VirusTotal has discovered a phishing campaign hidden in SVG files that create convincing portals impersonating Colombia’s judicial system that deliver malware.
VirusTotal detected this campaign after it added support for SVGs to its AI Code Insight platform.
VirusTotal’s AI Code Insight feature analyzes uploaded file samples using machine learning to generate summaries of suspicious or malicious behavior found in the files.
After adding support for SVGs, VirusTotal found an SVG file that had zero detections by antivirus scans, but whose AI-powered Code Insight feature detected using JavaScript to display HTML, impersonating a portal for Colombia’s government judiciary system.
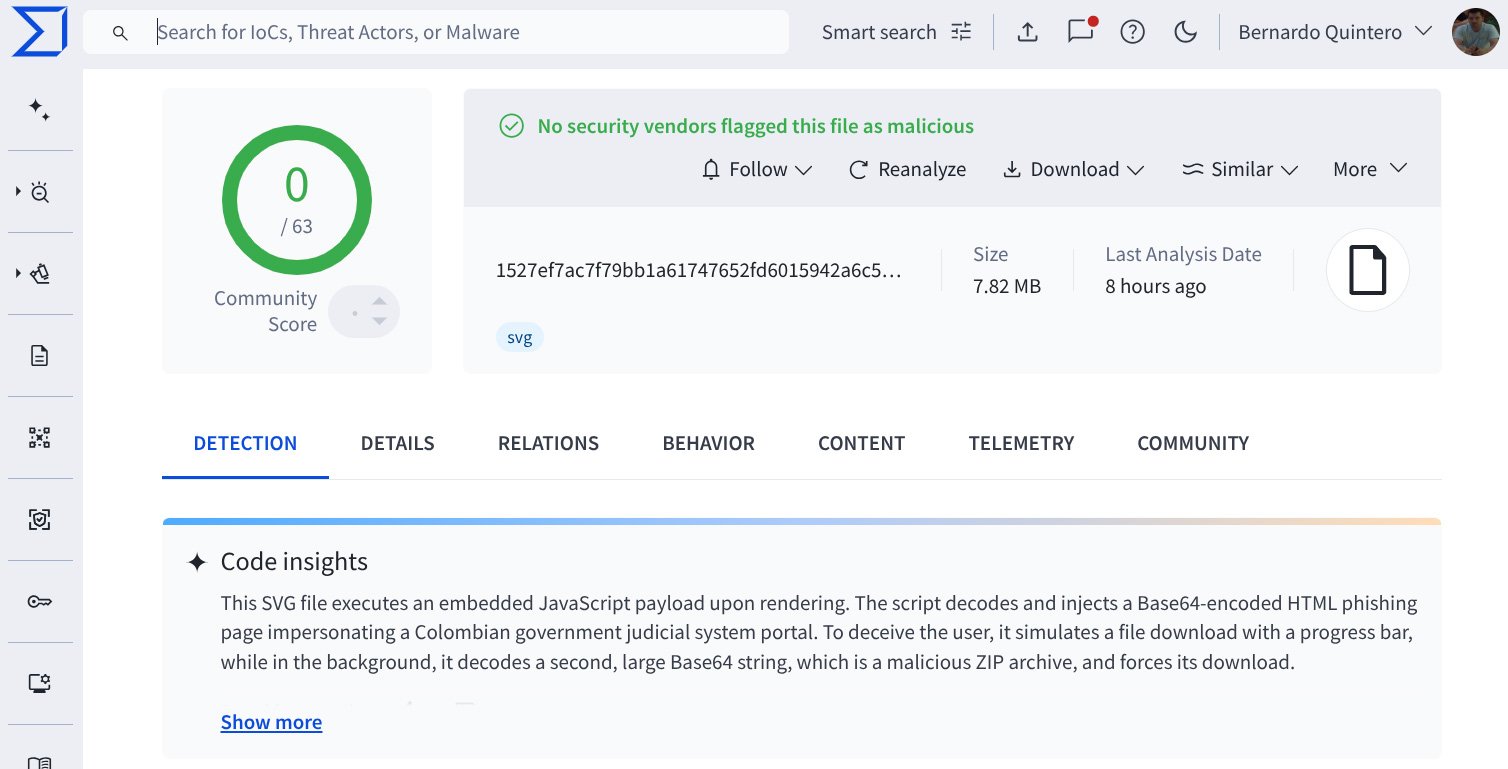
Source: VirusTotal
SVG, or Scalable Vector Graphics, is used to generate images of lines, shapes, and text through textual mathematical formulas in the file.
