Check Point Research (CPR) has published a comprehensive analysis of ValleyRAT, a widely distributed backdoor also known as Winos/Winos4.0, revealing its sophisticated modular architecture and dangerous kernel-mode rootkit capabilities.
The research demonstrates how the malware’s developers possess deep expertise in Windows internals and successfully bypass modern security protections on fully updated Windows 11 systems.
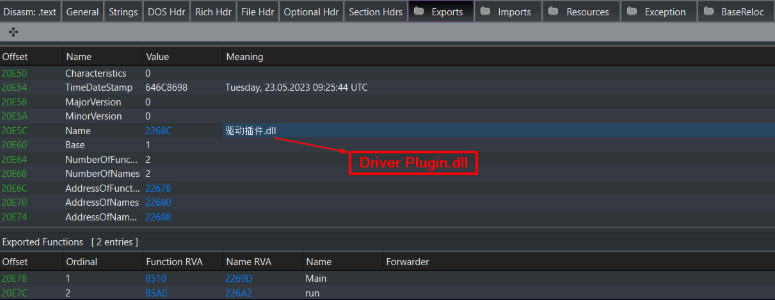
The most alarming discovery involves ValleyRAT’s “Driver Plugin,” which embeds a kernel-mode rootkit signed with valid but expired certificates.
Despite the certificate’s age valid only between 2013 and 2014 the driver qualifies under Microsoft’s legacy driver signing policy exceptions, allowing it to load on Windows 11 systems even with all protection features enabled, including Hypervisor-protected Code Integrity (HVCI) and Secure Boot.
The rootkit driver retains its original Program Database (PDB) path and compilation timestamp from April 23, 2023, suggesting the developers leveraged and modified the publicly available “Hidden” rootkit project.
Check Point’s differential analysis identified approximately 25 new functions added to the original codebase, including critical capabilities for stealthy deployment and lateral movement.
Sophisticated Installation
ValleyRAT implements two driver installation modes. The normal mode drops the embedded driver to disk and registers it as a kernel service named “kernelquick.”
The “Driver Plugin” is a DLL that acts as a user‑mode client for an embedded rootkit driver. Its original filename can be recovered from the Export Directory.
More concerning is the “Stealth Mode,” which employs MalSeclogon-based impersonation and parent process ID (PPID) spoofing to execute installation commands under the Desktop Window Manager (dwm.exe) context, significantly reducing behavioral detection signals.
The rootkit driver introduces advanced functionality to maintain persistence and evade detection.
The newly added UMInjection() function enables kernel-mode to user-mode APC-based shellcode injection, while ForceDeleteFile() implements kernel-level forced deletion of arbitrary files including antivirus and endpoint detection and response (EDR) drivers.
Additionally, the SetDriverStartType_SystemStart() function elevates persistence by switching the service start type to system startup, ensuring the rootkit loads during boot.
Check Point’s detection analysis reveals approximately 6,000 ValleyRAT-related samples detected between November 2024 and November 2025, with a striking 85 percent appearing within the last six months.
This surge correlates directly with the public release of the ValleyRAT builder in March 2025, found on GitHub repositories containing both the C2 panel and development structure, including Visual Studio solutions.
Among detected samples, researchers identified 30 distinct builder variants and 12 rootkit driver variants, with the majority compiled in 2025.
Seven drivers remained signed with valid, non-revoked certificates despite originating from before 2015, further emphasizing the gap in current driver blocklists and detection capabilities.
Modular Backdoor Capabilities
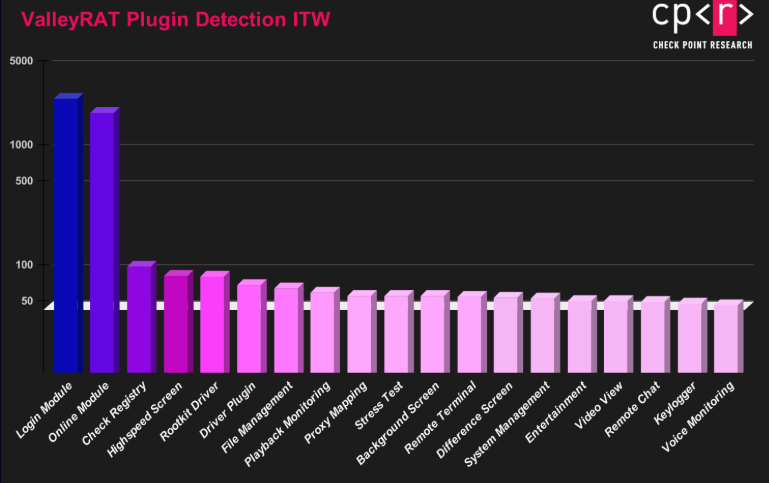
Beyond the rootkit, ValleyRAT’s 19 main plugins provide extensive backdoor functionality: system reconnaissance, file management, remote command execution, screen capture, audio and video surveillance, keystroke logging, and network traffic proxying.
The analysis also identified 24 auxiliary plugins designed for credential theft, privilege escalation, persistence, and data exfiltration targeting Chinese applications including WeChat, QQ, and Telegram.
The public availability of both the builder and alleged source code complicates traditional attribution methods.
While ValleyRAT has historically been linked to Chinese-speaking threat actors such as Silver Fox, the current landscape makes such attribution unreliable. Anyone can now compile, modify, and deploy ValleyRAT independently, blurring previous indicators.
Check Point responsibly disclosed their findings to Microsoft’s Security Intelligence team, highlighting real-world security gaps in Windows driver signing policies.
The research underscores that ValleyRAT has transitioned from an actor-linked threat to an openly available malware framework with accelerating adoption in the wild.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
