A new malicious campaign has been unveiled, targeting the vast user base of the online gaming platform Roblox.
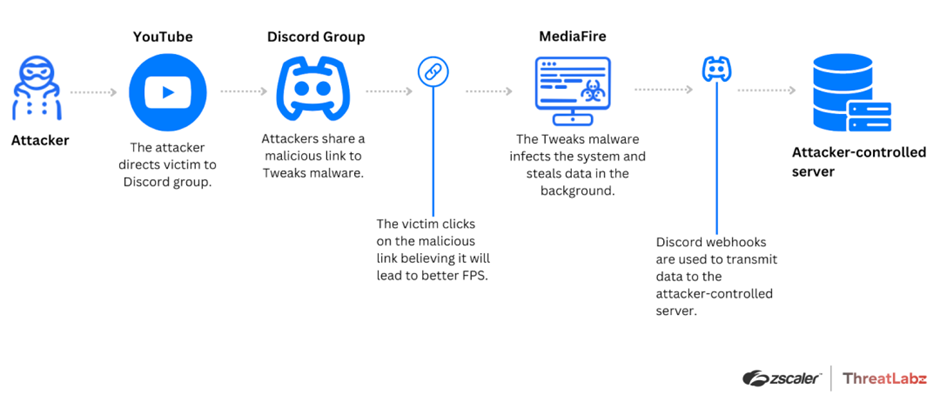
This campaign distributes an infostealer malware, known as Tweaks or Tweaker, exploiting the popularity of platforms like YouTube and Discord to reach its victims.
This strategy allows the attackers to bypass traditional web filters that block known malicious servers, making the campaign particularly insidious.
Roblox, a platform that boasts millions of players worldwide, offers many games and experiences.
A significant feature attracting players is the promise of enhanced gameplay through improved Frames Per Second (FPS).
Attackers exploit this desire for a smoother gaming experience, tricking users into downloading malware disguised as FPS optimization tools.
Exploiting YouTube and Discord
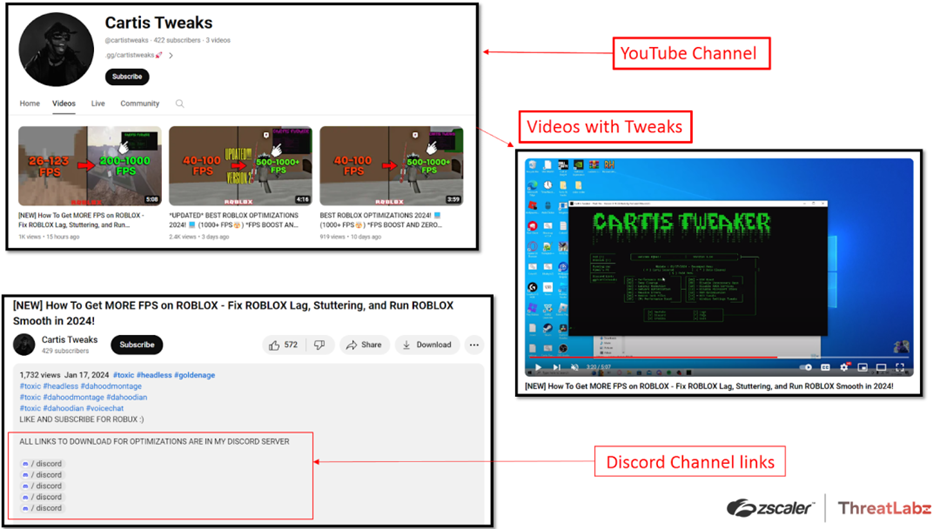
Attackers have cleverly utilized YouTube, creating videos that guide users on increasing their FPS in Roblox.
These videos often suggest disabling antivirus software to ensure the smooth operation of the so-called “PC optimizer,” a tactic designed to leave systems vulnerable to malware.
