A Raspberry Pi device that was directly attached to an internal network switch was used by the financially motivated threat actor group UNC2891 to breach ATM networks in a sophisticated cyber campaign that targeted banking infrastructure.
This embedded hardware, equipped with a 4G modem, facilitated remote access over mobile data, bypassing perimeter firewalls and establishing an outbound command-and-control (C2) channel via the TINYSHELL backdoor linked to a Dynamic DNS domain.
The setup allowed persistent external connectivity, enabling lateral movement across critical systems without triggering conventional defenses.
Investigators noted that this physical backdoor remained undetected in initial triage, highlighting gaps in traditional monitoring that overlook hardware-based intrusions.
Stealthy Physical Intrusion
Forensic analysis revealed the Raspberry Pi’s role in beaconing activity, with outbound connections occurring every 600 seconds to port 929, yet no corresponding process IDs (PIDs) appeared in standard listings.
To uncover this, responders deployed a custom script capturing socket connections at one-second intervals over 10 minutes, exposing hidden network behaviors during system idle states.
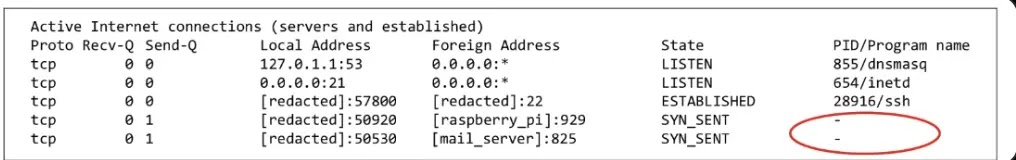
Memory dumps further identified masqueraded processes, including binaries named “lightdm” executed from /tmp and /var/snap/.snapd paths, mimicking the legitimate LightDM display manager with deceptive arguments like “–session child 11 19.”
These backdoors connected to both the Raspberry Pi and an internal Mail Server, leveraging an undocumented anti-forensics technique involving Linux bind mounts now cataloged as MITRE ATT&CK T1564.013 to obscure process visibility.
By mounting /proc/[pid] directories to tmpfs or external filesystems, the attackers evaded detection tools, rendering processes invisible in listings and defeating routine forensic triage.
Disruption of Fraudulent Objectives
The Network Monitoring Server served as a central pivot, granting UNC2891 broad internal access due to its connectivity across the data center.
Even after the Raspberry Pi’s removal, persistence was maintained via a backdoor on the Mail Server, which had direct internet exposure.
The group’s ultimate aim was to compromise the ATM switching server by deploying the CAKETAP rootkit, designed to manipulate Hardware Security Module (HSM) responses and spoof authorization messages for illicit cash withdrawals.
Fortunately, the operation was halted before completion, but the multi-pivot path combining physical hardware, network beaconing, and Dynamic DNS for IP agility underscored the campaign’s resilience against containment efforts.
Detection relied heavily on advanced techniques, as standard tools failed amid system sleep states and bind mount obfuscation.
Memory and network forensics proved essential, revealing anomalies like repeated connections without visible PIDs.
For defense, experts recommend monitoring mount and umount syscalls via auditd or eBPF, alerting on /proc/[pid] mounts to tmpfs, restricting executions from /tmp or .snapd paths, securing physical switch ports, and incorporating memory imaging in incident response.
This incident emphasizes that initial access blind spots, particularly physical vectors, demand integrated threat models blending logical and hardware security in banking environments, where rootkits exploiting Linux features like bind mounts can subvert established playbooks.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!
