Shortly after the announcement of an alliance between the ‘UserSec’ and eight other hacker collectives, the pro-Russian hacker group expanded their list by adding one more group to it — Bear IT Army.
UserSec’s collaboration with Bear IT Army further expands the partnerships among Pro-Russian cybercriminals supporting the country in the ongoing war against Ukraine.
Since the outbreak of the war, pro-Russia hackers have continued to team up and target countries that are pro-Ukraine, especially NATO countries.
The international conflict has simultaneously triggered a cyberwar, where hackers aligned with each nation have persistently sought to undermine the other through cyber attacks.
UserSec’s collaboration with Bear IT Army marks yet another teaming of cybercriminals besides Anonymous Sudan and Killnet.
UserSec’s collaboration with Bear IT Army and pro-Russian groups
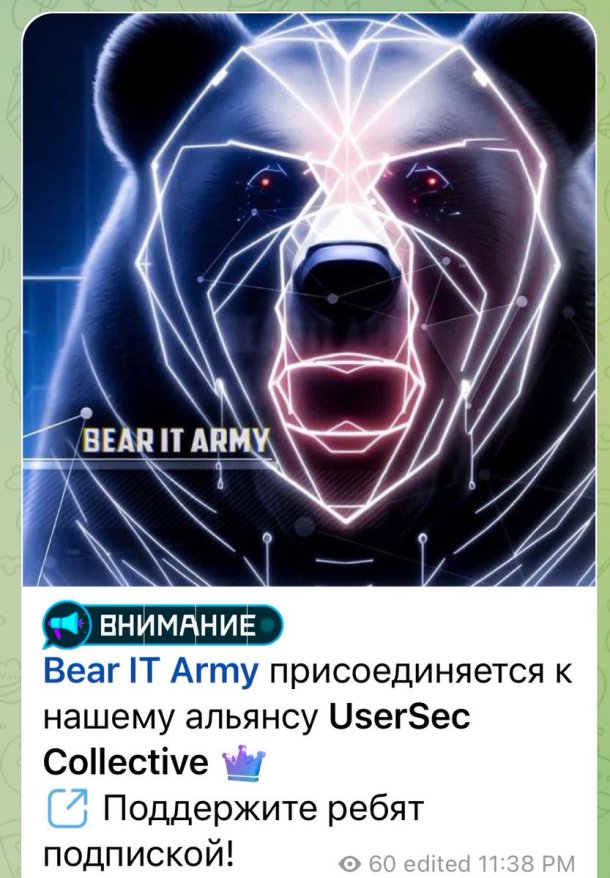
With UserSec’s collaboration with Bear IT Army, it becomes imperative for targeted nations to increase security and trace the culprits grouping against them.
Not much is known about the cybercriminal group Bear IT Army. However, the NoName Group uses the Bear image and similarly targets European nations’ websites.

UserSec’s collaboration with Bear IT Army is the latest in the list of geopolitical hacker collaborations spotted in the recent months. Apart from Russia, hacker groups from India and Egypt were spotted doing so recently.
UserSec itself last week announced a collaboration with pro-Russian ATPs from several other nations, listing the Romanian medical sector as their joint target.
“This (effort) aligns with their previous announcement last month when UserSec targeted NATO member states following the Russian invasion of Ukraine,” The Cyber Express reported then.
“The group specifically targeted Western governments and organizations that offered Ukraine strategic and military support.”
KillNet, probably the most popular among the pro-Russian hacker groups, joined hands with UserSec in its cyber attacks targeting NATO nations.
KillNet has also gone ahead and announced that it will offer hacking services to state-sponsored entities and private organizations.
All this was linked to NATO’s Secretary General visiting Ukraine, which likely spurred the desire of the hackers to invade NATO nations’ websites.
UserSec’s collaboration with Bear IT Army and its background
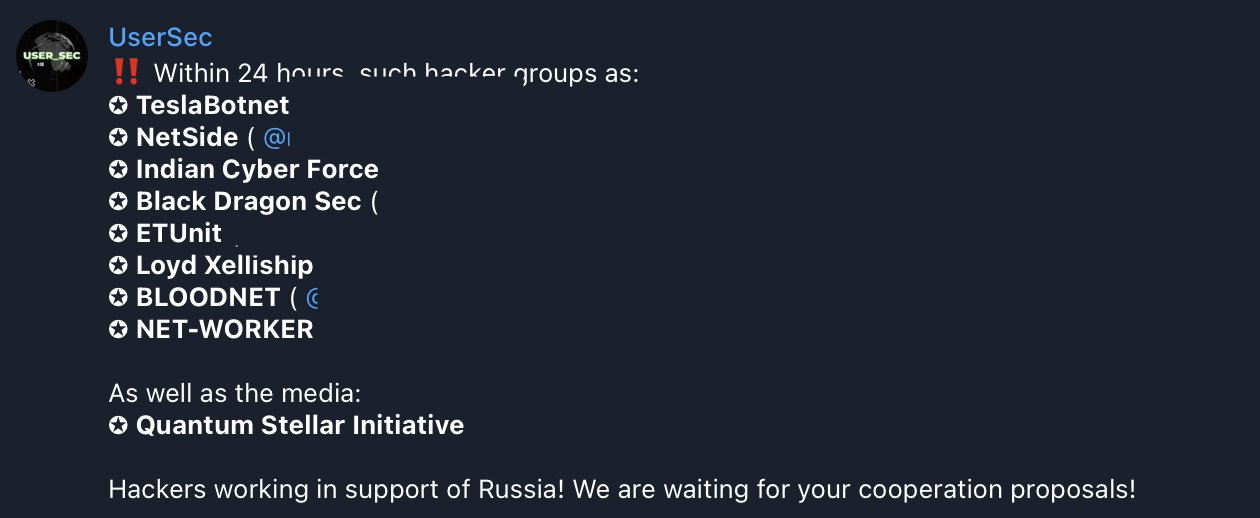
Recently, UserSec claimed to collaborate with eight hacker groups. These included TeslaBotnet, NetSide, Indian Cyber Force, among others. However, the authenticity of the claim could not be confirmed.