However, threat actors have begun increasingly using SVG files in attacks, as they can also be used to display HTML using the
In the campaign discovered by Virustotal, SVG image files are used to render fake portals that display a phony download progress bar, ultimately prompting the user to download a password-protected zip archive [VirusTotal]. The password for this file is displayed in the fake portal page.
“As shown in the screenshots below, the fake portal is rendered exactly as described, simulating an official government document download process,” explains VirusTotal.
“The phishing site includes case numbers, security tokens, and visual cues to build trust, all of it crafted within an SVG file.”
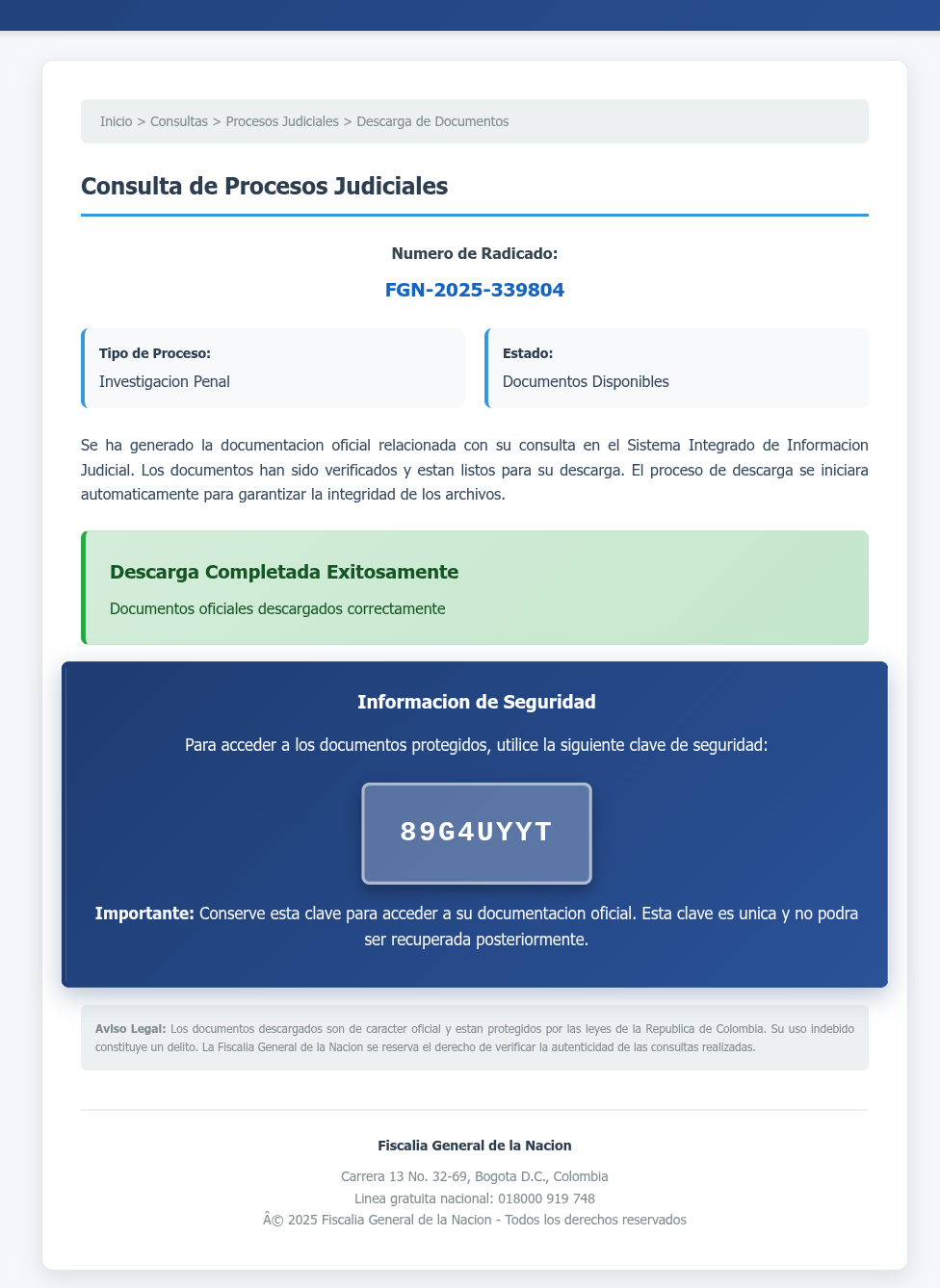
Source: VirusTotal
BleepingComputer found that the extracted file contains four files: a legitimate executable from the Comodo Dragon web browser, renamed to be an official judicial document, a malicious DLL [VirusTotal], and what appears to be two encrypted files.
