Ukraine’s Computer Emergency Response Team (CERT-UA) is warning about highly targeted attacks employing compromised Signal accounts to send malware to employees of defense industry firms and members of the country’s army forces.
The bulletin mentions that the attacks started this month, with Signal messages containing archives posing as meeting reports.
With some of these messages sent from existing contacts targets are familiar with, the chances of them opening the archives are higher.
The archive contains a PDF and an executable file, the first acting as a lure for victims to open and trigger the launching of the second.
The executable is classified as the DarkTortilla cryptor/loader, which, when launched, decrypts and executes the remote access trojan Dark Crystal RAT (DCRAT).
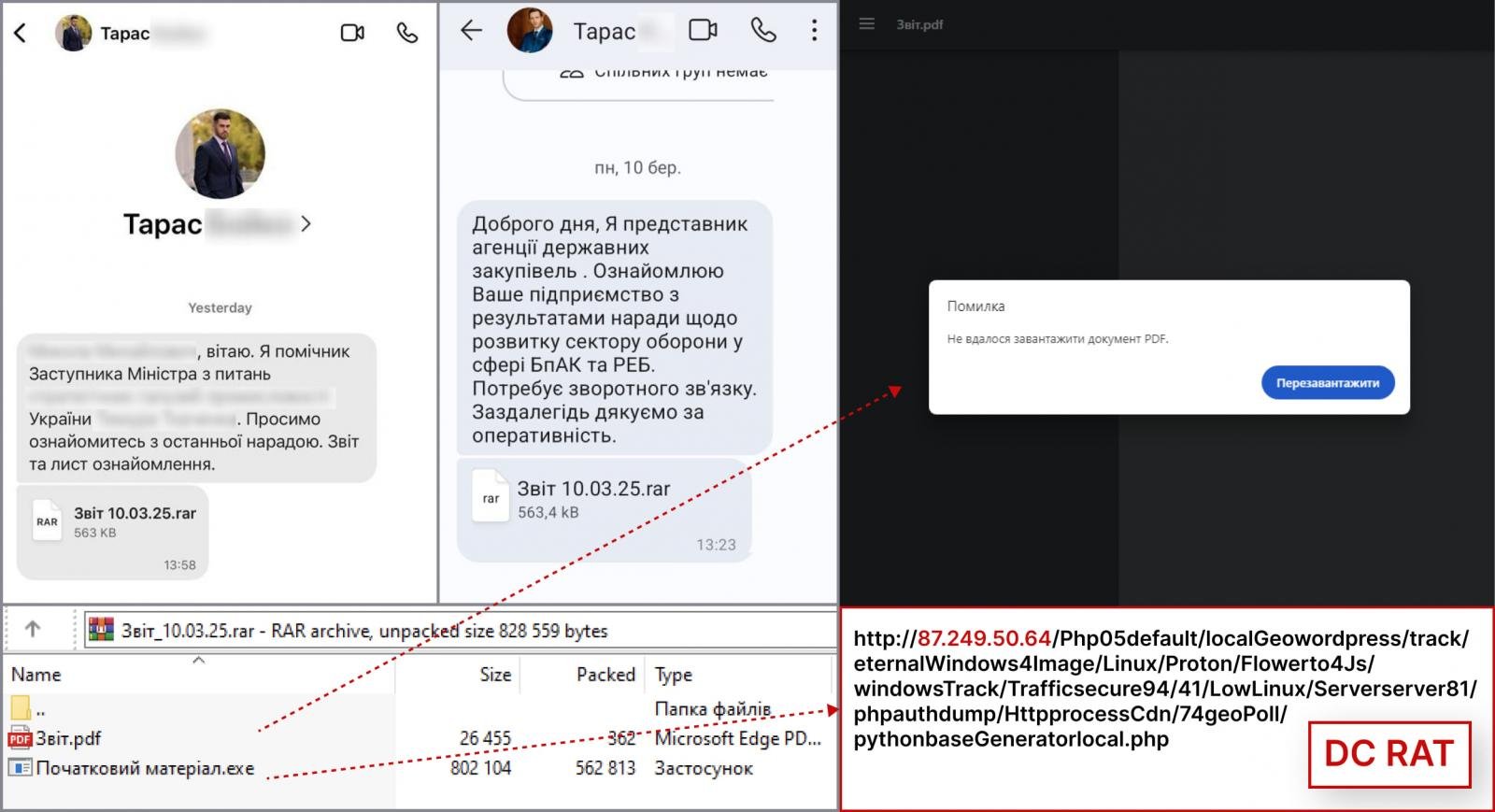
Source: CERT-UA
CERT-UA says the activity has been tracked under UAC-0200, a threat cluster employing Signal in similar attacks since June 2024.
However, in recent attacks, the phishing lures have been updated to reflect current vital topics in Ukraine, especially those related to the military sector.
“Starting in February 2025, the bait messages have shifted their focus to topics related to UAVs, electronic warfare systems, and other military technologies,” explains CERT-UA in its recent bulletin.
In February 2025, Google Threat Intelligence Group (GTIG) reported that Russian hackers were abusing the legitimate “Linked Devices” feature in Signal to gain unauthorized access to accounts of interest.
Signal users who consider themselves potential targets of espionage and spear-phishing attacks should turn off automatic downloads of attachments and be cautious of all messages, especially those containing files.
Additionally, it is recommended that the list of linked devices on Signal be regularly checked to avoid becoming a proxy for attacks.
Finally, Signal users should update their messenger apps to the latest version on all platforms and enable two-factor authentication for additional account protection.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