UserSec and other hacker’s cyber attacks against Ukraine
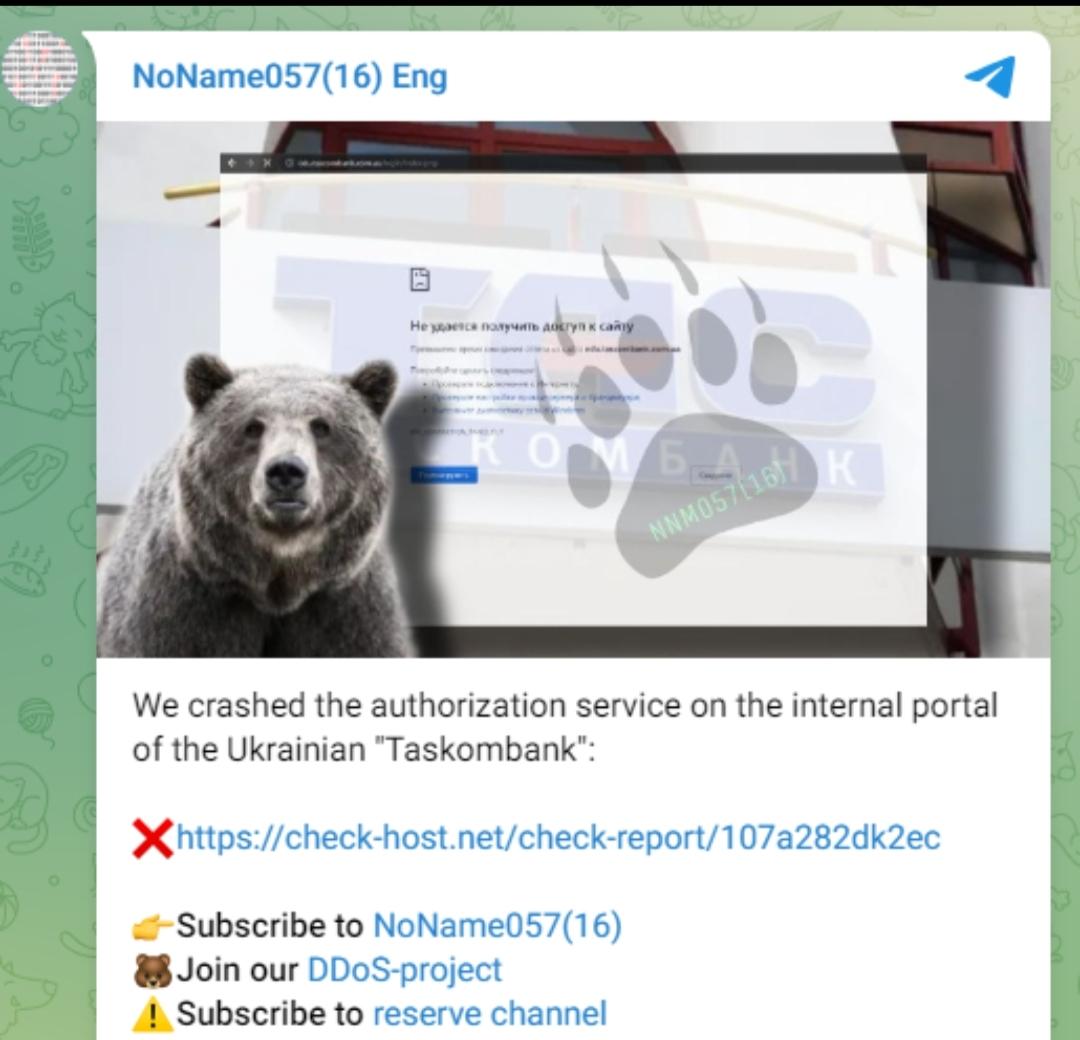
According to threat intelligence service Falcon Feeds, NoName hackers have also launched a cyber attacks on the Ukrainian financial sector recently.
Another group called Kromsec exploited a vulnerability to steal information from the French Ministry of Justice, while UserSec targeted Stockholm’s Arlanda Airport.
Meanwhile, a British man named Joseph James O’Connor was held on account of hacking the Twitter accounts of several celebrities and politicians in 2020.
He was arrested in Spain and sentenced this week to five years in prison. It is essential to not just nab cyber criminals but also deter them from turning back to cybercrime so the network of hackers is weakened.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
