North Korean state-backed hacking groups have stolen over $659 million worth of cryptocurrency in multiple crypto-heists, according to a joint statement issued by the United States, South Korea, and Japan on Tuesday.
The announcement also warns that threat groups linked to the Democratic People’s Republic of Korea (DPRK) are still actively targeting blockchain technology industry companies.
“As recently as September 2024, the United States government observed aggressive targeting of the cryptocurrency industry by the DPRK with well-disguised social engineering attacks that ultimately deploy malware, such as TraderTraitor, AppleJeus and others. The Republic of Korea and Japan have observed similar trends and tactics used by the DPRK,” the joint statement warns.
“The DPRK’s cyber program threatens our three countries and the broader international community and, in particular, poses a significant threat to the integrity and stability of the international financial system.”
It also officially confirmed that North Korean attackers were behind the July 2024 breach of WazirX, India’s largest Bitcoin exchange, which resulted in a $235 million loss.
North Korea was also linked to multiple other cryptocurrency heists disclosed last year, including DMM Bitcoin ($308 million), Upbit ($50 million), Rain Management ($16.13 million), and Radiant Capital ($50 million).
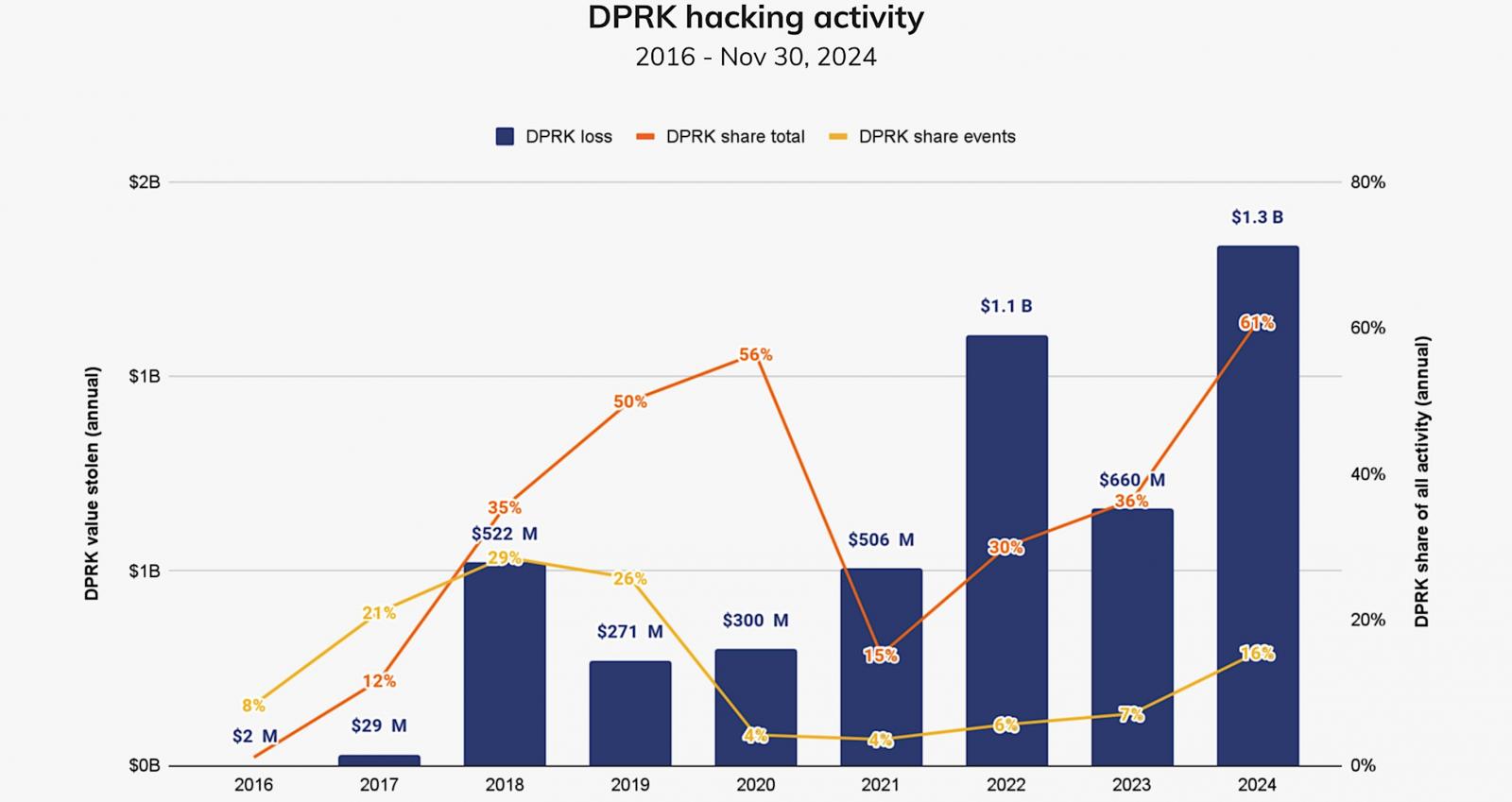
However, blockchain analysis company Chainalysis painted a more dire picture in a December report, saying North Korean hackers stole $1.34 billion worth of cryptocurrency in 47 cyberattacks last year, breaking their previous record of $1.1 billion from 2022.
“In 2023, North Korea-affiliated hackers stole approximately $660.50 million across 20 incidents; in 2024, this number increased to $1.34 billion stolen across 47 incidents — a 102.88% increase in value stolen,” Chainalysis said.
North Korea’s army of IT workers
In recent years and throughout 2024, United States, South Korean, and Japanese government agencies have also published alerts regarding North Koreans tricking private companies into hiring them as remote IT workers.
These North Korean IT workers, who refer to themselves as “IT warriors,” are impersonating U.S.-based IT staff by connecting to enterprise networks via U.S.-based laptop farms, something that the FBI has warned for years.
As it repeatedly cautioned, North Korea maintains a large army of IT workers who have been trained to conceal their true identities to secure employment at hundreds of companies across the United States and worldwide.
For instance, cybersecurity company KnowBe4 has recently hired a North Korean malicious actor as a Principal Software Engineer after he passed background checks, verified references, and four video interviews with the help of a stolen identity and AI tools. However, once hired, the “IT warrior” immediately tried to install information-stealing malware on company-provided devices.
After being discovered and fired, some of these North Korean IT workers have also used insider knowledge and their coding skills to extort their former employers under the threat of leaking stolen sensitive information online.
The U.S. State Department now offers up to $5 million for information that could help disrupt the activities of North Korean front companies Yanbian Silverstar and Volasys Silverstar (and their employees). Over the last six years, these companies have generated over $88 million in illegal remote IT work schemes.
“The United States, Japan, and the Republic of Korea advise private sector entities, particularly in blockchain and freelance work industries, to thoroughly review these advisories and announcements to better inform cyber threat mitigation measures and mitigate the risk of inadvertently hiring DPRK IT workers,” the United States, South Korea, and Japan added in today’s joint statement.
