A Ukrainian national has been extradited from Spain to the United States to face charges over allegedly conducting Nefilim ransomware attacks against companies.
The suspect, Artem Aleksandrovych Stryzhak, 35, was arrested in Spain in June 2024 and extradited to the U.S. on April 30, 2025.
According to the U.S. Department of Justice, Stryzhak allegedly participated in ransomware attacks that targeted high-revenue companies, primarily in the United States, Norway, France, Switzerland, Germany, and the Netherlands.
In June 2021, Stryzhak allegedly became an affiliate of the Nefilim ransomware operation in exchange for 20% of any ransom payments he generated from attacks.
Stryzhak and his co-conspirators researched potential targets using online platforms to gather information about a company’s revenue, size, and contact details. One of the more popular sites used by ransomware gangs to research targets is Zoominfo.
“In one exchange with Stryzhak in or about July 2021, a Nefilim administrator encouraged him to target companies in these countries with more than $200 million in annual revenue,” reads the DOJ’s press release.
When conducting attacks, Nefilim affiliates breach corporate networks, steal data, and then encrypt devices using the ransomware encryptor. The attackers then demand a ransom payment in bitcoin to receive the decryption key and for stolen data not to be leaked. If a victim refuses to pay, the attackers publish the stolen data online on data leak sites.
The Nefilim ransomware launched in 2020, sharing much of its code with the Nemty ransomware. The ransomware encrypted files using AES-128 encryption and appended the “.NEFILIM” file extension to encrypted files.
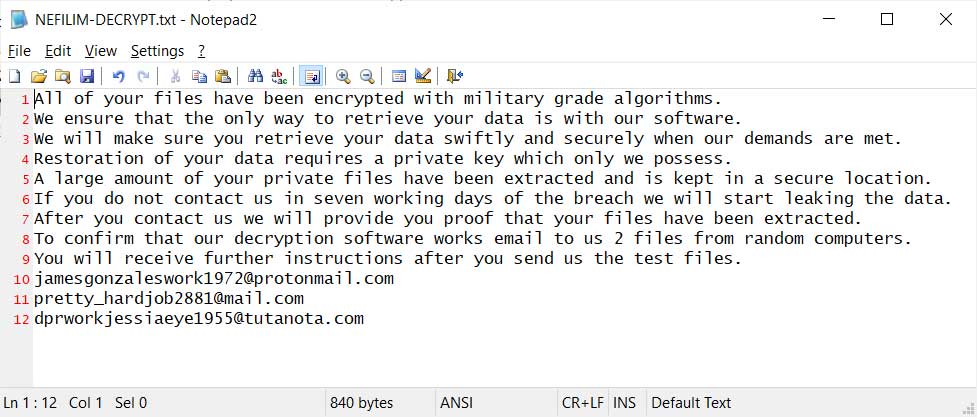
Ransom notes named “NEFILIM-DECRYPT.txt” were created throughout the device’s file system, warning that stolen data would be leaked within seven days if negotiations were not started.
Source: BleepingComputer
Nefilim is believed to have later rebranded under other names, including Fusion, Milihpen, Gangbang, Nemty, and Karma.
Some companies hit by Nefilim attacks include Toll Group, Orange, and Whirlpool.
Stryzhak is charged with conspiracy to commit fraud and related activity, including extortion, in connection with computers. The indictment was unsealed in federal court in Brooklyn, where Stryzhak is scheduled for arraignment before U.S. Magistrate Judge Robert M. Levy.
If convicted, Stryzhak faces up to five years in prison.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
