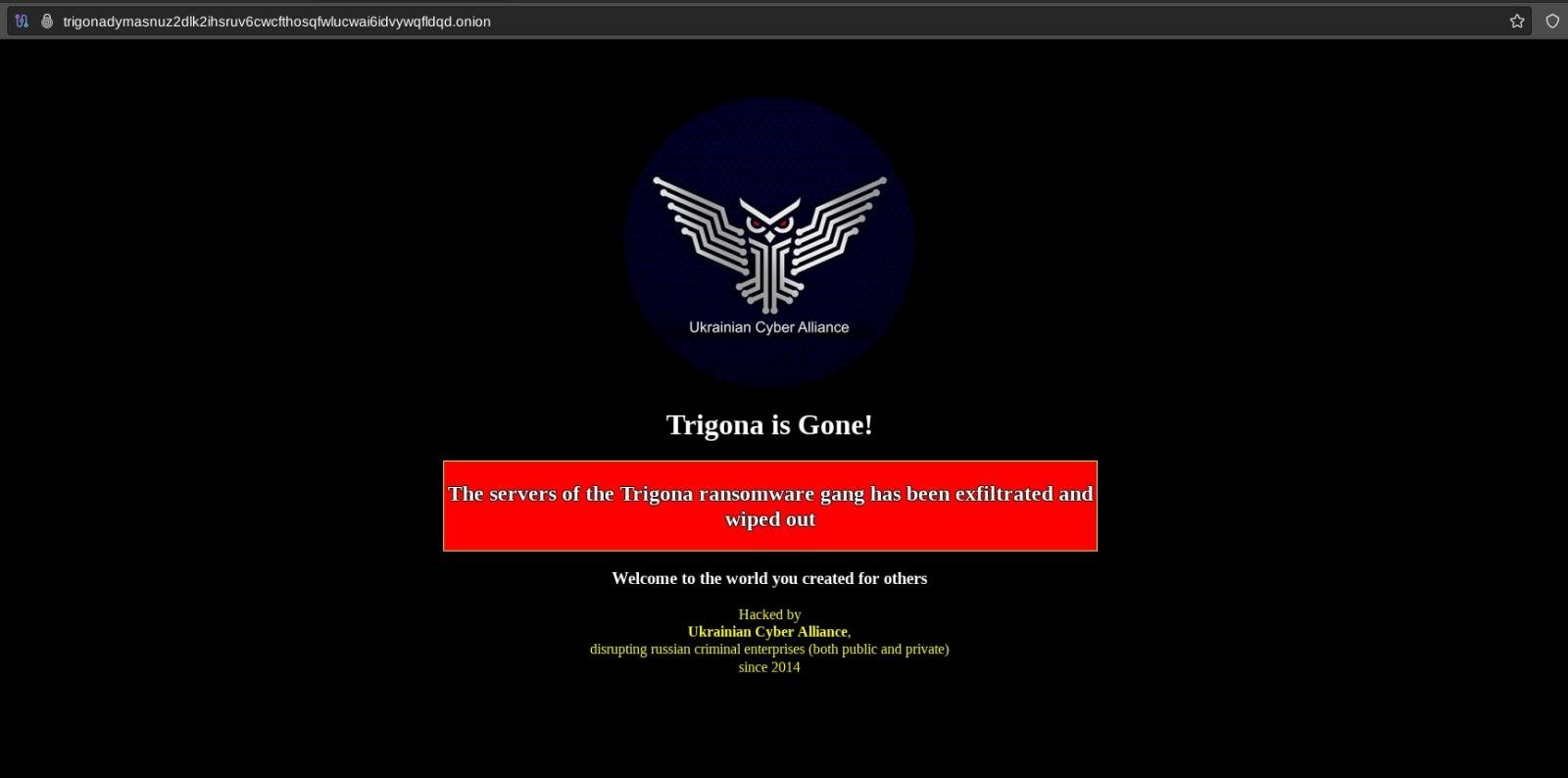
A group of cyber activists under the Ukrainian Cyber Alliance banner has hacked the servers of the Trigona ransomware gang and wiped them clean after copying all the information available.
The Ukrainian Cyber Alliance fighters say they exfiltrated all of the data from the threat actor’s systems, including source code and database records, which may include decryption keys.
Trigona ransomware out of commission
Ukrainian Cyber Alliance hackers gained access to Trigona ransomware’s infrastructure by using a public exploit for CVE-2023-22515, a critical vulnerability in Confluence Data Center and Server that can be leveraged remotely to escalate privileges.
The vulnerability was leveraged in attacks as a zero-day since September 14 by at least one threat group that Microsoft tracks as Storm-0062 (also known as DarkShadow and Oro0lxy).