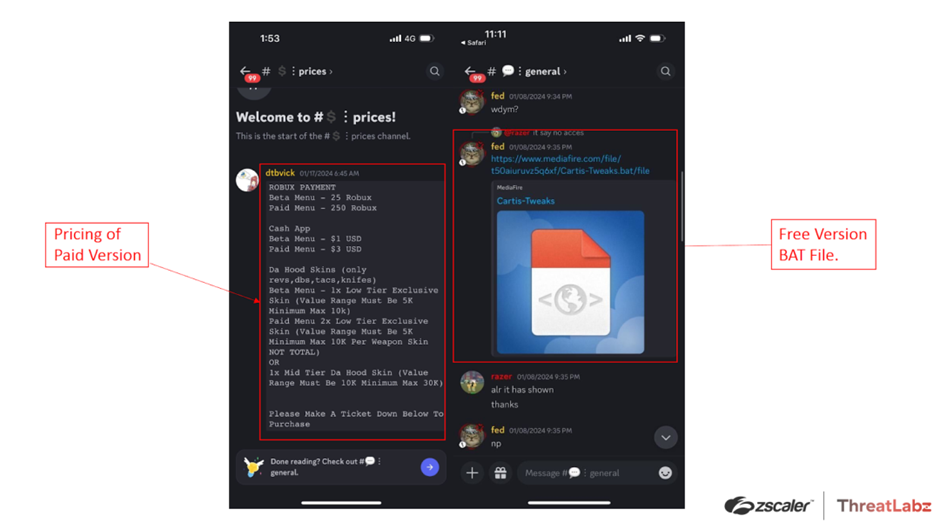
The video descriptions contain links to Discord groups controlled by the attackers, where users are further enticed with free and paid versions of the optimization files.
Unbeknownst to the users, downloading these files results in installing the Tweaks malware.
Zscaler’s ThreatLabz has identified a new malicious campaign that distributes an infostealer named Tweaks (also known as Tweaker) which is designed to target users of Roblox, a popular online gaming platform.
The malware steals sensitive information from the infected device and sends it to the command and control server.
Once infected, the malware operates in the background, stealing sensitive data while ostensibly enhancing the gaming experience.
This dual functionality makes the malware less likely to raise suspicion among its victims.
Technical Breakdown
The Tweaks malware is particularly nefarious, capable of stealing a wide range of data, including Wi-Fi profiles and passwords, user location, system information, Roblox IDs, and in-game currency details.
It employs PowerShell-based scripts to exfiltrate this data, sending it to attacker-controlled servers via Discord webhooks.
Two case studies highlight the malware’s distribution methods:
One involves a malicious BAT file downloaded from a Mediafire link, and another sells the malware directly on Discord, disguised as an EXE file within a ZIP archive.
Both methods result in the theft of sensitive information, with the latter also causing financial loss to those opting for the paid version.
Mitigation and Recommendation
The campaign underscores the importance of vigilance when downloading software from the Internet, especially from generally considered safe platforms like YouTube and Discord.
Users are advised to download apps only from reputable sources and to be wary of disabling antivirus software.
By taking these precautions, gamers can protect themselves from such malware threats.
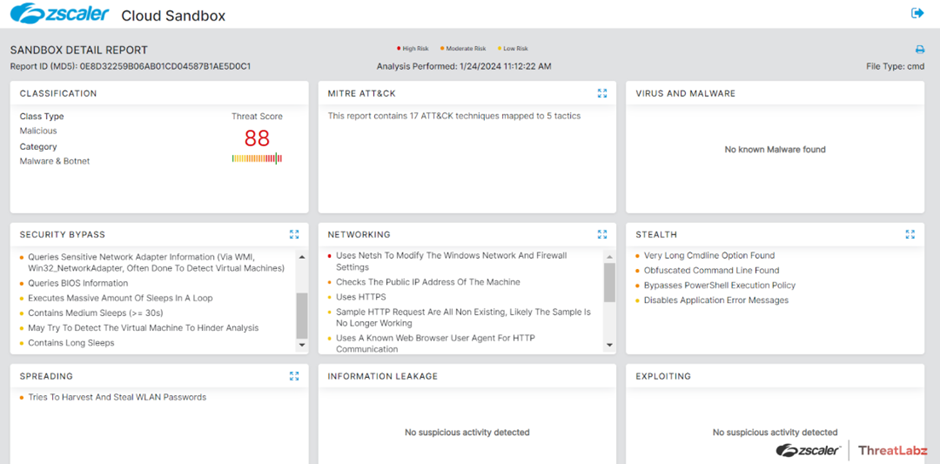
Zscaler Sandbox’s analysis of this campaign has been instrumental in understanding the behavior and impact of the Tweaks malware, highlighting the need for robust cybersecurity measures in the face of evolving online threats.
In the digital age, where online gaming continues to grow in popularity, the Tweaks Stealer campaign is a stark reminder of the cybersecurity risks that come with it.
As attackers become more sophisticated in their methods, users and platforms must stay one step ahead to ensure a safe gaming environment.
IOCs
| MD5 | File type |
| e35864892846be3462139f9534d5ddb5 | EXE |
| 0e8d32259b06ab01cd04587b1ae5d0c1 | BAT |
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter