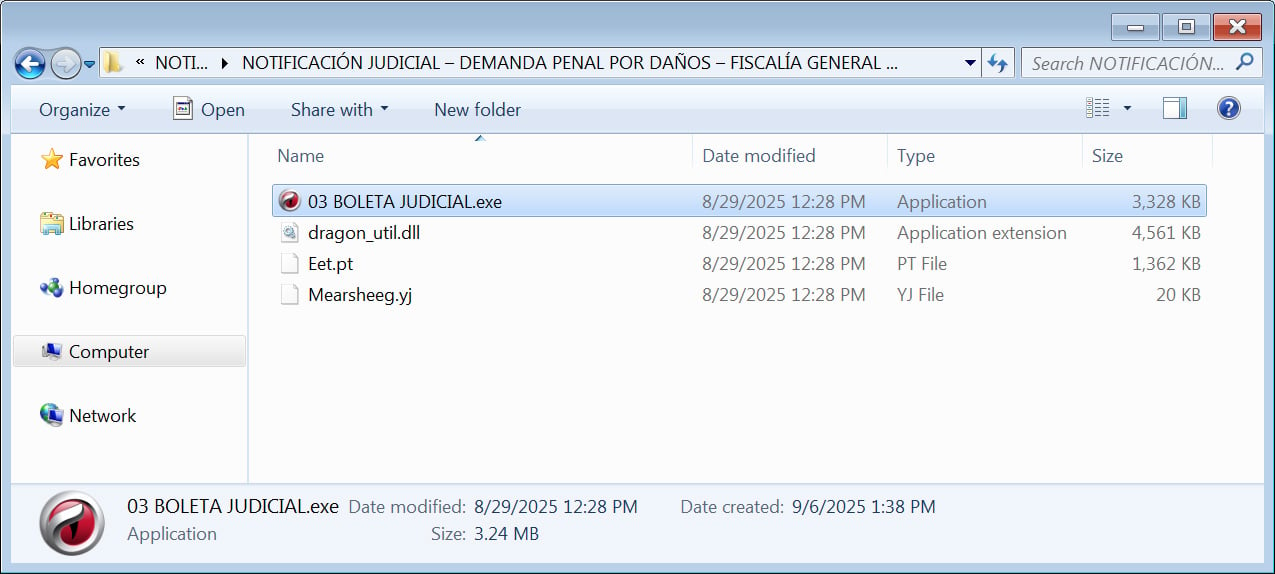
Source: BleepingComputer
If the user opens the executable, the malicious DLL will be sideloaded to install further malware on the system.
After detecting this initial SVG, VirusTotal identified 523 previously uploaded SVG files that were part of the same campaign but had evaded detection by security software.
The addition of SVG support to AI Code Insights was crucial in exposing this particular campaign, as VirusTotal noted that the use of AI makes it easier to identify new malicious campaigns.
“This is where Code Insight helps most: giving context, saving time, and helping focus on what really matters. It’s not magic, and it won’t replace expert analysis, but it’s one more tool to cut through the noise and get to the point faster,” concludes VirusTotal.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