The Ukrainian Cyber Alliance, or UCA for short, first breached Trigona ransomware’s Confluence server about six days ago, established persistence, and mapped the cybercriminal’s infrastructure completely unnoticed.
After a UCA activist using the handle herm1t published screenshots of the ransomware gang’s internal support documents, BleepingComputer was told that Trigona ransomware initially panicked and responded by changing the password and taking down its public-facing infrastructure.
However, over the next week, the activists managed to take all the information from the threat actor’s administration and victim panels, their blog and data leak site, and internal tools (Rocket.Chat, Jira, and Confluence servers).
herm1t told BleepingComputer that they also exfiltrated the developer environment, cryptocurrency hot wallets as well as the source code and database records.
The activists don’t know if the information they transferred contains any decryption keys but they said they would release them if found.
After harvesting all available data from the ransomware gang, the UCA activists deleted and defaced their sites, also sharing the key for the administration panel site.
source: herm1t
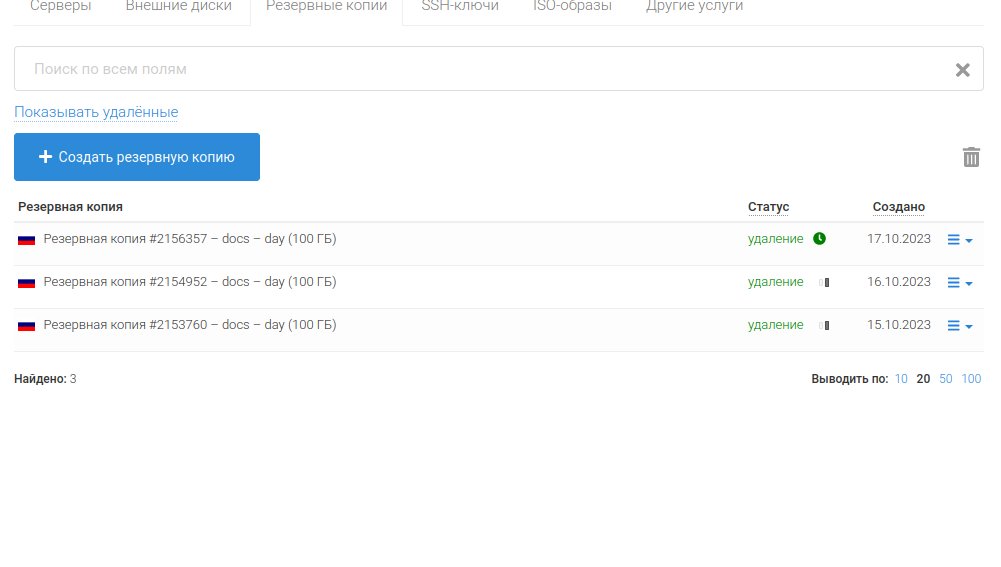
UCA claims that they were able to retrieve three backups with hundreds of gigabytes of likely stolen documents.
source: herm1t
The Ukrainian Cyber Alliance
Starting in 2014, multiple hacktivists in Ukraine and around the world started working together to defend the country’s cyberspace against Russian aggression.
About two years later, individual hackers and several hacker groups united to form the Ukrainian Cyber Alliance, now registered as a non-governmental organization, and began to target various organizations and individuals supporting Russia’s activity against Ukraine.
The identities of the members of the group are secret, except for those that set it up as an official entity whose work is governed by the civic duty for the country.
According to the organization’s Wikipedia page, its members carried out multiple successful hacking operations that resulted in exposing information about Russian activity and propaganda efforts in Ukraine and other countries, as well as its control over various individuals and entities.
Among UCA’s claims are hacking the Russian Ministry of Defense twice in 2016 and leaking public defense contracts and confidential data on the provision of the state defense order of 2015–2016.
Another success was hacking the emails of Vladislav Surkov, an individual believed to have designed the machinery for the Russian propaganda of the past years, where he discussed the annexation of Crimea and how to fund the Luhansk and Donetsk territories when they became Russian republics.
Trigona ransomware activity
The Trigona ransomware operation emerged under this name in late October last year, when the gang launched a Tor site to negotiate ransom payments in Monero cryptocurrency with victims of their attacks.
Previously, samples of the malware had no specific name and were observed in the wild since the beginning of 2022. Before the Trigona branding, the operators used email to negotiate the ransom payments.
For a while, the cybercriminals were sufficiently active to compromise in a single month at least 15 companies in the manufacturing, finance, construction, agriculture, marketing, and high technology sectors.
Earlier this year, Trigona hackers were targeting Microsoft SQL servers exposed on the public internet using brute-force or dictionary attacks to obtain access credentials.
At the moment, due to the Ukrainian Cyber Alliance’s recent actions, none of the Trigona ransomware public websites and services are online.
