The National Institute of Standards and Technology (NIST) announced that ASCON is the winning bid for the “lightweight cryptography” program to find the best algorithm to protect small IoT (Internet of Things) devices with limited hardware resources.
Small IoT devices are becoming increasingly popular and omnipresent, used in wearable tech, “smart home” applications, etc. However, they are still used to store and handle sensitive personal information, such as health data, financial details, and more.
That said, implementing a standard for encrypting data is crucial in securing people’s data. However, the weak chips inside these devices call for an algorithm that can deliver robust encryption at very little computational power.
“The world is moving toward using small devices for lots of tasks ranging from sensing to identification to machine control, and because these small devices have limited resources, they need security that has a compact implementation,” stated Kerry McKay, a computer scientist at NIST.
“These algorithms should cover most devices that have these sorts of resource constraints.”
ASCON was selected as the best of the 57 proposals submitted to NIST, several rounds of security analysis by leading cryptographers, implementation and benchmarking results, and feedback received during workshops. The whole program lasted for four years, having started in 2019.
NIST says all ten finalists exhibited exceptional performance that surpassed the set standards without raising security concerns, making the final selection very hard.
ASCON was eventually picked as the winner for being flexible, encompassing seven families, energy efficient, speedy on weak hardware, and having low overhead for short messages.
NIST also considered that the algorithm had withstood the test of time, having been developed in 2014 by a team of cryptographers from Graz University of Technology, Infineon Technologies, Lamarr Security Research, and Radboud University, and winning the CAESAR cryptographic competition’s “lightweight encryption” category in 2019.
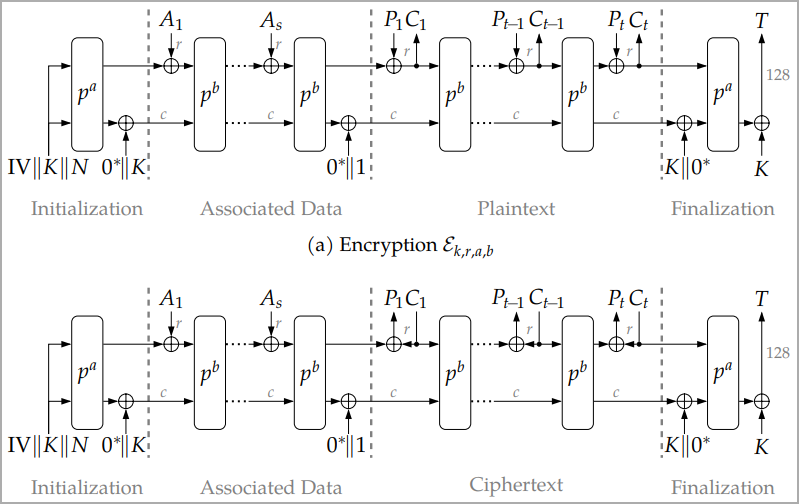
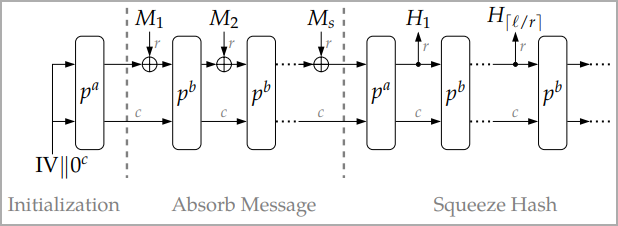
Two of ASCON’s native features highlighted in NIST’s announcement are AEAD (Authenticated Encryption with Associated Data) and hashing.
AEAD is an encryption mode that provides confidentiality and authenticity for transmitted or stored data, combining symmetric encryption and MAC (message authentication code) to prevent unauthorized access or tampering.
Hashing is a data integrity verification mechanism that creates a string of characters (hash) from unique inputs, allowing two data exchange points to validate that the encrypted message has not been tampered with.
NIST still recommends the AES technique for AEAD and SHA-256 for hashing; however, these are unsuitable for smaller, weaker devices.
Despite ASCON’s lightweight nature, NIST says the scheme is powerful enough to offer some resistance to attacks from powerful quantum computers at its standard 128-bit nonce. However, this is not the goal or purpose of this standard, and lightweight cryptography algorithms should only be used for protecting ephemeral secrets.
NIST treats post-quantum cryptography as a separate challenge, running a different program for developing quantum-resistant standards, and the effort has already yielded its first results.
For more details on ASCON, check the algorithm’s website, or read the technical paper submitted to NIST in May 2021.




