The Idaho National Laboratory (INL) confirmed that attackers stole the personal information of more than 45,000 individuals after breaching its cloud-based Oracle HCM HR management platform last month.
INL is one of 17 U.S. Department of Energy’s (DOE’s) national laboratories, and it employs 6,100 researchers and support staff involved in national security and nuclear research.
On November 20, it confirmed a “cybersecurity data breach” that impacted its off-site Oracle HCM system one day before. CISA and FBI are looking into its impact as part of an ongoing joint investigation.
The research lab says in breach notification letters filed with the Maine Attorney General’s Office this week that the attackers exfiltrated the data of 45,047 current and former employees (including postdocs, graduate fellows, and interns), as well as their dependents and spouses. The breach did not affect employees hired after June 1, 2023.
While the laboratory is still investigating the incident’s full impact, it said that multiple forms of sensitive personally identifiable information (PII) was affected, including names, social security numbers, salary information, and banking details.
“The event did not impact INL’s own network, or other networks or databases used by employees, lab customers or other contractors. The breach only impacted the cloud-based Oracle HCM test environment that resides off-site. “INL said.
“A well-known hacking organization has taken responsibility via social media, but a full investigation must be completed to confirm this information.”
Even though INL hasn’t attributed the attack to a specific group, SiegedSec hacktivists claimed the attack on November 20 and leaked stolen human resources data on a hacking forum.
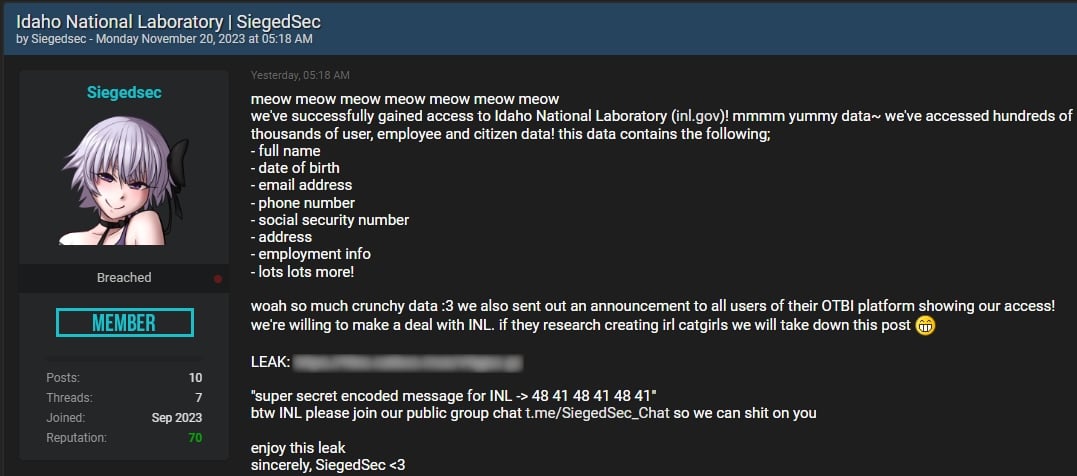
Just as they did when they leaked data allegedly stolen from NATO and Atlassian, SiegedSec has made no attempt to negotiate or demand a ransom from INL, directly publishing it online instead.
They provided evidence of their access to INL’s systems by sharing a custom announcement they made using INL’s system to notify everyone on the campus, along with screenshots of internal INL tools.
SiegedSec claims the data they leaked online includes a wide range of sensitive information, including affected individuals’ full names, dates of birth, email addresses, phone numbers, Social Security Numbers (SSN), physical addresses, and employment information.
