name, and environment variables. LunarMail retrieves environment variables. | |
| T1518.001 | Software Discovery: Security Software Discovery | LunarWeb discovers installed security solutions via the WMI query wmic /Namespace:\rootSecurityCenter2 Path AntiVirusProduct Get *. | |
| Collection | T1005 | LunarWeb and LunarMail use a statically linked Zlib library for compression of collected data. | LunarWeb and LunarMail can upload files from the compromised machine. |
| T1074.001 | Data Staged: Local Data Staging | LunarMail stages data in a directory in %TEMP%. | |
| T1113 | Screen Capture | LunarMail can capture screenshots. | |
| T1114.001 | Email Collection: Local Email Collection | LunarMail collects recipients of sent email messages and can collect email addresses of Outlook profiles. | |
| T1560.002 | Archive Collected Data: Archive via Library | LunarWeb and LunarMail use a statically linked Zlib library for the compression of collected data. | |
| Command and Control | T1001.002 | Data Obfuscation: Steganography | LunarWeb can receive commands hidden in JPG or GIF images. LunarMail receives commands hidden in PNG images and exfiltrates data hidden in PNG images or PDF documents. |
| T1001.003 | Data Obfuscation: Protocol Impersonation | LunarWeb impersonates legitimate domains in C&C communications by using a fake Host header and known URIs. | |
| T1071.001 | Application Layer Protocol: Web Protocols | LunarWeb uses HTTP for C&C communications. | |
| T1071.003 | Application Layer Protocol: Mail Protocols | LunarMail uses email messages for C&C communications. | |
| T1090.001 | Proxy: Internal Proxy | LunarWeb can use an HTTP proxy for C&C communications. | |
| T1095 | Non-Application Layer Protocol | Stage 0 macro pings the C&C server, utilizing ICMP protocol. | |
| T1132.001 | Data Encoding: Standard Encoding | LunarWeb may receive base64-encoded data from the C&C server. | |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | LunarWeb and LunarMail encrypt C&C communications using AES-256. | |
| T1573.002 | Encrypted Channel: Asymmetric Cryptography | LunarWeb and LunarMail encrypt the AES key used in C&C communications using RSA-4096. | |
| Exfiltration | T1020 | Automated Exfiltration | LunarWeb and LunarMail automatically exfiltrate collected data to the C&C server. |
| T1030 | Data Transfer Size Limits | LunarWeb splits exfiltrated data above 1.33 MB into multiple smaller chunks. LunarMail limits the size of email attachments containing exfiltrated data. | |
| T1041 | Exfiltration Over C2 Channel | LunarWeb and LunarMail exfiltrate data over the C&C channel. |
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free
