Chris Holt, Senior Bug Bounty Operations Lead at Verizon Media is a Paranoid. The Paranoids, as the Verizon Media security team is known, exist to protect consumer, customer, and corporate data, and to fight for their users and for the targeted, abused, and vulnerable.
When the properties you look after, which collectively serve over 1 billion people, include Yahoo!, AOL, and TechCrunch, this is a big job. Chris shares how The Paranoids have come to view hackers as partners in their fight for users. Read on to learn more about how Chris and his team run their bug bounty program, including how their program helps strengthen their entire SDLC.
Bus In, Bugs Out
This hacker-powered security touch point begins when the Security Analysts at HackerOne validate a report submitted by a hacker and submit it as a triaged vulnerability to The Paranoids (see Figure 1). The team then decides who needs to get involved in each bug. Sometimes that’s the developers, sometimes other groups may be needed, like the incident response team. Most bugs only need the development team’s attention.
Business as Usual (BAU) diagram of bug bounty ops at Verizon Media
The developers address vulnerabilities within acceptable risk management practices. But they also assist in updating proactive security tools, processes, and templates to harden surfaces further.
Bug Bounty Lifecycle
The Paranoids use the outside perspective they gain from the hacker community to strengthen their entire SDLC.
Starting with the traditional SDLC (Figure 2), The Paranoids flip it around — using bugs to drive deeper and wider improvements.
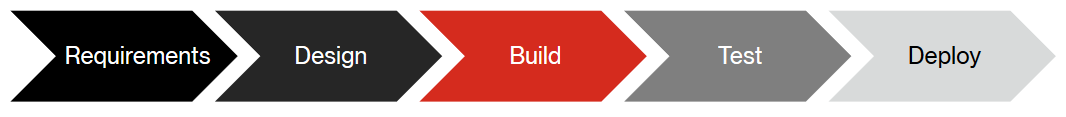

Starting from the right, a typical bug gives you a payload that executes in production, so they will Deploy a small fix.
But why stop there? The team will frequently implement a tool and add it as a new Test case.
Over time, as more bugs of a particular type come in, The Paranoids work with development to Build a new library into the codebase.
There may be an opportunity to work with the Architecture team to Design a new control.
Finally, The Paranoids sometimes take the lessons learned from a class of vulnerability and write Requirements, policies or standards to address it.
Community Above All
Verizon Media uses Live Hacking events as a sharp tool to focus testing on a specific product, feature or security control.
Hackers can use them to build up their network and Verizon Media also uses these events to train new hackers and recruit hackers onto their security team.
At the h1-5411 live hacking event in Buenos Aires, Verizon Media invited welcome dozens of top hackers from the global community, over 20 from the local community, and golden tickets for EkoParty conference attendees who solved a CTF challenge.
Participants in h1-5411 Live Hacking Event in Buenos Aires
Wrap-up: Verizon Media’s Keys to Bug Bounty Success
Verizon Media’s bug bounty program success starts by recognizing the central importance of their team’s purpose – fighting for users (See Figure 4).
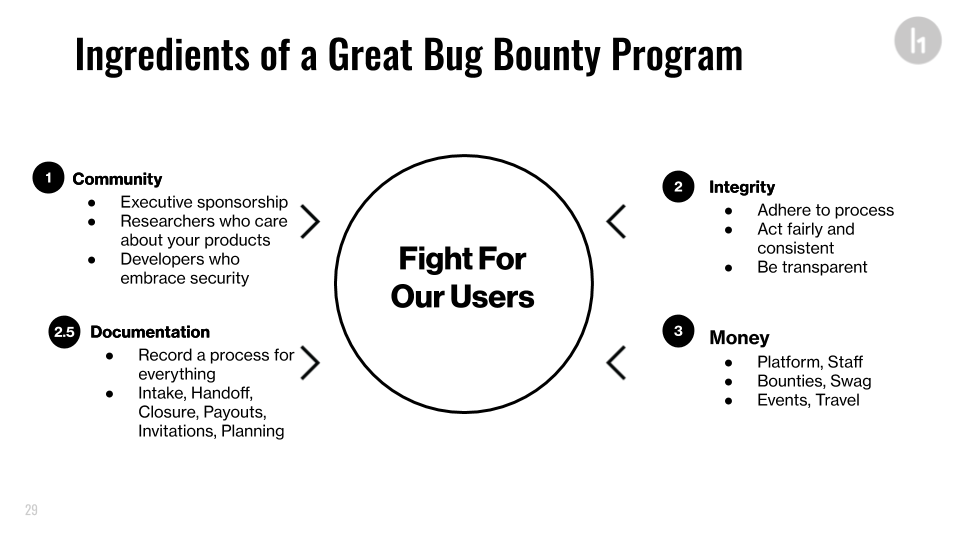
From there, you need a strategic approach to community building and gaining buy-in from executives and your colleagues. When the bugs start rolling in, what do you do with them? Whomever is responsible for fixing bugs has to be willing to accept bugs from your program.
Next comes Integrity. To build a sustainable hacker community, Chris shared, the program must treat its security page as a contract. If you say you’ll pay $x for a certain type of bug, you have to do it and exceptions must be rare and very well-explained.
But integrity is also more than this for Verizon Media. It also means being as transparent as possible with hackers. Sometimes they will ask questions that you can’t fully answer without divulging confidential or privileged information. When it happens – and it will – simply tell the hacker that you can’t answer because to do so would require sharing confidential info. Honesty and transparency go a long way.
Documentation to ensure consistent approaches to bounty operations is also a key to success. You won’t need it all at once, but ultimately you’ll need docs for: How to accept bug submissions. Who gets notified of a bug and when. The process for handing bugs off to developers. What information do you need to request from the hacker Does your team add anything else to that? When is a bug “fixed”? How do you track all of these reports that come in? (Editor’s note: The HackerOne Bug Bounty Field Manual covers all this, and more!)
As The Paranoids have internalized these best practices, they’ve benefitted from a hacker community that works as an extension of their team. Building the community (with hackers and across the various groups internally) gives Chris the confidence to know that when the hackers break something – and whatever you point them at, they will break – that it breaks cleanly. “Like cracking an egg into a bowl and not on the floor.”
Verizon Media’s partnership with HackerOne is about much more than “bugs in, bugs out”. The insight they gain from hackers is put to use across their entire SDLC to ensure they continue earning the trust of their 1 billion users. Anyone looking to take their bounty program to the next level can learn a lot from the best practices Chris shares in this webinar.
You can give this lively, 30-minute webinar recording a listen here.




